Protecting web applications from cyber threats has never been more important. The risk of attack from cyber criminals, state-based actors and others just looking to cause disruption for fun has never been higher, nor does it show any signs of diminishing. So too the advent of cloud deployment and the increasing prevalence of multi-cloud use in organizations has made cybersecurity more complex than ever before.
What Is Security Strategy?
Protecting your customers, business partners, staff, applications and data requires a layered approach to cybersecurity. No magic solutions will deliver the security needed for modern IT environments. Instead, a security strategy needs to work across both technical and human factors, and provide protection at multiple places and in numerous ways.
Data from multiple industry surveys and reports show that many organizations have significant problems with their
application security. When Veracode — an industry-leading provider of tools helping developers create more secure code and applications
— scanned 130,000 applications, they found that 68% had vulnerabilities listed in the OWASP Top 10 (ref 1). Additionally, Cisco reported in a 2022 Application Security report (ref 2) that “50 % of organizations are lacking sufficient resources
to detect and remediate application vulnerabilities quickly.”
Clearly, work is still required to provide the level of security needed. Multiple technology solutions will need to be used to deliver the necessary multi-layered cybersecurity that realizes a comprehensive security strategy. NIST maintains a Cybersecurity
Framework (CSF) designed to be a foundation for organizations building a security strategy.
Progress provides solutions that operate across all five segments of the CSF, with LoadMaster playing a significant part in a multi-layered cybersecurity response in the Identity and Protect components of the CSF. LoadMaster delivers this enhanced security
in addition to the existing application availability benefits currently enjoyed via LoadMaster deployments.
How does LoadMaster supports your security strategy?
LoadMaster significantly enhances web application security in several areas.
Web Application Firmware (WAF) - LoadMaster includes an enterprise-class WAF to protect both in-house and third-party applications from common vulnerabilities. The WAF also supports the creation of per-application security profiles to
enforce source location-level filtering, adopt pre-integrated rulesets for common attack vectors (including the OWASP ModSecurity Core Rule Set) and provide custom security rules support. The out-of-the-box deployment delivers protection against common
threats without changing your applications or infrastructure. Every organization can tailor this security with custom rules to meet its unique needs.
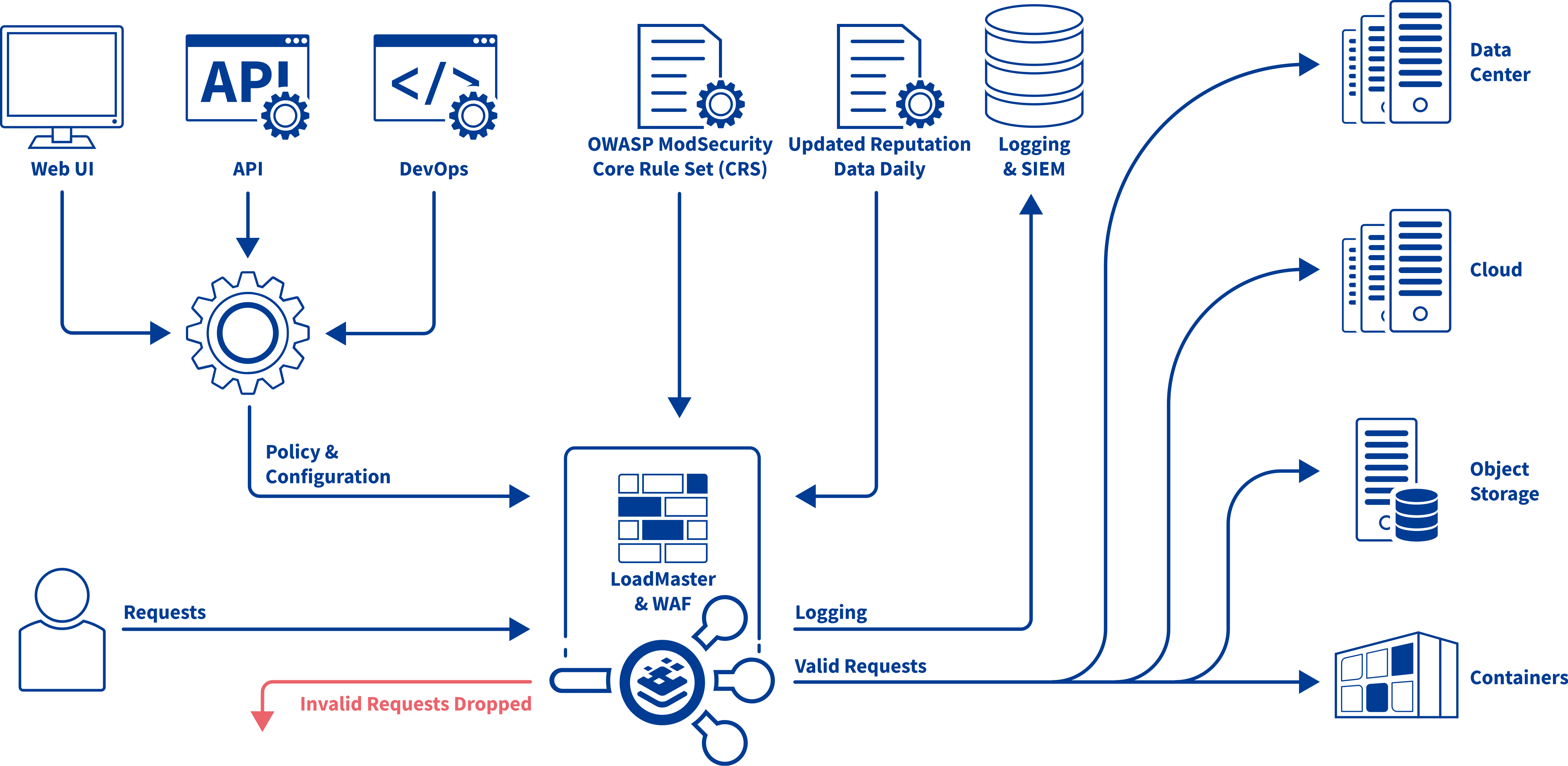
The diagram below shows where WAF on LoadMaster logically sits within a typical application deployment infrastructure. Organizations will likely have applications deployed on-premises and on multiple cloud providers. LoadMaster and WAF sit between
the applications and clients to mediate access requests, inspect the traffic and provide security via the predefined rule sets and any custom rules deployed.
