Maurice McMullin

Maurice McMullin was a Principal Product Marketing Manager at Progress Kemp.
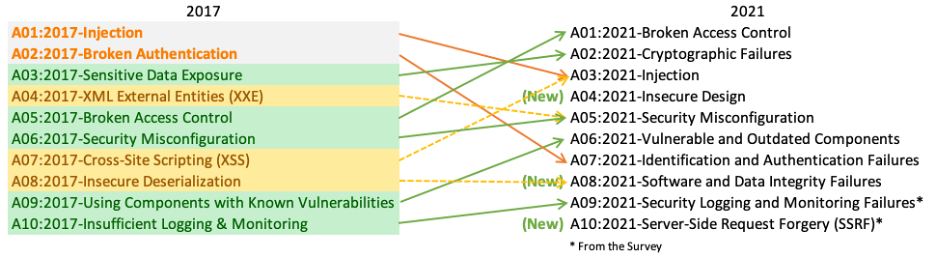
OWASP 2017 – A1 Injection
| 5 min read
OWASP 2017 A10 – Underprotected APIs
| 3 min read
Top 15 Tips to Increase Exchange Security
| 4 min read