
Using the Kemp LoadMaster as a Reverse Proxy
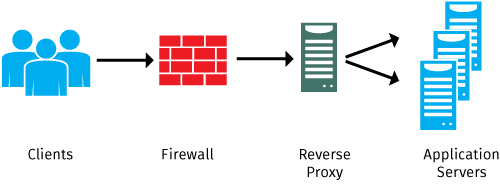
Reverse Proxy
The term reverse proxy is normally applied to a service that sits in from of one or more servers (such as a webserver), accepting requests from clients for resources located on the server(s). From the client point of view, the reverse proxy appears to be the web server and so is totally transparent to the remote user.
Kemp’s LoadMaster™ provides a perfect platform to deliver highly available reverse proxy services for a wide range of workloads and to enhance service delivery with features such as advanced load balancing, SSL offloading and an integrated web application firewall.
Resources and Related Content
- Microsoft TMG Replacement
- Building Scalable Communications Platform with Microsoft Lync & Kemp- Case Study
- MVP Erdal Ozkaya talks about Lync, Exchange and Load Balancing
As all client requests pass through the proxy, it is a perfect point in a network to control traffic while also optimizing performance with compression, encryption offloading and caching. As a single point of connection to services, reverse proxies are normally deployed in a highly available configuration to maximize application and service uptime.
Controlling Network Traffic
A reverse proxy solution will usually include the capability to forward traffic to multiple servers and to balance the traffic between these servers (load balancing). Being able to forward traffic to more than one server opens up many ways to improve service uptime, as application resilience can be implemented by deploying more than one server. The reverse proxy would then balance web traffic between the servers using a basic scheme such as round-robin or something more advanced, such as server health and capacity checking. It is this feature of a reverse proxy that allows web services to scale as more web servers can be added (and removed) as demand changes without any change to the Internet-facing part of the service.
Securing the Web Server Infrastructure
Being the chokepoint for all traffic from the internet, a web proxy is also the perfect place in the network to secure the backend server infrastructure. At the most basic level, the proxy rewrites URLs so that the underlying infrastructure is not exposed to the client. At a more advanced level, the proxy may enforce encryption on all traffic and also inspect traffic for suspicious activities using a Web Application Firewall (WAF). The WAF feature allows the proxy to identify and mitigate against known vulnerabilities and exploits preventing such attacks from ever reaching the servers.
Encryption Offload in a Reverse Proxy
A reverse proxy will generally need to look inside web traffic so that it can perform operations such as caching and content security. This means that the proxy will act as the endpoint from SSL encrypted connections rather than the webservers. This approach removes the CPU overhead of establishing secure connections from the server and also simplifies the management of encryption keys and certificates. The proxy can also use specialist hardware to process this security workload and also to secure private keys in accordance with standards such as FIPS-140-2.
Improving Performance with Content Caching
A reverse proxy may also cache content locally so that not all client requests need to be forwarded to a server. This can significantly reduce the server workload as frequently requested items such as brand images are served directly from the proxy cache. This also improves the client quality of experience as cached content is delivered without having to access back-end resources.
More Than Just Web Traffic
Reverse proxies can be used for more than just web applications. Services such as Microsoft Lync require a reverse proxy to allow external subscribers access services. Again, a proxy enhances the security and performance of such applications by offloading security processing and hiding the internal infrastructure topology from the Internet.
