Web Application Firewall - Implementing and Managing Your Website Security
Web applications are core technologies for many, probably most, SMEs, enterprises and public-sector organizations. Their widespread use and reliance increase the risks associated with any outages that cause downtime. One of the primary threats that often leads to downtime is cyberattacks. Robust security to protect web applications is as core to efficient business operations as the applications themselves.
Web Application Firewalls (WAFs) are vital to the broader cybersecurity protections needed to secure web applications. They provide an essential line of defense by protecting websites from various malicious attack types. In the sections below, we’ll discuss the importance of WAFs, provide guidance on how to plan for their deployment and comment on how to deal with common challenges.
Importance of Web Application Firewalls
The threat landscape that web applications operate in is constantly changing. Cybercriminals frequently discover and exploit new threats, including zero-day vulnerabilities. Attackers also change their techniques to bypass the cybersecurity measures in place. Let’s not forget the risks from well-known threats such as SQL injection, cross-site scripting (XSS) and DDoS attacks, which continue to be significant.
WAFs play a crucial role in defending against the threats that current web applications face, including the threats in the OWASP Top 10. They serve as a shield between your web applications and the internet, filtering and monitoring web traffic flowing to and from applications. WAFs do this by inspecting network traffic from load balancers to web application servers. A WAF can block malicious and suspicious network requests and traffic from reaching the web application servers. Using WAFs as a core part of a wider cybersecurity protection strategy significantly reduces the risk of successful cyberattacks and data breaches. As such, they help protect your business applications, sensitive data and your organization’s reputation.
WAFs typically support multiple techniques to monitor and filter traffic flowing to web application servers. These techniques include:
Signature-Based Detection - WAFs use rules and lists of known attack patterns to detect malicious activity.
Anomaly-Based Detection - An established baseline of regular network activity gets recorded. Any deviations from this baseline are detected, and steps are taken to stop malicious activity. See the Progress Flowmon ADS site for a Progress solution that takes this defense method to the next level.
Security Models - WAFs can use Negative (block) and Positive (allow) lists to control traffic flow to web applications.
WAFs protect against web application attacks and often include additional features such as bot attack prevention, DDoS protection, API security and integration with other security solutions, such as SIEM systems.
WAFs are essential to the broader security strategy to protect web-based applications. They provide an extra layer of protection against cyberthreats targeting the application layer.
Understanding WAFs: An Implementation Guide
Configuring and implementing a WAF will require a combination of standard configuration settings plus changes unique to the network environment and web applications deployed. At a high level, the implementation choices will vary between these three deployment options:
Network-Based WAF - Typically dedicated hardware-based and installed on a local network. They provide high-speed protection and are often also load balancers with dedicated TLS/SSL chips to process network traffic decryption and encryption.
Software-Based WAF - Software-based WAFs are typically deployed as a component of a load balancer running in a virtual machine. In some instances, they can run directly on a web server. However, this approach is not recommended for security and performance reasons.
Cloud-Based WAF - There are two common cloud-based deployment methods. The first is to use a WAF that the third-party cloud platform provider manages. This method offers ease of deployment without an ongoing need for management. Another cloud option is to deploy a third-party WAF (often along with a load balancer) as a dedicated service from the cloud platform marketplace or via a server virtual machine. This option gives the organization using the WAF more control over the settings, but it does require more setup and management. A significant advantage of this approach is that it allows the use of a common WAF across all parts of a multi-cloud and on-premises hybrid infrastructure. In this scenario, systems admin staff only need to learn how to use a single user interface and set of configuration screens.
Implementing WAFs
When planning a WAF deployment, you should include the following steps in the process to pick a WAF and deployment method:
Evaluate Your Needs - Determine the type of WAF that best fits your web application based on factors such as traffic volume, application architecture and specific security requirements.
Select a WAF Solution - Choose a WAF provider that meets your criteria. Consider factors like ease of integration, cost, support and feature set. Read more about the enhanced WAF included in LoadMaster 360.
