Help Protect SharePoint from CVE-2025-53770 with LoadMaster WAF
In Short: What Is CVE-2025-53770?
On July 19, 2025, Microsoft published a customer advisory about a newly discovered vulnerability in their SharePoint application. On a vulnerable, unpatched version of SharePoint, an attacker can execute arbitrary code on the server: a major security concern.
The waves caused by this vulnerability continue to be felt and it continues to be actively exploited online. SharePoint administrators should update as soon as possible, if they haven’t already done so, to patch this serious security problem.
Administrators who are unable to update are left in a precarious situation. A stopgap solution is to apply a virtual patch to protect against this problem. This is a temporary defensive layer to block exploit attempts without changing the affected software. This is ideal if fully patching SharePoint itself isn’t immediately possible or practical. To be clear: the full, correct and permanent solution is to update SharePoint when and where it is possible to do so.
Blocking the Exploit
The full remote code execution vulnerability relies on first exploiting another, related vulnerability (CVE-2025-53771). By sending a specially crafted HTTP request to a specific legacy SharePoint endpoint, it is possible to bypass SharePoint’s authentication checks and immediately gain authenticated access. It’s then possible to proceed with the remote code execution attack (CVE-2025-53770).
Progress Kemp LoadMaster Web Application Firewall (WAF) functionality is well-suited to detect the specially crafted authentication exploit attempt. When the WAF detects the malicious combination in a web request, it can be detected and blocked, helping to mitigate bogus authentication and reduce the risk of remote code execution.
Virtual Patching with LoadMaster WAF
The virtual patch below helps block known attempts to exploit the SharePoint vulnerability, based on the best information currently available:
# vim: set et sw=4 ts=4 tw=80 colorcolumn=81:
# # colorcolumn=81:
#
# -- Virtual patch for SharePoint vulnerabilities CVE-2025-53770/CVE-2025-53771
#
# Remote code execution exploit leverages an