What is Web Application Firewall (WAF)? Types & Benefits

Add a critical layer of security to your network by protecting applications from attack.
Did you know that over two thirds of web applications have critical security flaws? That is what Veracode found when it scanned 130,000 applications for vulnerabilities, finding some 68% had a flaw that fell into the OWASP Top 10.
The Commercial App Attack Surface
Extortion via ransomware or threats to publish sensitive data is a key motivator. Again, the size or type of the organization is not necessarily significant to make these attempts worthwhile.
What is a Web Application Firewall (WAF)?
“A Web Application Firewall (WAF) builds on and enhances traditional firewall security protection. Traditional firewalls don't stop encrypted HTTPS traffic as they have no visibility of the content within. A Web Application Firewall, which is logically placed between standard firewalls and web servers, operates at Layer 7 of the network stack. It can decrypt HTTPS web traffic and inspect the data content. In conjunction with lists of known attack methods, the Web Application Firewall can deny access to web servers when potentially malicious requests are detected,” the Progress/Kemp glossary explained.
What Are the Benefits of a Web Application Firewall?
- Defense for web applications - Businesses and other organizations depend on web applications for critical operations and customer engagement, making them prime targets for cyberattacks. WAFs act as a frontline defense, sitting directly in the web traffic path between endpoint devices and web application servers, looking for security issues in the traffic before it can reach the applications.
- Security that goes beyond traditional defenses – WAFs analyze how web traffic using HTTP/HTTPS protocols works and inspect these network packets to look for threats. This means that WAFs can prevent threat exploits that tools like network firewalls can’t detect. It’s worth repeating that WAFs do not replace traditional network firewalls. It augments them (and other security tools) by adding additional security inspections and checking network traffic in a different and complementary way.
