
Reverse Proxy Solutions for Performance, Security & Scalability
Optimize traffic, secure applications, and ensure high availability with an enterprise-grade reverse proxy
Product Comparison Free TrialProgress Kemp LoadMaster™ leads the way in reverse proxy solutions, providing intelligent traffic management, security, and performance optimization for your applications. With a full suite of features including load balancing, SSL offloading, and Web Application Firewall (WAF), LoadMaster ensures reliable, secure, and high-performance application delivery.
Reverse Proxy
The term reverse proxy (see: Load Balancer) is normally applied to a service that sits in front of one or more servers (such as a webserver), accepting requests from clients for resources located on the server(s). From the client point of view, the reverse proxy appears to be the web server and so is totally transparent to the remote user.
Kemp LoadMaster™ provides a perfect platform to deliver highly available reverse proxy services for a wide range of workloads and to enhance service delivery with features such as advanced load balancing, SSL offloading and an integrated web application firewall.
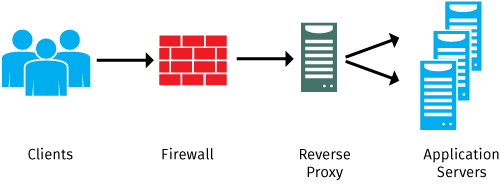
As all client requests pass through the proxy, it is a perfect point in a network to control traffic while also optimizing performance with compression, encryption offloading and caching. As a single point of connection to services, reverse proxies are normally deployed in a highly available configuration to maximize application and service uptime.
Key Features of Our Reverse Proxy Solution
1. Controlling Network Traffic with Intelligent Load Balancing
Our reverse proxy solution optimizes network traffic to prevent server overload, ensure high availability, and improve performance. It dynamically distributes requests across multiple backend servers, maintaining seamless operations—even under heavy demand.
How It Works
- Distributes traffic efficiently across multiple servers to prevent congestion
- Enhances uptime by detecting server failures and rerouting requests automatically
- Scales dynamically by adding or removing servers without downtime
- Supports Layer 4 proxying, unlike Microsoft Application Request Routing (ARR), which only works with HTTP/HTTPS
A reverse proxy solution typically includes the capability to forward traffic to multiple servers and balance the load efficiently. Load balancing methods such as round-robin, least connections, and server health checks ensure that requests are intelligently routed based on real-time server conditions. If a server fails or reaches capacity, traffic is automatically redirected to a healthy server, preventing downtime and performance degradation.
Unlike some solutions, LoadMaster can proxy any application at Layer 4, making it ideal for businesses that need flexible traffic management beyond just web-based applications. Competing solutions, like Microsoft Application Request Routing (ARR), are limited to HTTP and HTTPS traffic, restricting their ability to manage diverse workloads.
For businesses experiencing fluctuating traffic, our solution scales seamlessly, allowing servers to be added or removed without affecting the end-user experience.
2. Securing Web Server Infrastructure
Our reverse proxy acts as a security gateway, preventing direct exposure of backend servers while filtering malicious traffic and enforcing security policies.
How It Works:
- Acts as the chokepoint for all internet traffic before it reaches backend servers
- Hides backend infrastructure by rewriting URLs and masking internal server details
- Blocks suspicious traffic with a Web Application Firewall (WAF)
- Enforces encryption to protect sensitive data in transit
As the chokepoint for all incoming traffic, our reverse proxy ensures that only secure, authorized requests reach backend infrastructure. Instead of exposing internal server details, it rewrites URLs so that backend services remain hidden from external users.
Our integrated Web Application Firewall (WAF) provides advanced security measures, blocking threats before they reach application servers. This ensures protection against SQL injection, cross-site scripting (XSS), and other cyber threats. TLS encryption further guarantees secure data transmission, reducing the risk of man-in-the-middle attacks.
3. SSL Offloading & Traffic Encryption
Our reverse proxy solution offloads SSL/TLS encryption from backend servers, improving performance while simplifying certificate management.
How It Works:
- Handles SSL encryption at the proxy level, freeing up backend resources
- Centralizes SSL certificate management for easier updates and maintenance
- Ensures compliance with security standards such as FIPS-140-2
Instead of requiring backend servers to manage encryption, our reverse proxy terminates SSL connections at the proxy layer. This eliminates CPU strain on backend servers while simplifying certificate management and renewal. Additionally, specialized hardware can be used to enhance encryption processing speed and protect private keys in compliance with regulatory standards.
For organizations handling sensitive data, our solution supports FIPS-140-2 compliance, providing an additional layer of protection for encryption keys.
4. More Than Just Web Traffic: Proxying Enterprise Applications
Our reverse proxy solution extends beyond web services, providing secure access and performance enhancements for enterprise applications.
How It Works:
- Supports non-web services such as Microsoft Skype for Business
- Enhances security by preventing direct exposure of internal infrastructure
- Improves performance by handling security processing externally
Many enterprise applications require external access to internal services. A reverse proxy enables this by acting as a secure gateway, ensuring that internal systems remain protected while still being accessible when needed.
For example, services like Microsoft Skype for Business rely on a reverse proxy to manage external traffic securely. By preventing direct connections, our solution reduces security risks while maintaining seamless application performance.
5. Performance Optimization with Content Caching
Our reverse proxy solution improves website performance by caching frequently accessed content, reducing the number of requests sent to backend servers.
How It Works:
- Caches static assets like images, scripts, and stylesheets for faster delivery
- Reduces redundant server requests, decreasing backend workload
- Enhances the user experience by lowering latency and improving load times
Instead of forwarding every request to backend servers, our reverse proxy stores and serves cached content when applicable. This allows frequently requested elements—such as logos, scripts, and images—to be delivered directly from the proxy without additional processing.
By reducing the load on backend servers, our solution increases scalability, making it ideal for high-traffic environments.
Resources and Related Content
Load Balancer
- What is a load balancer?
- Load Balancer
- Load Balancing HTTP/2
- Load Balancing Business Applications
- Load Balancing Techniques and Algorithms
- Load Balancers for Education
- Apache Load Balancing
- Network Load Balancer
- Application Server Load Balancer
- HTTP Load Balancer
- Reverse Proxy
- RDS Services
- Global server load balancing