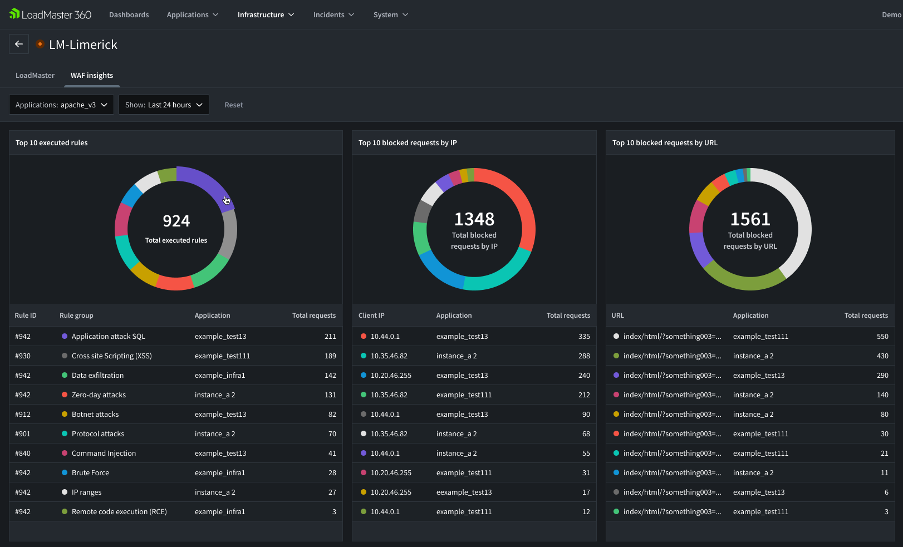
Image 1: LoadMaster 360 WAF Insights
Configure the WAF - To increase defenses against common threats, you can configure the WAF by defining security policies, setting rules and customizing the configurations to suit your application. For details on configuring the LoadMaster 360 WAF, read the LoadMaster WAF documentation pages.
Test - Implement the WAF in a staging environment first to verify if it doesn’t interfere with legitimate traffic. Monitor performance and make necessary adjustments. Another common option is first to deploy copies of the WAF you plan to use to DevSecOps and Q&A environments. When testing your WAF deployment, the LoadMaster 360 Insights screen provides valuable information on what the WAF is seeing and blocking in the network traffic. The WAF Rule Tuning setting outlines how to tweak the rules on the WAF to meet your particular needs.
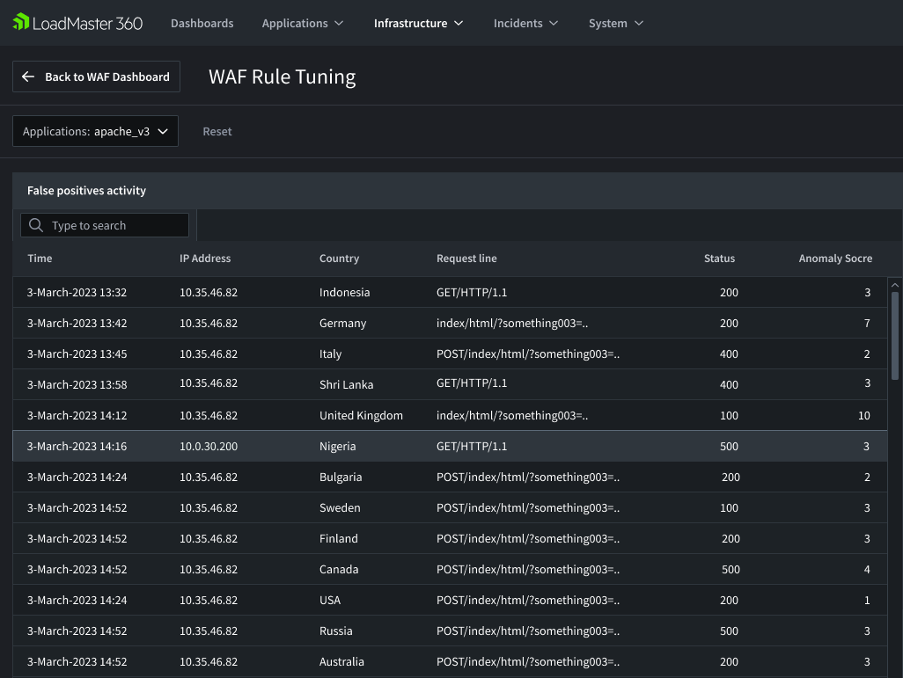
Image 2: LoadMaster 360 WAF Rule Tuning
Go Live—Once tested, deploy the WAF in your live environment. Scripting can make this process seamless. Once the WAF is in production, monitor its operation and adjust the configuration as needed.
