The “Legacy Web Application Firewall (WAF)” feature on Progress Kemp LoadMaster was officially retired in June 2021 and will be entirely removed in the upcoming LMOS Version 7.2.61.0, as previously announced.
The rest of this article details what is happening, why and steps that current “Legacy WAF” users should take.
What is Happening?
We’re removing the retired “Legacy WAF” functionality from LMOS Version 7.2.61.0.
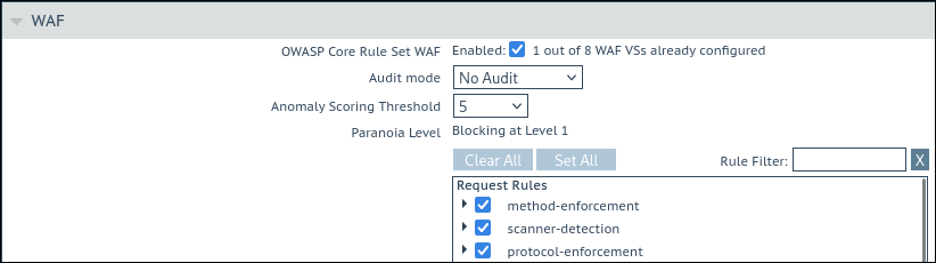
This change doesn’t affect the newer, replacement “OWASP CRS WAF” functionality that has been present since 2021.
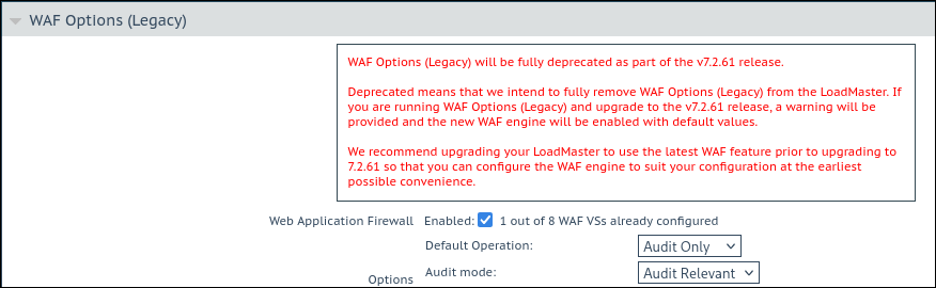
After updating a LoadMaster to LMOS Version 7.2.61.0, the “WAF Options (Legacy)” panel and its features and options are no longer available for new or existing virtual services, including virtual services with the “Legacy WAF” feature enabled before the update.
For existing virtual services with the “Legacy WAF” feature enabled, the replacement “OWASP CRS WAF” is automatically enabled in its place.
- Example of an affected “Legacy WAF” service:
- Example of an unaffected “OWASP CRS WAF” service:
Performing the Update
Before a LoadMaster can be updated to LMOS Version 7.2.61.0, clear warnings and advice regarding the “Legacy WAF” removal are presented.
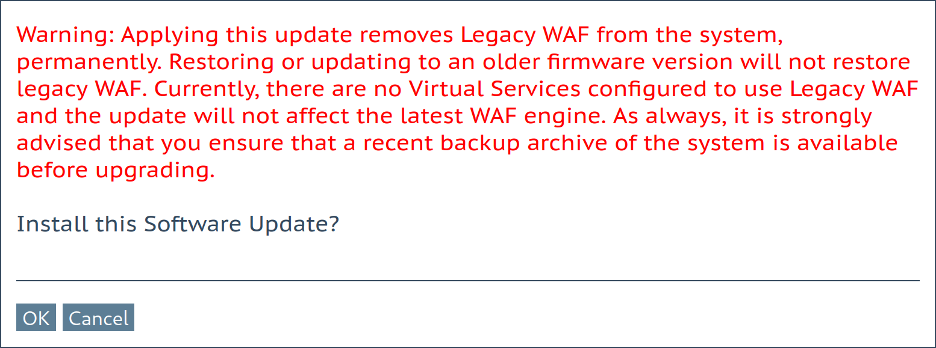
On a LoadMaster without “Legacy WAF” in use, the following pre-update dialog box is shown:
On a LoadMaster where one or more “Legacy WAF” services are in use, the affected virtual services are listed in a pre-update dialog box like the following:
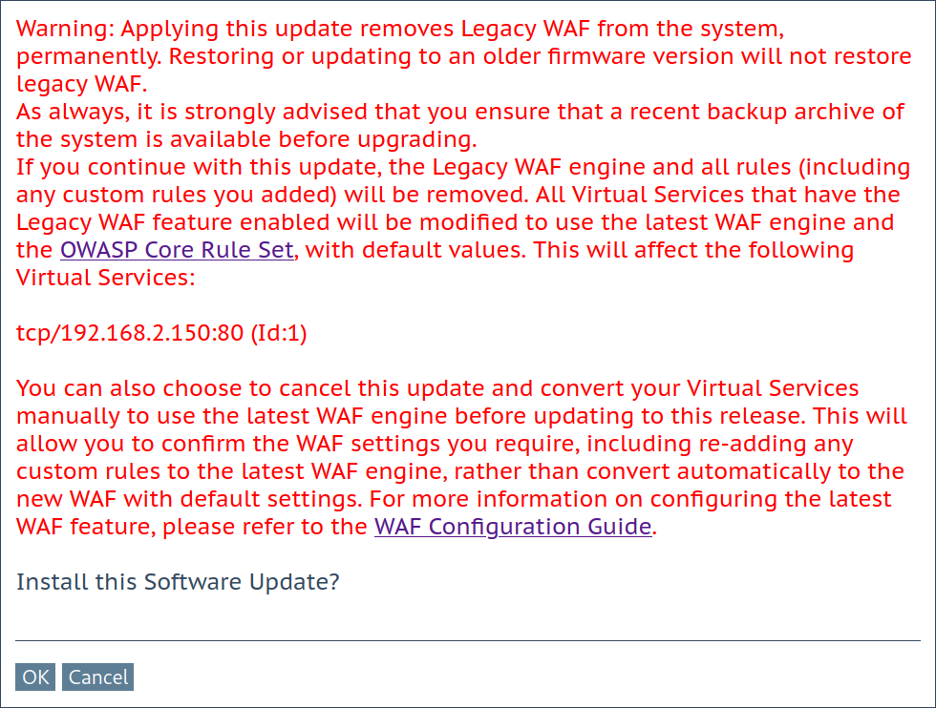
Users are strongly advised to take a system backup before performing the update. This is particularly important for systems using “Legacy WAF.”
