
Layer 7 Load Balancing
The Open Systems Interconnection (OSI) Reference Model for networking outlines the various layers where load balancing can be performed. Ostensibly, these are Layer 7 (Application) and Layer 4 (Transport) as shown in Figure 1 below.
What is Layer 7 Load Balancing?
A Layer 7 load balancer operates at the highest level applicable and provides for deeper context on the Application Layer protocols such as HTTP. Operating at the Application Layer, a Layer 7 Load Balancer can use this additional application awareness to make more complex and informed load balancing decisions based on the content of the message, to apply optimizations and changes to the content (such as HTTP header manipulation, compression and encryption) and ensure reliability and availability by monitoring the health of applications.
As shown in the Open System Interconnection (OSI) Model, Load Balancing at the Application Layer (Layer 7) is this highest level applicable and provides for deeper context on the Application Layer protocols such as HTTP. Operating at the Application Layer, a Layer 7 Load Balancer can use this additional application awareness to make more complex and informed load balancing decisions based on the content of the message, to apply optimizations and changes to the content (such as HTTP header manipulation, compression and encryption) and ensure reliability and availability by monitoring the health of applications.
A Layer 7 Load Balancer is also referred to as a reverse proxy.
Layer 7 vs Layer 4 Load Balancing
Layer 4 load balancers operate at the Transport layer e.g. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). Typically, the routing decisions at Layer 4 are based on source/ destination IP / Port without further packet inspection. A Layer 4 load balancer is not inspecting the message contents and unable to provide smarter application layer routing decisions and to apply optimizations and change the message content.
Learn more about Layer 4 load balancing.
Whilst we refer to Layer 7 Load Balancing for ease-of-reference, HTTP combines functions from Open System Interconnection (OSI) Layers 5, 6 and 7; which the Kemp Technologies Layer 7 Load Balancer leverages for enhanced functionality.
Requests received by the Load Balancer are typically distributed to an application based on a configured algorithm. Kemp Technologies provides the following load balancing algorithms:
- Round Robin
- Weighted Round Robin
- Least Connection
- Weighted Least Connection
- Adaptive
- SDN Adaptive
- Fixed Weighting
- Weighted Response Time
- Source IP Hash
- URL Hash
Learn more about load balancing algorithms.
Layer 7 Load Balancing Features
Persistence
Persistence enables all request from an individual client to be sent to the same server to that application context can be maintained. Persistence is also referred to as “affinity”, “server affinity” or “server sticky”.
Kemp Technologies provides the following persistence methods:
- Source IP Address
- Super HTTP
- Super HTTP and Source IP
- Server Cookie
- Server Cookie or Source IP
- Active Cookie
- Active Cookie or Source IP
- Hash All Cookies
- Hash all Cookies or Source IP
- URL Hash
- HTTP Host Header
- Hash of HTTP Query
- Selected header
- SSL Session ID
- UDP Session Initiation Protocol (SIP)
Context Switching
Context switching allows the Load Balancer to direct traffic based on the content and context of the information in the request from the client.
Content Rewriting
Content Rewriting allows the Load Balancer to rewrite client requests and replies to support use cases on hiding internal URLs and supporting applications with hardcoded URLs.
Secure Socket Layer (SSL)
Layer 7 Load Balancers provide the ability to terminate SSL traffic. Handling SSL/TLS encryption for network packets is a resource intensive task. Doing this on the web servers and application servers that are there to serve client requests puts an additional overhead on servers that should be optimized for content delivery.