authentication exploit. Detect and
# block requests to the vulnerable legacy endpoint if the request also contains
# the Referer header value required for the authentication exploit.
#
# Case-insensitive regular expression patterns to catch any possible case-based
# evasions.
# Best efforts transformation pipeline to catch possible evasions discovered in
# the future (re-run the regexes after each stage of decoding with multiMatch.)
#
# References:
# https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/
# https://blog.cloudflare.com/cloudflare-protects-against-critical-sharepoint-vulnerability-cve-2025-53770/
#
SecRule REQUEST_URI "@rx (?i)layouts/15/ToolPane.aspx" \
"id:1000,\
phase:1,\
deny,\
t:none,t:utf8toUnicode,t:urlDecodeUni,t:htmlEntityDecode,t:jsDecode,t:cssDecode,t:removeNulls,t:removeWhitespace,t:normalisePath,\
log,\
msg:'Exploit attempt of SharePoint vulnerability CVE-2025-53770/CVE-2025-53771.',\
multiMatch,\
chain"
SecRule REQUEST_HEADERS:Referer "@rx (?i)layouts/SignOut.aspx" \
"t:none,t:utf8toUnicode,t:urlDecodeUni,t:htmlEntityDecode,t:jsDecode,t:cssDecode,t:removeNulls,t:removeWhitespace,t:normalisePath,\
