DDoS attacks – The damage they cause and how you can prevent them

Distributed Denial of Service (DDoS) cyberattacks are an unfortunate fact of life in the modern business landscape. Any company or organisation with an online presence is, in theory, vulnerable to such an assault, which, in simple terms, involves taking a website offline by deliberately overwhelming it with incoming traffic. While the cost of dealing with DDoS attacks can be high – depending upon the business, the per hour cost can run into six figures – the negative impact associated with this kind of action goes beyond the financial. Businesses have also reported a loss of confidence from customers, concerns around intellectual theft, and worries about malware infections arising from such attacks.
DDoS Attacks
Formal and anecdotal evidence suggests that year-on-year DDoS incidents are on the rise and perpetrators are increasingly able to generate more data traffic in individual attacks, with the largest of these now able to consume more than 1 TB per second. We have seen some high-profile targets in recent times – in the United Kingdom, the entire BBC network of websites was knocked offline on New Year’s Eve 2015, the PlayStation Network was targeted in another massive attack in 2016, while last year, in what was the biggest-ever DDoS incident recorded at the time, GitHub was hit by an attack that saw 1.3 TB per second flood their servers.
Knowing as we do the increasing danger posed by DDoS attacks, both in terms of frequency and severity, individual businesses need to ask how their network would cope if targeted and if they are doing all they can to protect themselves. Along with a defence in depth strategy and back up plans one of the best ways to deal with a DDoS attack is to prevent it in the first place, or at least be able to detect it at the earliest possible moment.
Kemp Support
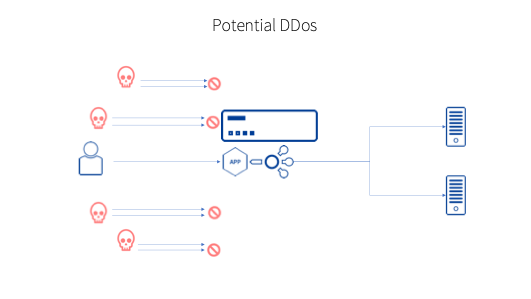
When Kemp LoadMaster detects a high volume of inbound connections it utilises a mechanism called TCPSYN Cookies which protects the network from spoofed Ip address connections. This is done by avoiding inbound queues filling up with illegitimate traffic requests. A SYN queue index is encoded into a sequence number sent in the response of all requests and on receipt of this same index the queue entry can be reconstructed. For spoofed requests this index will never be received thus negating the connections from the spoofed IP addresses.
On top of this mechanism deployed by LoadMaster, two of our support subscription options, Enterprise Support, and Enterprise Plus Support include Kemp 360 Vision, which will identify when this occurs and notify the relevant administrator of the suspect attack. This product has been created to take advantage of almost two full decades of Kemp support knowledge and to put that learning to work for clients.
Kemp 360 Vision
Kemp 360 Vision analyses discrete metrics and communicates these to you through an event-based UI that makes it easy to recognise important alerts in what can be a noisy daily environment. It provides insight into metrics like most recent configuration changes, current transactions per second, and applications with the largest amount of TCP connections, thus helping narrow down the problem. These can alert you to discrete DDoS attacks that other monitoring software and firewalls can miss.
For example, imagine that you are an Application Delivery Manager at a mid-size company with 2,000 employees and revenue of $2 billion. In this role, you oversee your company’s IT infrastructure, and you and your 60 colleagues in the IT department are responsible for monitoring a constantly growing network. The quick and easy deployment and maintenance of applications is a priority. You are also conscious of security requirements and the need to respond to new threats across your complex network architecture.
Now, imagine there is a sudden surge in connections to your application. Users are reporting that some applications are down unexpectedly, but servers are not reporting errors and cloud services are running. With Kemp LoadMaster and Kemp 360 Vision, the LoadMasters TCPSYN Cookie mechanism blocks the illegitimate traffic and Kemp 360 Vision alerts you so immediate action can be taken place.
This highlights the potential benefits that Kemp 360 Vision can bring to your business. Early detection of DDoS attacks can make a quantifiable difference in terms of dealing with such incidents effectively and with the least negative impact on your network.
Additional Information
For more information on how to benefit from Kemp 360 Vision, visit kemp.ax/kemp360/vision or login at vision.kemptechnologies.com.
