Forward Proxy Vs. Reverse Proxy: Differences and Similarities
What is a Proxy?
In the world of computing, a proxy mediates connections between two systems, often a client and server. In the case of a client and server, the client request goes to the proxy, which passes it to the server, which sends the server response back to the proxy, which then passes it back to the client.
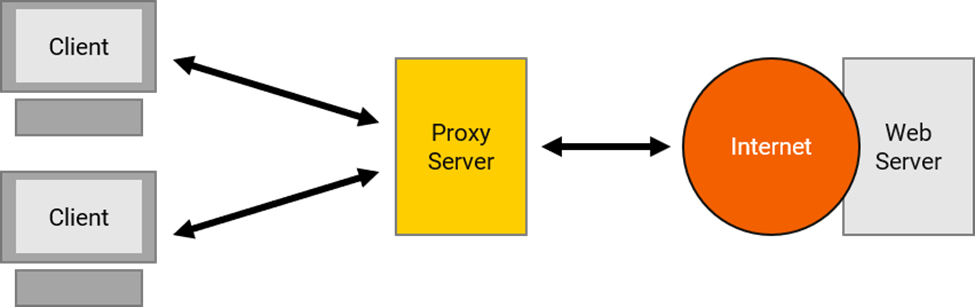
Proxy servers are intermediaries between client devices and web servers. They serve a variety of purposes such as speeding up web access by caching previously visited pages, providing firewall and load balancing services, using proxy identities to protect a user's IP address or real identity and filtering web tracking, allowing unwanted content to be blocked.
What is a Forward Proxy?
What is a Reverse Proxy?
So. What is the Difference Between a Forward Proxy and a Reverse Proxy?
With a forward proxy, websites do not communicate directly with a client. With a reverse proxy, clients never interact directly with back-end servers.
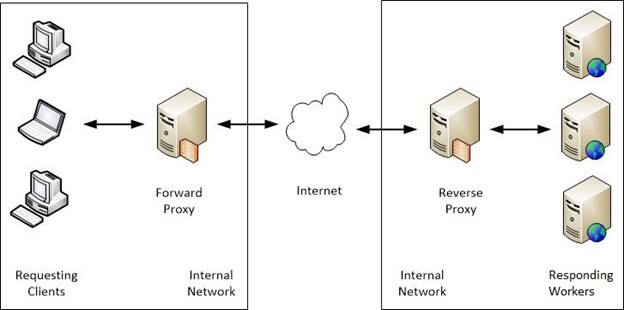
Source: Microsoft
What are the types of forward proxies?
There are several key types of forward proxies mainly defined by where they reside or which locations they serve.
- Residential proxy: Residential proxies generally come from an Internet Service Provider (ISP) and mask the actual physical location. In fact, users can generally pick a location, such as country or city, and because the residential proxy address has an actual physical location, the user appears to be from that area.
- Datacenter proxy: This proxy type is generally used by an enterprise and does not come from an ISP. Datacenter proxies can assign IP addresses that come from the data center proxy’s own address pool and or from third-party cloud providers.
- Mobile proxy: While a mobile proxy sounds as if it is made for mobile devices, instead, the proxy IP address itself is from a mobile network in contrast to a residential or data center proxy—named for their fixed point of origin. However, a mobile proxy, by not having a fixed location, makes it appear that that device is using a mobile data network. Mobile proxies are often used by cybercriminals and scammers.
Why Should I Use a Forward Proxy?
There are several key uses of forward proxies. Here are some key details:
- Getting content from restricted geo-locations: Sometimes, it is important to access data from restricted geo-locations, such as a US-based end user wanting or needing content from Italy. A forward proxy, by masking the identity and geo-location of the client, can access content otherwise restricted to specific countries.
- Keeping web servers anonymous: A forward proxy server hides the real IP address of web server, replacing it with its own proxy’s IP address and keeping the web server secure.
- Web scraping: Web scraping is perhaps the most common forward proxy use and helps companies gather information off other sites, often from a competitor to provide market intelligence.
What are the Types of Reverse Proxies?
Some reverse proxies are basic intermediaries, sitting between users and a web server and obscuring the IP addresses. Others have deeper functions such as load balancing and firewall network security services. The best, such as Kemp LoadMaster, have a bevy of features.
- Load Balancers: A load balancer can be deployed as software or hardware to a device that distributes connections from clients between a set of multiple servers. A load balancer acts as a ‘reverse-proxy’ to represent the application servers to the client through a virtual IP address (VIP). This technology is known as server load balancing (SLB). SLB is designed for pools of application servers within a single site or local area network (LAN).
- Application Delivery Controllers: An Application Delivery Controller (ADC), sometimes referred to as a load balancer, is a network server that takes processor-intensive tasks off the web servers so they can focus on application tasks. ADC is a core component of an Application Delivery Network, which is made of a suite of technologies deployed in concert to deliver applications efficiently over a network.
- Encryption Servers: Here, the reverse proxy includes encryption services such as TSL and certificate management.
- Caching Servers: These servers are designed mainly to speed load times and network performance by caching frequently accessed content.
- Content Delivery Networks (CDN): These networks, designed for high-traffic websites, cache traffic to locations closer to the end users for quicker content delivery and have data centers spread across geographies to hold this content.
- Web Application Firewall: A Web Application Firewall (WAF) builds on and enhances traditional firewall security protection. Traditional firewalls don't stop encrypted HTTPS traffic as they have no visibility of the content and sensitive data within. A Web Application Firewall, which is logically placed between standard firewalls and web servers, operates at Layer 7 of the network stack. It can decrypt HTTPS traffic and inspect the data content. In conjunction with lists of known attack methods, the Web Application Firewall can deny access to web servers when it detects malicious activity.
What is the Difference Between a Load Balancer and Reverse Proxy?
What Does a Load Balancer Do?
Application Workloads/Servers
Availability
Proxy 101: Three Frequently Asked Questions
Is VPN a forward proxy?
What is DNS forwarding proxy?
Which proxy is better for my business?
Can a forward proxy act as a reverse proxy?
Learn More
Learn all you need to know about ADCs and how your enterprise can benefit on the Application Delivery Controllers page.

Doug Barney
Doug Barney was the founding editor of Redmond Magazine, Redmond Channel Partner, Redmond Developer News and Virtualization Review. Doug has also served as Executive Editor of Network World, Editor in Chief of AmigaWorld and Editor in Chief of Network Computing.
more from the author