The Progress LoadMaster Professional Services teams can assist organizations adopting the enhanced LoadMaster 360 WAF.
Best Practices for Ongoing WAF Management
When a WAF is in a production environment, monitoring its activities and adjusting settings as required is essential. This does not mean that WAFs require constant management, but rather that it’s necessary to confirm they provide maximal cybersecurity protection in the constantly changing threat landscape. In reality, what this means is that your IT team should:
Access Performance Impacts – Confirm that the WAF doesn’t hinder web application performance. It’s especially important to check this after any updates to the web application or the WAF software.
Install Updates Regularly - Keep the WAF software and rules updated to protect against the latest threats.
Log Monitoring - Systems administrators should monitor WAF logs for abnormal activity. Most modern WAFs, such as the LoadMaster 360 WAF, can forward logs to dedicated log monitoring and SIEM systems for analysis. Rules on the WAF should be adjusted as required if the Log analysis highlights any potential security gaps.
Rule Updates and Tuning - Periodically review and adjust the WAF protection rules to minimize false positives and verify that legitimate traffic isn’t blocked.
Create an Incident Response Plan - Have a plan in place to respond to incidents quickly. The incident plan should be tested periodically via a simulated incident so that key staff members know how to react when an actual incident occurs.
By following these best practices, you can maximize the protection offered by your WAF and keep your website secure in the face of evolving cyber risks.
Integrating WAFs into Your Overall Website Security Strategy
WAFs are not remedies for cybersecurity. In the modern threat landscape, a broad set of security solutions and techniques are required to deliver a comprehensive defensive posture. Having said that, we shouldn’t downplay the importance of WAFs. They are a vital part of any cybersecurity defense strategy; you must include them if you deliver web applications over the Internet.
WAFs augment security defenses in several ways. The best way to deploy them is as part of a robust cybersecurity defense strategy that includes network firewalls and other technologies such as intrusion detection systems, network detection and response (NDR) solutions, Security Event and Information (SEIM) systems, Identity and Authentication Management (IAM), Zero-Trust Network Access (ZTNA) and more.
It’s worth noting that WAFs do not replace traditional network firewalls. Rather, they enhance the security provided by existing network and security tools by enabling an additional layer of security inspections and checking network traffic in different and complementary ways.
WAFs add the following to security defenses:
Defense for web applications - WAFs act as a final line of defense for web applications and web servers. They sit between user endpoint devices and web application servers and monitor web traffic to detect security issues before they can reach and impact the web applications.
Enhance security provision - WAFs understand how web traffic uses the HTTP/HTTPS protocols. As a result, they can inspect network packets to look for potential threats and prevent exploit attempts that traditional network firewalls will not detect. WAFs can decrypt network traffic to inspect it for malicious payloads. And also encrypt network packets they send.
WAFs play a crucial role in a complete cybersecurity strategy. Integrating WAFs with other security measures creates multi-layered defenses that address numerous cyberthreats. For an overview of the typical security provided by a WAF and, specifically, by LoadMaster 360 WAF, read this blog post and the LoadMaster 360 Enhanced WAF website.
Case Studies: Successful WAF Implementations
We’ve included case studies of organizations that have deployed WAFs to boost the resilience of their web application infrastructure. The case studies feature the LoadMaster WAF and showcase how WAFs have helped prevent attacks, mitigate risks and contribute to overall website and web application resilience.
Learning from others’ experiences is an excellent way to gain valuable insights and best practices for your WAF implementation and management strategies. Here are a few selected LoadMaster success stories that include using a WAF, taken from our Resource Library Case Studies section.
Sligro, a leading food and drinks supplier in the Netherlands, deployed 14 Kemp LoadMasters to provide continuous uptime and security across its applications used by over 50,000 users. As an eCommerce business, security was critical to Sligro and the web application security enhancements provided by the WAF and the other security features available via LoadMaster were very important to their deployment choice.