multiMatch"Applying the Virtual Patch
Copy and paste the patch into your text editor of choice and save a copy locally:
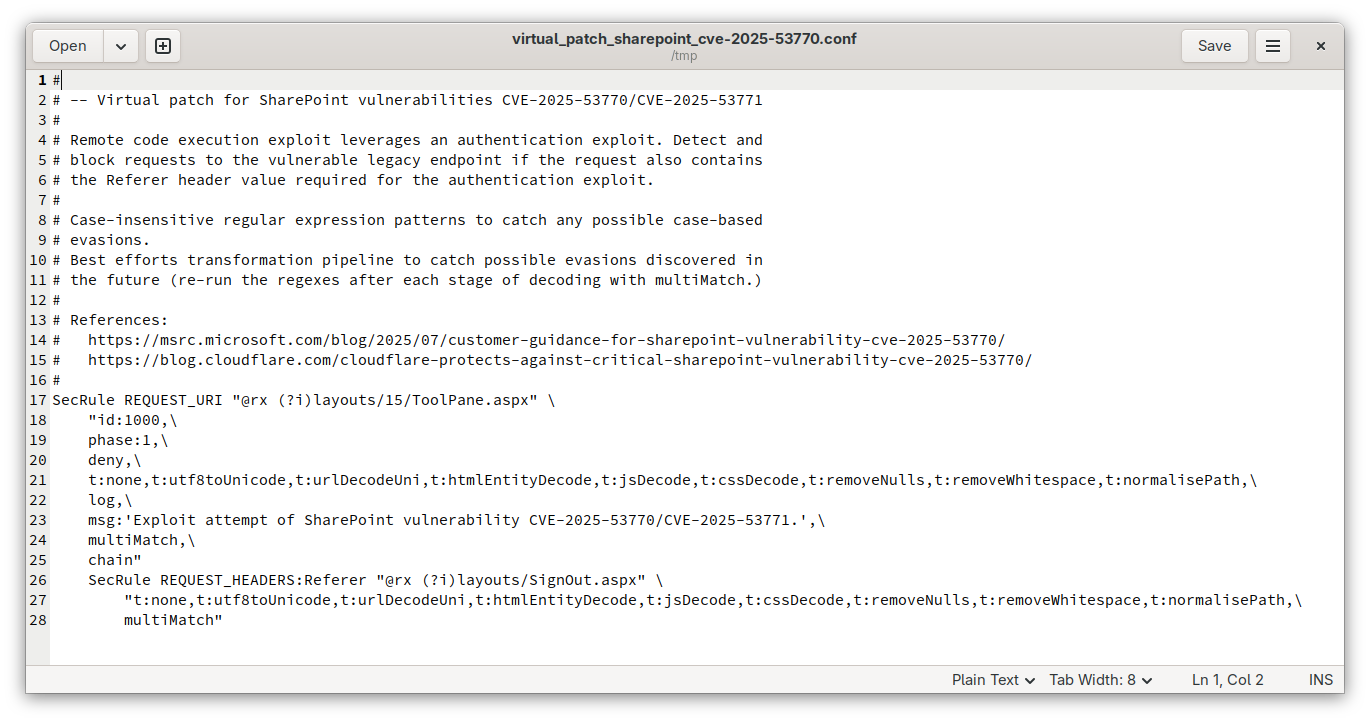
On the web UI of your LoadMaster solution, navigate to Web Application Firewall > Custom Rules. In the WAF Custom Rules section, click ‘Browse’, find and upload your virtual patch file and click Add Ruleset:
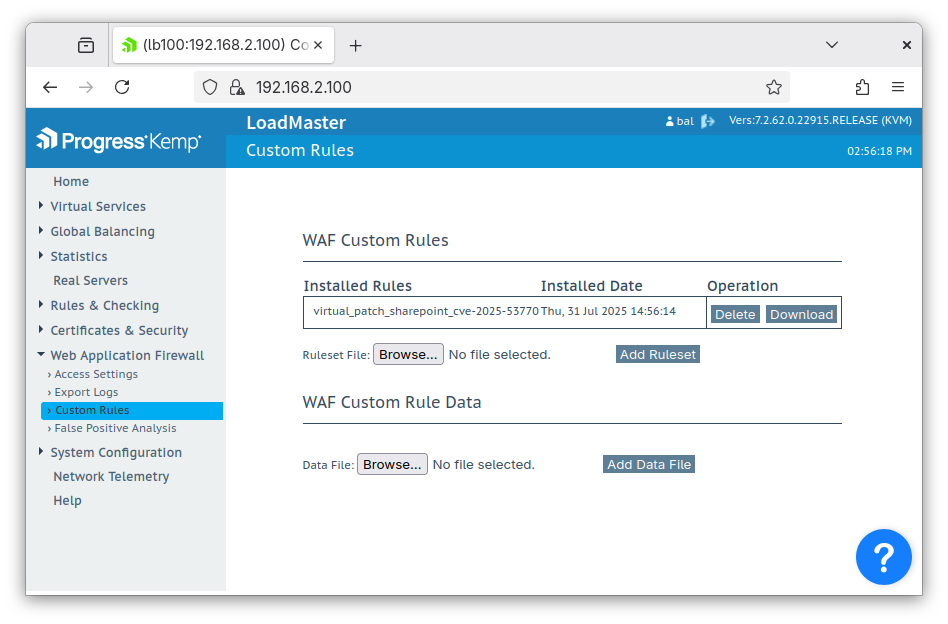
Under Virtual Services > View/Modify Services, click ‘Modify’ on your SharePoint virtual service:
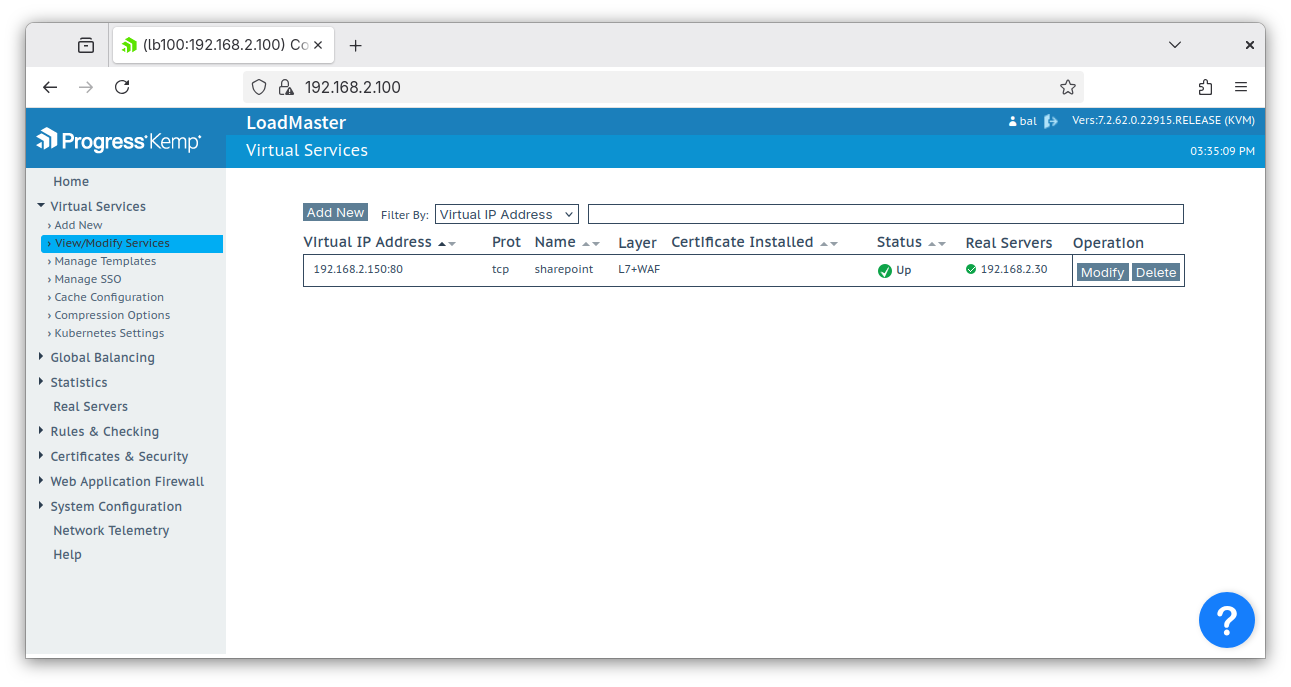
Expand the ‘WAF’ tab. Under Custom Rules, check the box next to the virtual patch file to enable it. Then click ‘Apply’ to put the virtual patch into effect (note: this may cause a momentary blip in active network connections to this virtual service while the WAF daemon restarts):
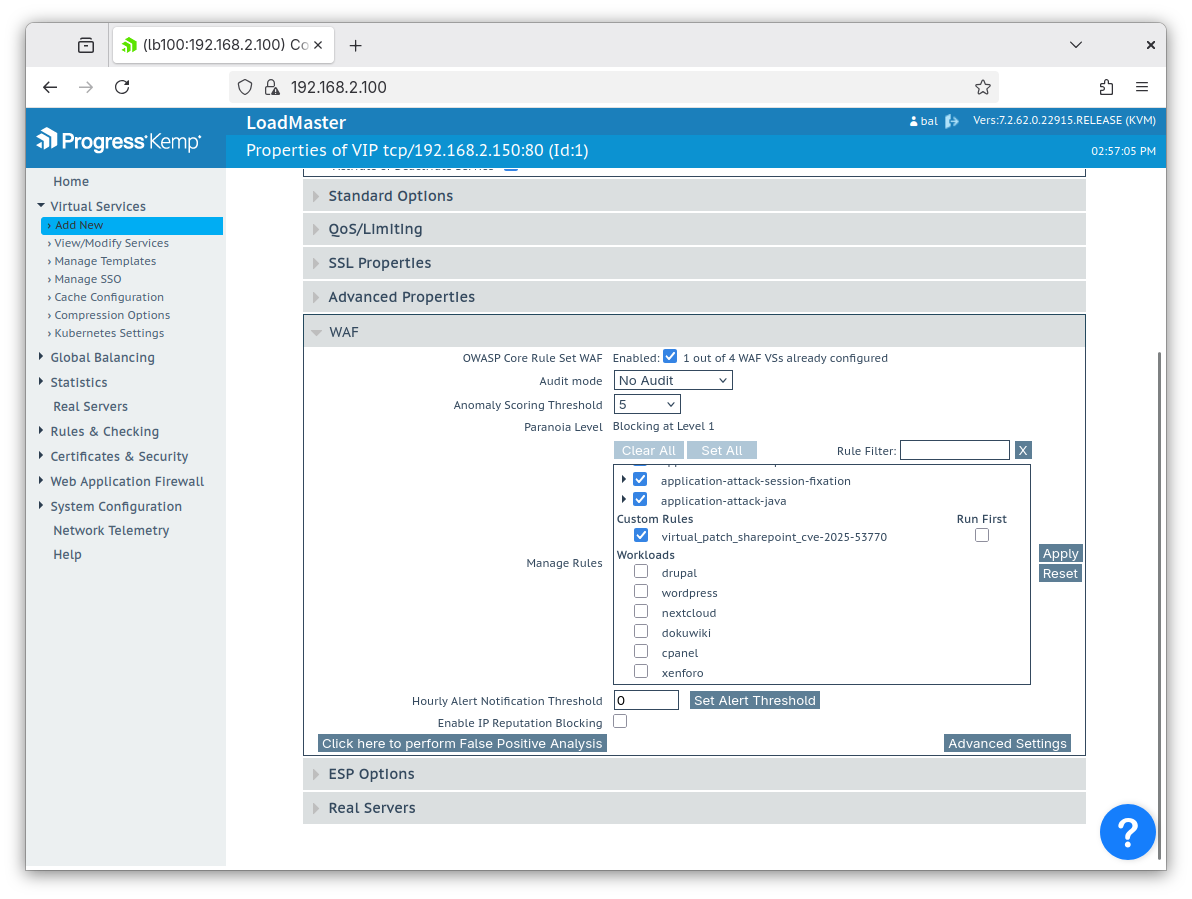
If you have never used the WAF functionality on your SharePoint virtual service before, you will need to tune the OWASP CRS WAF rules to work correctly for your deployment.
