
LoadMaster - Powering the Internet of Things (IoT)
Start Free TrialThe Internet of Things (IoT) is changing everything. As industries, device manufacturers, and infrastructure operators get onboard and connect all their devices to the Internet, they soon discover that security and compliance are major challenges. The drive to make devices “smart” and connect them is an open invitation for cyber-criminals, nation-state actors, and hackers. Without security, hackers who find an entry point into one device can move laterally across a network and start probing the entire system until they find the real prize: a database or repository that contains sensitive customer or business data. As the IoT continues to evolve, these threats will continue to grow in ferocity and the potential impact they have on the economy, corporations, business transactions, individual privacy, and safety.
It seems that a day does not go by without one breach or another making the headlines. Two recent attacks garnered a lot of attention.
- The Distributed Denial of Service (DDoS) attack against the Internet infrastructure company Dyn. This virulent attack was spawned by the Mirai bot. This bot scours the web for IoT devices, and then tries to break into them using factory-default usernames and passwords. If the login succeeds, the bot uses the devices to attack specific online targets. This attack was accomplished by hacking IoT devices, such as CCTV video cameras and digital video recorders, that still had the default administrator credentials that came with the devices. Not only were the factory-configured usernames and passwords never changed, the firmware for these devices was sorely out of date. Although this might seem shocking, the sad fact is that these very same issues are common with home devices.
- Attack on Target Corporation’s point-of-sale terminals. Hackers attacking Target’s heating and cooling systems gained access to the company’s internal accounts and installed card skimming software on point-of-sale terminals that allowed them to steal 11 gigabytes of sensitive information. As a result of the attack, Target was forced to inform about 110 million credit-card and debit-card shoppers, who made purchases at one of the company's stores during the attack, that their personal and financial information had been compromised.
The challenges associated with protecting large-scale IoT solutions using traditional security products are daunting, mainly due to the rigidity, poor elasticity, and cost. Traditional security products are rigid and inflexible because they are designed to resolve a specific problem and lack flexible customization, utility-oriented delivery, and granular consumption. Moreover, these solutions are not built to scale dynamically to respond to varying loads. Furthermore, the high cost of deploying a highly available firewall, VPN, and other intrusion prevention products makes traditional security solutions prohibitively expensive.
Kemp understands these challenges. Traditional application delivery controllers and purpose-built security products are simply not designed to protect IoT solutions. Kemp has taken the time to understand user needs and challenges thoroughly. From that research, Kemp has created a suite of virtual products that integrates multiple security and traffic management functions — including Web Application Firewall (WAF), load balancing, and VPN — into a virtual appliance.
Kemp Virtual Load Masters (VLM) abstract application delivery and security services from the physical infrastructure, and provides them as virtual services that can be attached to IoT workloads. Kemp VLMs can be dynamically provisioned to protect IoT devices and applications, deliver data confidentiality and integrity, and ensure true availability.
Consider the following advantages:
- Kemp VLMs protect IoT solutions from threats by including a WAF that controls access and prevents denial of service attacks.
- Kemp VLMs provide data integrity by authenticating devices or “things” that connect to the network, encrypting data and protecting private keys in hardware. By enabling SSL or IPSec encryption, IoT data can be protected during transfer from the enterprise edge to the cloud. With Kemp Edge Security Pack (ESP), IoT devices can be authenticated and authorized.
- To enhance reliability and availability, Kemp VLMs include L4-7 load balancing and GEO load balancing. These features ensure that IoT sessions are always handled by the most highly available server. In addition, Kemp 360 advanced monitoring and analytics engine visualizes changes in device behavior, so that remedial actions can be taken proactively based on real-time graphs before a catastrophic failure occurs.
1.1 IoT Architecture
To appreciate the benefits of the Kemp solutions, it is important to understand the IoT architecture. Most IoT solutions include endpoints, platforms, and business solutions (see Figure 1). IoT endpoints are a combination of real-world sensors and some form of hardware and/or software that detects or causes a change in the state (or “event”) of those sensors.
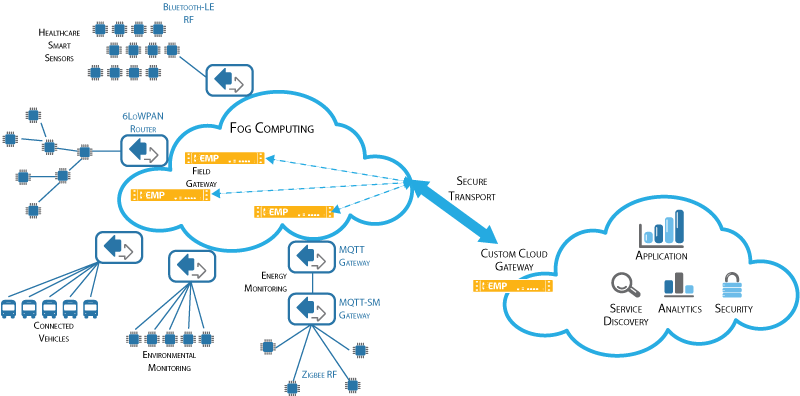
Figure 1. IoT Architecture
IoT platforms leverage gateways to monitor and manage IoT endpoints and their software, and to aggregate and analyze IoT endpoint data. An IoT gateway can be:
- A physical router, application delivery controller, or server with an IoT agent, or
- A virtual solution that resides in the cloud as a Platform as a Service (PaaS).
Whether physical or virtual, the goal of the IoT gateway is the same: to provide aggregated edge device management and connectivity. The IoT platform may have agents located on the IoT endpoints that connect either directly to the IoT back end or indirectly through IoT gateways.