The Dell Technologies Demo Center selected LoadMaster and WAF to help protect this vital technology demonstration and sales resource from application-layer attacks so that it would always be available to all staff, customers and partners worldwide.
Cantarus in the UK is a full-service digital and web design agency that works with membership organizations, charities and businesses. It delivers numerous customer solutions, from website and app hosting to infrastructure as a service or cross-platform integration. It’s vital that its digital services are always available and secure, so it deployed sets of virtual LoadMasters across two data centers in a high-availability configuration. To enhance the security of its own and its clients’ web applications, Cantarus deployed WAF to this highly available configuration.
Other case studies in which WAF played a part in the success are available on the case studies site.
Common Challenges and Solutions in WAF Management
Despite the benefits of WAFs, managing them can present specific challenges. From configuring rules to minimizing false positives to keeping up with the latest attack signatures, cybersecurity teams often face a range of annoyances when managing WAFs. Relying on the expertise of trusted sources and experts can mitigate the problems.
Rule Complexity - Using a WAF that can import industry standard rulesets and that you can update daily via a subscription from a trusted provider will reduce the overhead of initially configuring rules on a WAF and keeping them current against changing threats.
Reducing False Positives - Cybersecurity professionals are already busy. They don’t need to deal with the noise from false positive alerts generated by a WAF. The ability within the WAF to adjust the sensitivity of settings to reduce false positives is essential. Having sets of predefined configurations that you can import to configure a WAF in an ideal way for a particular application can make this process much easier for system admins.
Attack Signature Updating - Similar to automatic ruleset updates, it’s good to automatically update any signatures being used to detect known attack vectors.
Future Trends in Web Application Firewall Technology
The uptake and use of web applications will only accelerate in the future. As a result, the need for cybersecurity protection from WAFs will also increase. LoadMaster and the enhanced LoadMaster 360 WAF are ideal for this growing need. However, we’ll need to work smarter in the WAF security space. So, how will the sector change over the next few years?
One key trend is the increasing adoption of artificial intelligence (AI) and machine learning (ML) technologies. By analyzing vast amounts of data on network activity, WAFs using ML will predict potential issues before they become problems and provide actionable courses of action to administrators. In the future, WAFs will likely integrate with NDR tools.
Application security will experience further developments in the WAF space. WAFs will incorporate additional security elements as cyberthreats evolve to offer extensive protection against emerging threats. For instance, they will likely feature advanced bot protection and management to ward off DDoS attacks and enhanced integration with leading security information and event management solutions.
Progress Kemp LoadMaster and LoadMaster 360 solutions are well-positioned to embrace future trends and advancements in WAF security. LoadMaster and its WAF enable organizations to deliver an optimal application experience in the face of ever-changing challenges. This solution leverages emerging technologies, enhances security features, adapts to multi-cloud and edge computing environments and supports automation and DevSecOps practices.
Conclusion
WAFs are an essential part of the cybersecurity protection infrastructure. They operate alongside other cybersecurity solutions and techniques, including network firewalls, intrusion detection systems, network detection and response solutions, security event and information systems, identity and authentication management, zero-trust network access and more.
By implementing a layered security approach, organizations can decrease the risks of a compromised protective layer as other security layers are in place. Given the constantly evolving cyberthreats, deploying WAFs is essential to your cybersecurity strategy.
WAF with LoadMaster
LoadMaster WAF can play a central role in such a strategy, as it is powered by the industry-leading ModSecurity engine and supported by open-source rule sets and a commercial rules subscription service.
LoadMaster WAF takes advantage of all the benefits of the available flexible licensing models. Deploying LoadMaster instances with WAF via our Subscription Pooled Licensing allows WAF placement that fully meets every organization’s unique application delivery and security needs. Learn more and start a 30-day free trial of LoadMaster, including its WAF solutions.
.jpg?sfvrsn=98fc73aa_1)
Kameerath Abdul Kareem
Kameerath is a Product Marketing Manager at Progress, overseeing the Kemp LoadMaster portfolio. With a background in diverse IT areas such as cloud computing, DevSecOps, IT Ops and APM, she has a passion for writing about all things tech.
more from the author