What is the Difference Between a Web Application Firewall (WAF) and a Firewall?
Why Does a Web Application Need a Firewall?
As part of a layered security approach, a WAF can deliver logging and event information to external security and monitoring services. The WAF technology uses a set of rules that provide protection against a wide range of attacks – this set of rules has evolved over the years to provide coverage for new and emerging threats. In the case of the WAF available with Progress/Kemp LoadMaster, these security rules are updated automatically on a regular basis.

Using the LoadMaster WAF as an example, this WAF’s rules provide protection against the major vulnerabilities identified in the OWASP TOP 10.
OWASP are an independent, industry supported group who focus on application security and annually conduct research into application security. Over the years, the vulnerabilities in the OWASP top 10 have changed as new exploits become more common and older exploits have been mitigated over the years as application vendors fix vulnerabilities. The rules provided by LoadMaster include these older vulnerabilities, alongside application specific protection.
How is a Web Application Firewall Used?
Let’s take a quick look at some of these vulnerabilities and how they are exploited, starting with SQL Injection.
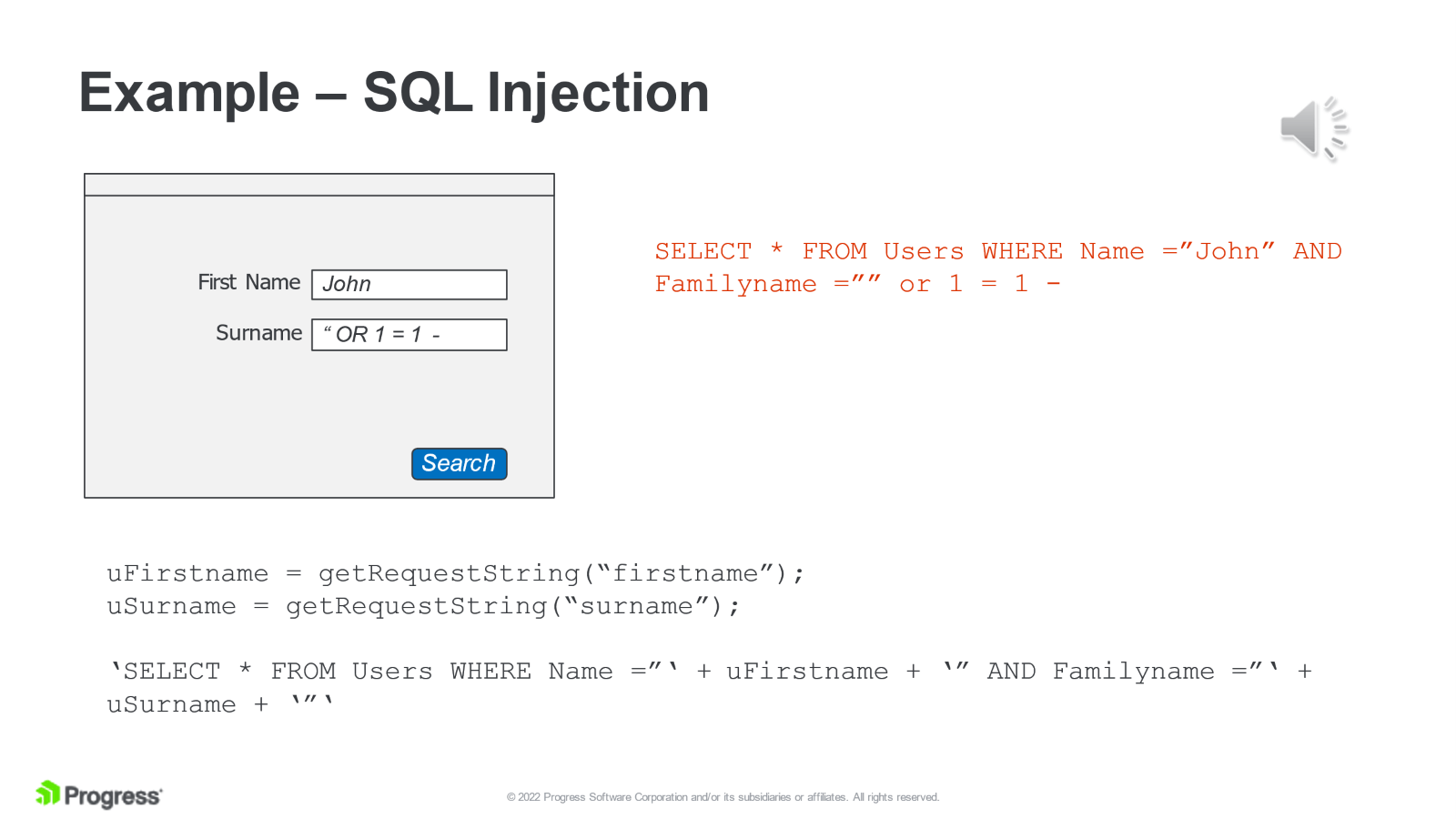
The above illustration shows what an SQL injection attack looks like. An SQL injection attack attempts to modify the behavior of an SQL statement at the back end server by injecting additional SQL commands.
Here we have a form that takes in variables and constructs an SQL statement based on the values in the form fields. However, if a malicious actor injects some additional SQL via the surname field, the results returned are completely different.