To skip the WAF rule tuning step and simply use the virtual patch on its own:
First, check the ‘Run First’ box next to the virtual patch to allow it to execute independently. Then, uncheck all the other WAF rule categories and click ‘Apply’:
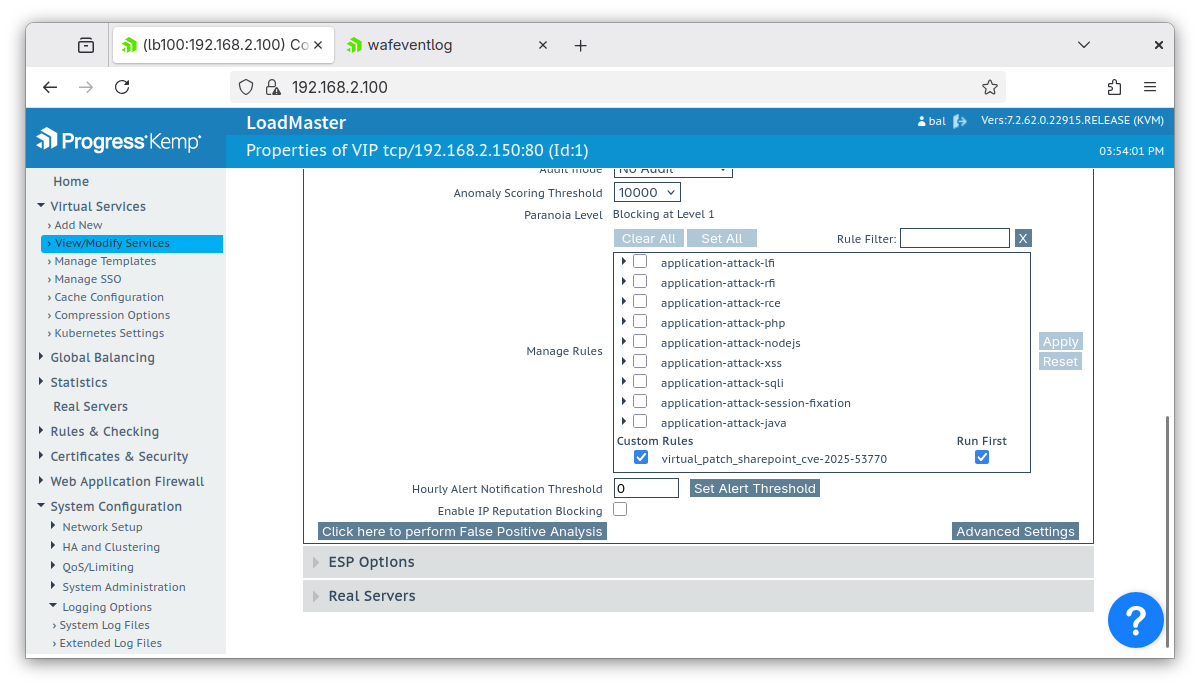
How to Test
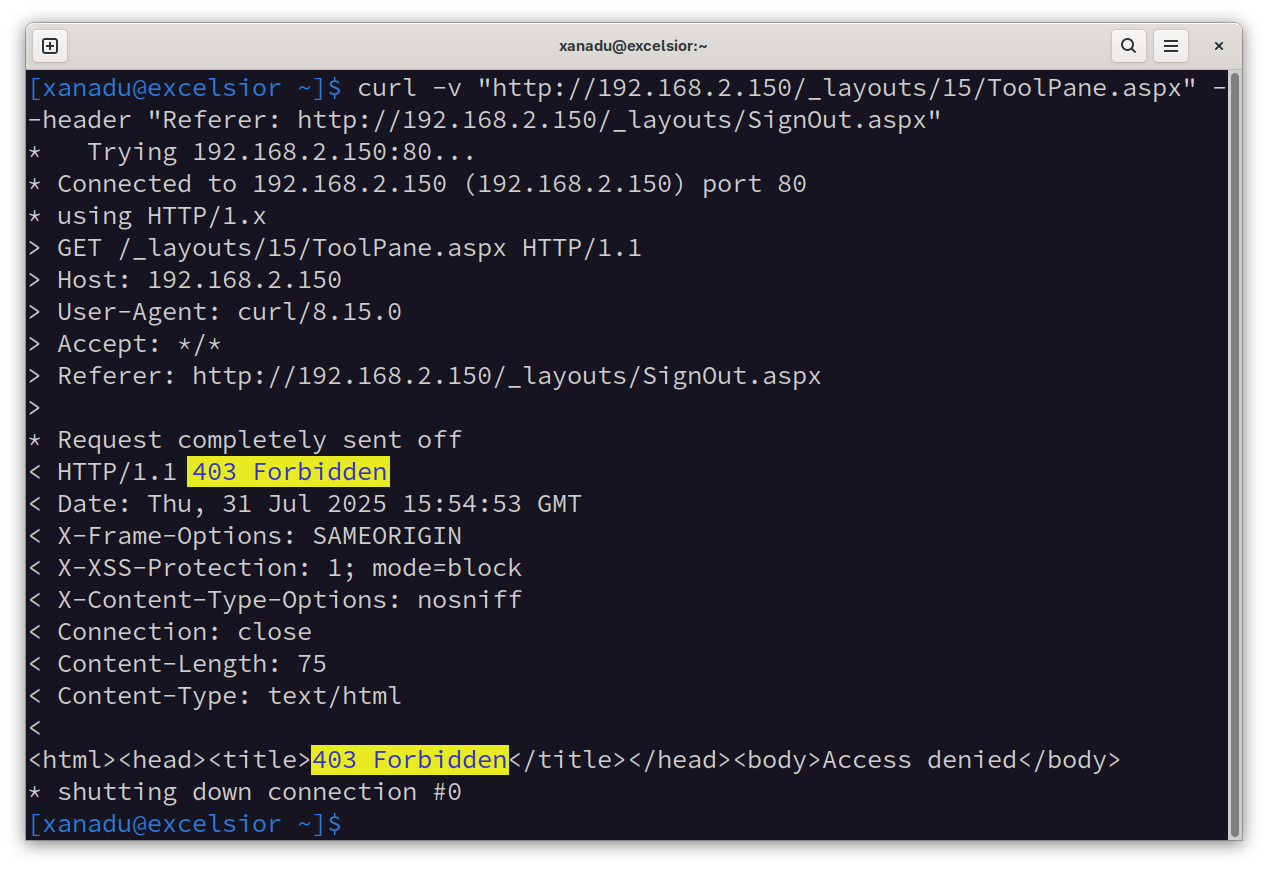
Use a curl call like the following to confirm the virtual patch is working:
$ curl -v "http://192.168.2.30/_layouts/15/ToolPane.aspx" --header "Referer: http://192.168.2.30/_layouts/SignOut.aspx"
A successful block will see an immediate 403 Forbidden response returned by the LoadMaster WAF:
There are publicly available exploit tools, testers and proofs of concept that are more sophisticated than the simple curl call above. These can also test SharePoint deployments for the presence of this vulnerability.
Use caution when executing third-party exploit testing tools or scripts and never run them against infrastructure you don’t own.
LoadMaster WAF with Enterprise Plus: Enhanced Security Capabilities for Your Web Apps
Please contact LoadMaster support if you have any questions or concerns about this SharePoint vulnerability or how to patch it virtually.
Want to use LoadMaster WAF functionality but don’t have the Enterprise Plus licence tier? Please reach out to your sales representative, who will be happy to discuss this.
Do you have other software you’d like to apply virtual patches to? Own legacy software that’s end of life and can never be officially patched? Need an interim virtual patch for a vulnerability until your next maintenance window? The LoadMaster WAF is a flexible platform well-suited to support this—on hardware, virtual and in the cloud. Talk to an experienced LoadMaster representative today about your WAF and security needs

Andrew Howe
Andrew Howe is a web application firewall expert at Progress. Passionate about free and open-source software, he is a developer for the open-source OWASP CRS security project, which helps defend web applications around the globe. Andrew lives in Southampton, UK, and is a fan of left-field cinema, classic synth-pop/disco, and tabletop gaming.
more from the author