WAF – Web Application Firewall 101

Traditional network firewalls placed in front web servers offer protection by limiting webserver access to the HTTP and HTTPS protocol ports – normally port 80 and 443. This approach prevents access to the server using other protocols such as telnet (which uses port 23). Because HTTPS traffic is encrypted between the client and the webserver, the firewall has no visibility on what is happening and even when the traffic is unencrypted (HTTP), a network firewall will have limited understanding of the content.
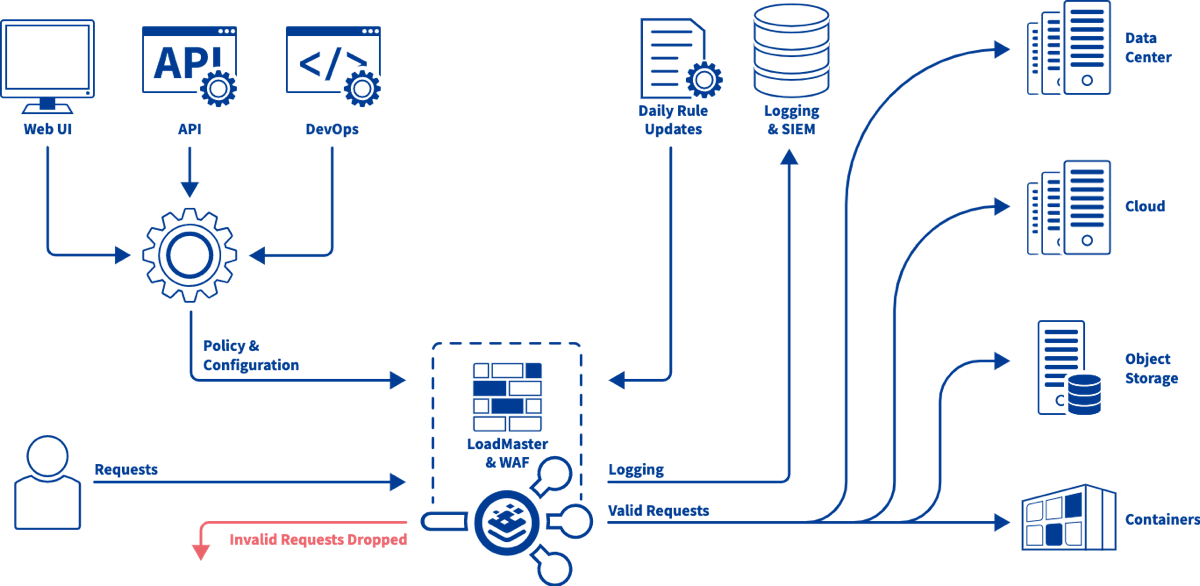
This is where a Web Application Firewall (WAF) comes into play. A WAF is a firewall that can analyze HTTP traffic and identify attacks based on a database of known attacks. A WAF does not replace the network firewall and is normally deployed between the network firewall and the web server infrastructure. To provide maximum protection, the WAF needs to be able to analyse HTTPS as well as HTTP and so will need to terminate (decrypt) the SSL encrypted traffic.
With access to the HTTP and HTTPS traffic streams, the WAF can now analyse the passing traffic to identify and mitigate rogue and malicious content. Such content is identified by, among other techniques, matching against known attack signatures, by limiting the size of requests and by identifying content patterns such as credit card numbers. A reputable WAF vendor will provide regular updates to the signature database to provide protection against the latest exploits as well as offering tools to create custom signatures.
For more on this topic, check out our recent post by Christian Folini. Folini is a security engineer and open-source enthusiast. He holds a PhD in medieval history and enjoys defending castles across Europe. He brings more than ten years of experience with ModSecurity configuration in high security environments, DDoS defense and threat modeling.

Maurice McMullin
Maurice McMullin was a Principal Product Marketing Manager at Progress Kemp.
more from the author