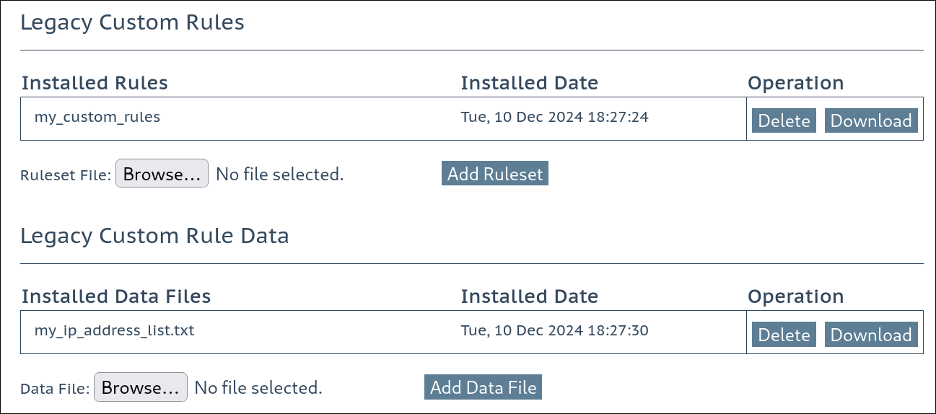
Suppose any “Legacy WAF” custom rule files or custom rule data files are present (navigate to Web Application Firewall > Custom Rules in the Web UI). In that case, it’s imperative to download them for safekeeping, as they will not be available after the update.
Why is This Happening?
The “Legacy WAF” system provided protection using a commercial set of security rules from a third-party security rule provider. This rule set began an End-of-Life process in August 2021 and ended in July 2024. It’s now unsupported and will not receive further updates or security fixes, making it unsuitable for ongoing use in any serious security capacity.
In April 2021, LMOS Version 7.2.54.0 added a replacement WAF solution, “OWASP CRS WAF,” to provide a sustainable, long-term WAF security solution for LoadMaster users. This new WAF solution uses OWASP CRS, a widely used, industry-standard, free, open-source WAF rule set. The well-known OWASP Foundation actively and transparently develops it and is not beholden to any commercial organizations, making it a resilient long-term choice.
Security Benefit to LoadMaster Users
The retired “Legacy WAF” system used a security rule set mainly written to detect specific, known vulnerabilities and payloads. This approach is limiting as it relies on:
- Specific and new written rules to detect each new vulnerability
- Timely updates based on the rule set by continuous vendor publishing
- Promptly obtain LoadMaster data and apply the latest rule set files
In contrast, the newer replacement “OWASP CRS WAF” system uses a generic rule set to detect and help reduce traffic based on anomalous and malicious-looking behaviors. Its generic nature allows it to detect numerous attacks, including the OWASP Top 10 attack categories, zero-day vulnerabilities and even unknown exploits. This is possible because entirely new and original attacks are rare. New attacks are usually similar to other attack classes. As a result, new attacks trigger security rules written to detect unusual behaviors.
Further Advice for Current “Legacy WAF” Users
Users can convert existing “Legacy WAF” services to replace “OWASP CRS WAF” before updating to LMOS 7.2.61.0. This provides plenty of time to tune and configure the new WAF functionality as required for each web application (refer to the LoadMaster documentation for further details on this process).
Where custom “Legacy WAF” rules exist, sometimes these can be reused with the new WAF system:
- Custom rules that perform specific detections (e.g., looking for and blocking a particular payload, blocking specified IP address subnets, etc.) should be reusable without modification.
- Custom rules performing rule exclusions are not reusable because the “Legacy WAF” rules and rule ID numbers they refer to have been removed.
Don't hesitate to contact our professional services team for personalized advice and consultancy regarding custom WAF rules. Learn more and start a 30-day free trial of LoadMaster, including its WAF solutions.

