Preventing unauthorized SSH access attempts and closing security gaps

Finnish computer scientist Tatu Ylonen invented the Secure Shell (SSH) protocol in 1995 after a phishing attack. His aim was to mitigate this vulnerability by encrypting the communications between clients and servers. Since then, the encryption and authentication offered by SSH have led to it becoming a key building block for secure networks today. SSH authenticates everything from user logins to vital applications and services. Downtime can result in a user not being able to log in or a critical service being unavailable.
However, SSH is only as secure as its implementation. The in-built authentication that is facilitated by SSH can also be a vulnerability. Brute force SSH attacks use a program to generate users and passwords to gain access to your network. This kind of attack can be difficult to detect, identify and resolve in a busy modern environment. When successful, such an attack can give malicious parties access to large swathes of your network. Some of the common reasons for SSH vulnerability are listed below:
Trackability
The number of keys can make it difficult to track SSH keys properly. In a large organization with thousands of servers, you may have millions of SSH keys. It quickly becomes very difficult to track the keys. Each key that is not accounted for is a potential vulnerability.
Key replication
Unlike certificates, keys can be replicated and used by multiple users. Over time, this can mean that a small number of keys can grant access to large parts of your network.
Static keys
The large number of SSH keys can also mean that it is difficult for IT Operations staff to rotate keys. Key rotation can result in access issues for users if an important key is forgotten after the keys are changed so, in practice, many organisations continue to use the same keys for a long time.
Embedded keys
Keys are often embedded in applications and as a result IT Operations teams can be reluctant to change these keys. These can become a vulnerability over time.
Network Security
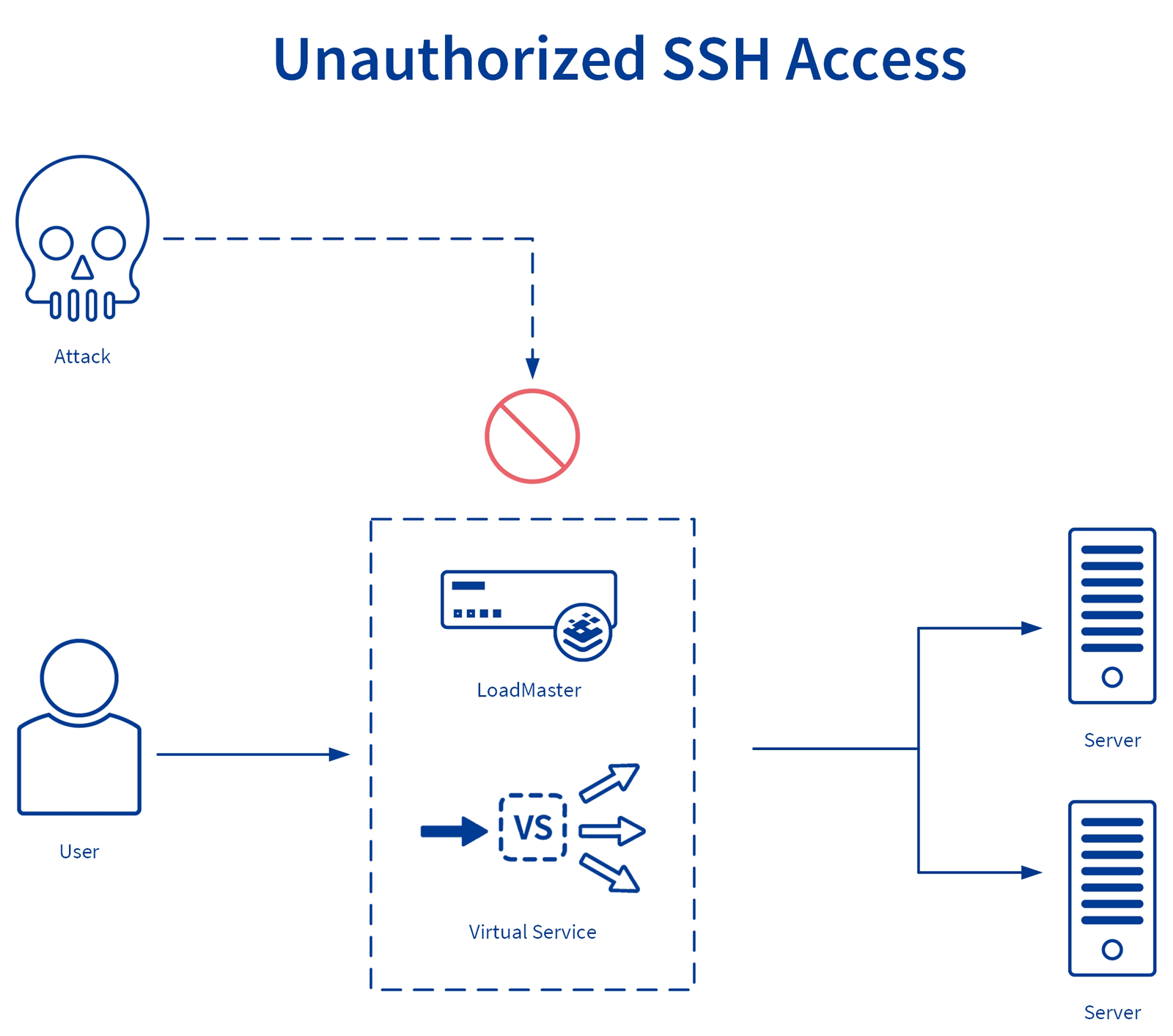
January 2019 brought news of a new SSH vulnerability. This type of attack utilises vulnerable connections to allow attackers to change or destroy information sent between the server and the client. Identifying and preventing SSH attacks requires software with a holistic view of your network that can actively monitor discrete metrics. Does your current monitoring software offer this service? If you are a Kemp customer, you can use Kemp 360 Vision to help identify and prevent SSH attacks.
Imagine the following scenario, you are an Application Delivery Manager on call during the weekend. You are notified by an alert that there have been multiple unauthorized SSH access attempts on the Kemp LoadMaster load balancer. Kemp support use a digital duplicate to monitor your system. They are alerted to the issue by the large number of failed login attempts. Support contact you to check if this is a legitimate attempt. They ask if you want to block SSH access to your management interfaces from unidentified hosts to mitigate the issue and suggest that you review your user authorizations.
You check the audit logs for LoadMaster. You notice that you do not recognise the IP address and you suspect this may be an attack, as suggested by Kemp. You contact the security organisation and they inform you that your report has helped them to identify and close the gap. You have prevented a malicious breach of your network and avoided possible application downtime and data security issues. Simultaneously, you have helped close a gap in your network’s security.