Security Certificate Management - One of the most common issues with the cryptographic security needed to encrypt and protect data at rest and in transit over networks is the expiry of a security certificate. When this happens for
a certificate being used to provide TLS/SSL security for a web application, unplanned downtime is the result. Expired security certificates have been the root cause of many significant service outages that have impacted some of the largest and most
recognizable technology companies. Renewing certificates before they expire prevents this from happening, but all too often those responsible for this task fail to do it before it’s too late.
LoadMaster natively supports the Automated Certificate Management Environments (ACME) protocol. ACME enables IT infrastructure to use security certificates to communicate via an API with Certificate Authorities, which are responsible for issuing trusted
security certificates. Using ACME in LoadMaster enables the automatic renewal of security certificates issued by Let’s Encrypt, Entrust, DigiCert, SSL dot Com and ZeroSSL.
SSL/TLS Security Compliance - Many industry and Governmental regulatory frameworks require that applications use the latest version of TLS/SSL possible (ideally TLS 1.3, the latest at the time of writing). This can be a problem with legacy
applications as they may only support older SSL protocols or even no SSL or TLS at all. This needs fixing if any of these applications are used in organizations that must implement PCI DSS or NIST FIPS 140-2 requirements.
LoadMaster supports TLS 1.3 and can mediate access requests coming in from other systems using TLS 1.3. LoadMaster will isolate any legacy applications that don’t support TLS 1.3 and communicate with them using the latest TLS/SSL protocol they do
support. Then, LoadMaster will return any data from the legacy applications to the requesting user or systems with the data, once again secured with TLS 1.3.
LoadMaster can also enforce the use of cyber suites that deliver security levels mandated by some applications and regulations. This gets done at the LoadMaster level, making managing multiple cyber suites centralized and easier.
Comprehensive Logging - LoadMaster also includes comprehensive logging of inbound and outbound activities and events. This occurs on a granular per-application level and includes support for securely sending logged information to 3rd-party
SIEM systems.
Authentication & Single Sign-on - LoadMaster also supports multiple authentication methods to deliver enhanced security and single sign-on across applications (where it’s appropriate to have this in a zero-trust environment).
LoadMaster can bridge any gaps in built-in authentication by providing pre-authentication services that control access higher up on the access path. The LoadMaster authentication functionality allows access to legacy applications using modern authentication
methods without modifying the applications themselves.
The following methods are supported:
Integration with Microsoft 365 and Azure AD is also core to LoadMaster — and Microsoft has validated this integration. Organizations using AD Federation and Azure AD can use accounts that are in AD via LoadMaster to authenticate users to legacy applications alongside modern ones.
Security Strategy in the Cloud
The security that LoadMaster provides within a broader security strategy gets enhanced when an organization has IT deployments across hybrid and multi-cloud infrastructure.
Most cloud platforms provide a WAF that organizations can deploy for use with applications on that vendor’s cloud. But into a multi-cloud environment, this means that system admins need to know how to deploy and use WAFs that differ from each other.
In many cases, if AWS, Azure and Google cloud deployments are in place, then three different WAFs will need to be configured and managed. LoadMaster is available across all the leading cloud platforms (and can be deployed in a VM on any other). Using
LoadMaster means you can deploy a single WAF type across all your infrastructure and IT staff can learn how to configure and manage it at once.
Deploying LoadMaster across multi-cloud infrastructure will also be cheaper than using native WAF functionality. The cloud providers charge for additional rules, storage, network traffic levels and more on a granular basis. These costs add up over time,
with the ongoing costs for using native cloud WAFs often hidden or else much more expensive than the listed base prices. LoadMaster includes everything in the core pricing model upfront so you can accurately predict your costs.
We mentioned authentication in the previous section. In a multi-cloud environment, Identity and Access Management (IAM) is often a significant management overhead for organizations. Maintaining user accounts and access permissions across multiple platforms
is time-consuming, prone to errors and can introduce security gaps. LoadMaster’s authentication support allows for multi-cloud single sign-on via a unified security model and supports API Gateway access integration. The latter is increasingly
required to enable secure communications across apps and micro-services.
EMA Report
Progress partnered with EMA to take a snapshot of what the industry thinks about load balancing in a multi-cloud world. The report, titled How to Succeed with Load Balancing in a Hybrid Multi-Cloud World, can be downloaded for free from this web page, and you can read more about the report and the background in this blog: How Hybrid Cloud is Driving Load Balancing Strategies—And Why a Unified Approach to Load Balancing Matters.
Watch Our Recent Webinar