IoT business applications use the data collected from sensors and endpoints to improve operational intelligence, produce better business outcomes, and improve the quality of life for businesses and consumers alike.
1 Powerful Solutions for Securing the IoT
1.1 Perimeter Security
The Pitfall
Enterprise IT professionals agree that securing the network only at the perimeter is inadequate for any solution, and particularly for IoT solutions. Modern attacks can exploit a perimeter-centric defense. Once the malware enters a data center by compromising one authorized sensor or by some other means, it can move easily from sensor to sensor within the data center.
The Solution
Kemp empowers IT teams to bring security closer to the IoT workloads and protect IoT data.
Kemp’s WAF combines Layer 7 Web Application Firewall protection with other application-delivery services that include intelligent load balancing, intrusion detection, intrusion prevention, and edge security and authentication. By integrating one of the world’s most deployed Open Source Web Application Firewall engines, ModSecurity, augmented by threat intelligence and research from information security provider Trustwave, Kemp WAF provides ongoing protection against known and evolving vulnerabilities in IoT solutions.
Kemp WAF is sufficiently robust to process and secure encrypted IoT traffic flows. Acting as a check on exfiltration of sensitive data such as personal health information, credit card data, and other sensitive information, WAF helps organizations satisfy PCI-DSS, HIPAA, and other stringent compliance requirements.
Kemp ESP provides multifactor authentication and fine-grained authorization. It can authenticate devices using certificates and the Online Certificate Status Protocol (OCSP) protocol before accessing IoT application servers, and restrict access to published applications using Active directory group membership information. It also supports RADIUS authentication and dual-factor authentication with RSA SecurID.
1.2 Lax Data Integrity and Protection
The Pitfall
IoT solutions provide huge and unprecedented amounts of sensitive personal information, such as addresses, birth dates, social security numbers, and more. There is great risk of abuse of this information by individuals, criminals, companies and governments. IoT data needs to be protected to avoid reputational damage and meet compliance requirements.
The Solution
To provide confidentiality and integrity of IoT data transferred from the data center edge to cloud gateways, Kemp LoadMasters implement IPsec VPN tunnels. IPsec is an industry standard and is offered as a secure connectivity option on cloud services from Microsoft, Amazon, and Google.
For organizations seeking to protect IoT application data, ensure confidentiality, and enforce data integrity, Kemp Application Delivery Controller (ADC) solutions provide high-performance SSL VPN termination and acceleration. The Kemp LoadMaster 8000 series include robust, high-end integrated SSL acceleration processors that can handle more than 45,000 SSL transactions per second (TPS) with 1K keys.
Kemp’s LoadMasters also support the use of network attached Hardware Security Modules (HSM) for enhanced protection of private key material required to support a TLS (SSL) handshake. It also executes cryptographic functions such as encryption (signing) and decryption.
1.3 Inability to Ensure Data Availability
The Pitfall
To cyber criminals, the plethora of devices that constitute the IoT is an open invitation for Distributed Denial of Service (DDoS) attacks. Attackers can create massive botnets and use them to generate a deluge of data. Because these attacks come from so many different devices instead of from known bad Internet addresses, they are extremely difficult to defend.
The Solution
Kemp VLMs protect against DDoS attacks that hijack IoT devices and flood the network with spurious traffic until systems become congested and are rendered unavailable. By validating network connections and verifying protocol correctness (header, URL, HTTP version, method) while proxying connections, Kemp VLMs protect against SYN flood attacks, TCP reset attacks, ICMP attacks, UDP storm attacks, and many other application-layer attacks.
Kemp VLM’s high-performance L4/7 server load balancing distributes incoming IoT sessions to the most highly available application server. By steering traffic dynamically to cloud-based servers, Kemp VLMs prevent performance degradation during DDoS attacks and accelerate processing time. Additionally, integrating with SDN controllers allows KLMs to configure network bandwidth dynamically and steer network traffic to least loaded network paths. This translates into efficient load balancing, accelerated application delivery, and improved Quality of Experience (QoE) to end users.
Kemp VLMs operate as an active/hot-standby configuration, with stateful failover that delivers superior high-availability for mission—critical IoT solutions while removing single points of failure. With server hardware and application health checking, user requests go to the most “available” servers and applications.
To ensure optimum user experiences, Kemp Multi-Site GEO LoadMasters (GLM) are designed from the ground up to optimize and increase availability and continuity for IoT workloads across multiple datacenters and hybrid clouds. Kemp GLMs ensure that when a primary site goes down, traffic is diverted to the disaster recovery site automatically. In this way, clients connect to their fastest performing and geographically closest datacenter seamlessly.
2 Conclusion
Industry analysts agree that the proliferation of connected devices is disrupting IT organizations. The dramatic increase in the number of connected things is forcing IT organization to evolve and consider new architectures to address security, privacy, cost, simplicity, agility, and performance in one solution.
Kemp offers powerful, real-world solutions to address these issues (see Figure 2). Kemp VLMs secure IoT applications and devices against external threats using WAFs, secure data using VPNs, and ensure application availability and resiliency.
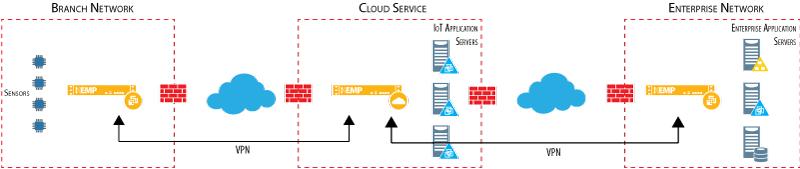
Figure 2. Defense in Depth Architecture