In the below example, we see a normal access where a user accesses their own account. However, if they modify the parameter on the HTTP request, they are allowed to access someone else’s account. Again, not exactly a desirable outcome.
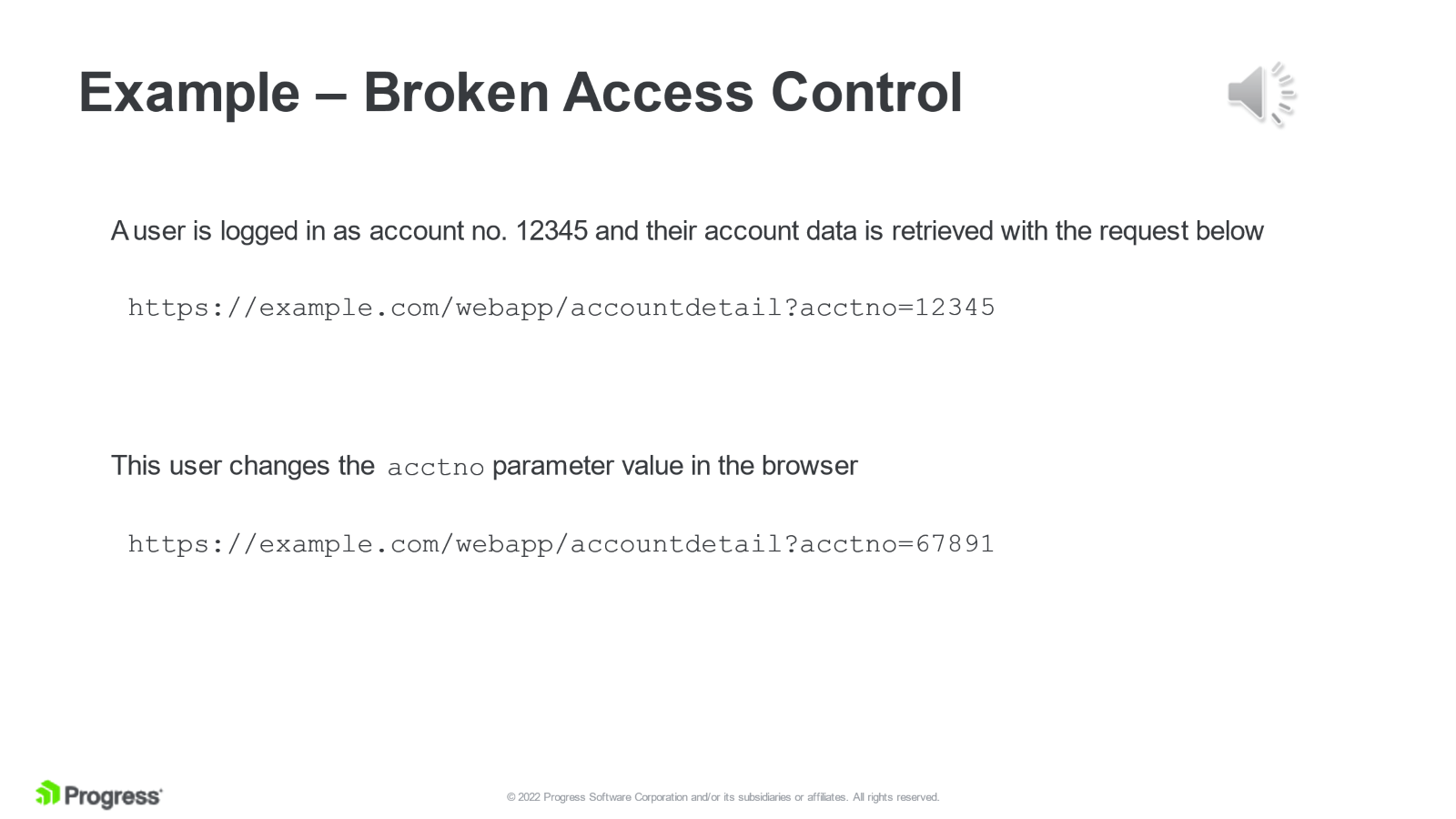
These two are very simplistic – applications should be coded much better than this - but they may still be susceptible to well-crafted attacks designed to exploit a very specific weakness.
Application weaknesses may be inherited from 3rd party or open-source components, which when updated may introduce new vulnerabilities. This is why application protection should be ongoing and not just based on periodical security checks such as app penetration tests.
What are the Types of Web Application Firewalls?
There are three main types of web application firewalls:
- Cloud-based WAFs are delivered as a service and the firewall exists completely in the cloud.
- Hardware-based WAFs are hardware devices deployed on a LAN.
- Software-based WAFs are generally deployed via a virtual machine and can run in the cloud or on-premises.
WAF Deployment Modes
What Web Application Firewall Should I Use?
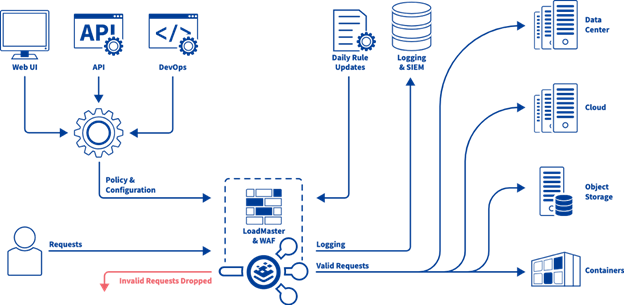
Here is a detailed look as how the web application firewall works.
Protection Against OWASP Top 10 Attacks
As mentioned earlier, the Open Web Application Security Project (OWASP) Top 10
identifies the most common and critical web application attacks. LoadMaster WAF has pre-defined rulesets to fight these very vulnerabilities. Built-in WAF protections include:
- Cookie Tampering
- Injection Attacks
- Cross-Site Scripting (XSS)
- Data Loss Prevention (DLP)
- Buffer Overflow Protection
- Access Control
- Security Misconfiguration
- Real-Time Protection
- Denial of Service Protection
- Botnet Attack Preventions
- Web-Based Malware Protection
- Zero-Day Threats
Listen and Learn

Maurice McMullin
Maurice McMullin was a Principal Product Marketing Manager at Progress Kemp.
more from the author