Kemp Technologies provides the following features:
- Decrypt and Re-Encrypt
- Full Certificate management incl.:
- Client certificates
- Importing and maintaining certificates
- OCSP Support
- SNI Support
- Full Cipher Suite management incl.:
- Default best practices to support A-rated Qualys scan
- Pre-configured cipher suites including FIPS, ECDSA_Default, ECDSA_BestPractices and more
- Ability to create and tailor your own cipher suite for your application
- Ability to apply this to both the data plane and to control and specify access to the LoadMaster
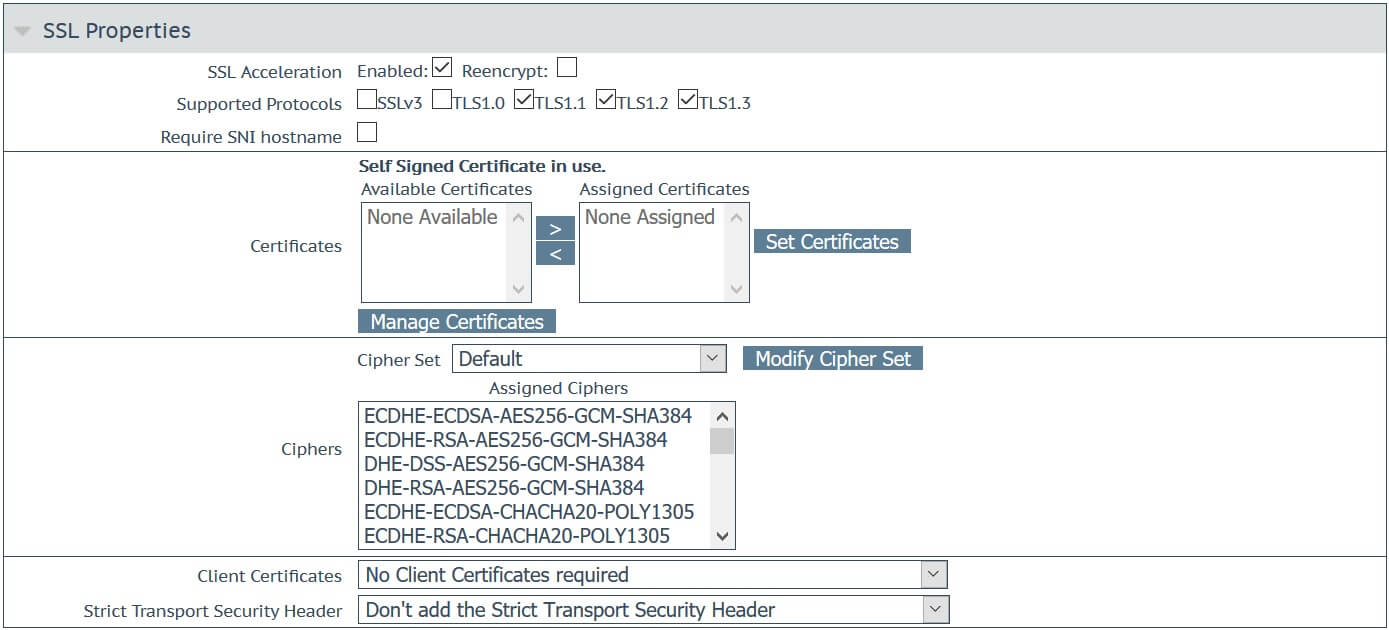 Figure 3: SSL Properties
Figure 3: SSL Properties
Health Checking
Health checking has evolved as a means for the Load Balancer to query the application server and application to determine that it is working correctly and available to receive traffic. The load balancing algorithm respects the results of the health check and only sends requests to application servers and applications that are available and can respond in a timely manner.
Logging & Monitoring
Due to its logical position on the network, a Layer 7 Load Balancer inspects all the Layer 4 and Layer 7 traffic flowing to and from websites and application servers. All this activity is recorded in the logs to aid monitoring and tracing with respect to networking information. These can be passed to dedicated monitoring tools for analysis, and any suspicious activity can be identified. Best practice says that the logs should be sent off from the network device that collects them and analyzed remotely.
An example of Layer 7 Load Balancing
Looking at an example, a user visits an online store with a virtual shopping cart. The online store is served by several application servers serving the content e.g. images of the items for sale and the virtual shopping cart. As the user browses the online store and puts items into the virtual shopping cart, the Layer 7 load balancer provides content rules to maximize public facing resources to local resources on the application server optimized for images, caching and compression of the image files to ease network congestion and persistence for the virtual shopping cart so that the user does not lose their purchases.
Layer 7 Load Balancing with Kemp
Kemp LoadMaster is an advanced and award winning Layer 4- 7 load balancer offering high performance hardware/virtual/cloud and bare metal options to suit customer needs and includes core functions like Server and Application health monitoring, SSL acceleration with FIPS 140-2 support, Caching/Compression, TCP Multiplexing, an automation-enabled API and more.
To gain an even greater level of understanding about layer 7, why not deploy a trial license today and configure layer 7 virtual services.
Load Balancer
- What is a load balancer?
- Load Balancer
- Load Balancing HTTP/2
- Load Balancing Business Applications
- Load Balancing Techniques and Algorithms
- Load Balancers for Education
- Apache Load Balancing
- Network Load Balancer
- Application Server Load Balancer
- HTTP Load Balancer
- Reverse Proxy
- RDS Services
- Global server load balancing
