Why Kemp Flowmon is a Better Choice Versus Darktrace

It’s been a busy news week in the Network Detection and Response (NDR) and Network Performance Monitoring and Diagnostic (NPMD) sectors. Here at Kemp, we announced that the latest update to the LoadMaster load balancing solution now integrates with Flowmon via Network Telemetry using the Flowmon Probe on LoadMaster. This is a significant milestone in the vision we have for integrating the Kemp LoadMaster and Flowmon product suites that were a key driver in Kemp’s decision to acquire Flowmon.
Darktrace, a solution provider in the NDR marketplace, announced that they would be listed on the London Stock Exchange via an IPO later this year. The IPO has been extensively covered in the mainstream and industry news outlets in Europe and should drive awareness around cybersecurity tools, NDR in particular.
Both these newsworthy items highlight a question that many technologists have been asking since Flowmon was added to the Kemp family last year: “How does Flowmon compare to Darktrace?”
We believe that Kemp LoadMaster coupled with the Flowmon solutions is a better functional and value proposition when compared to the Darktrace offerings. As a pure NDR cybersecurity tool, Darktrace provides protections and benefits that many organizations use every day. But when looked at in the round, the combined Kemp and Flowmon offering delivers more functionality, offers more monitoring data over time, and is delivered at a lower cost.
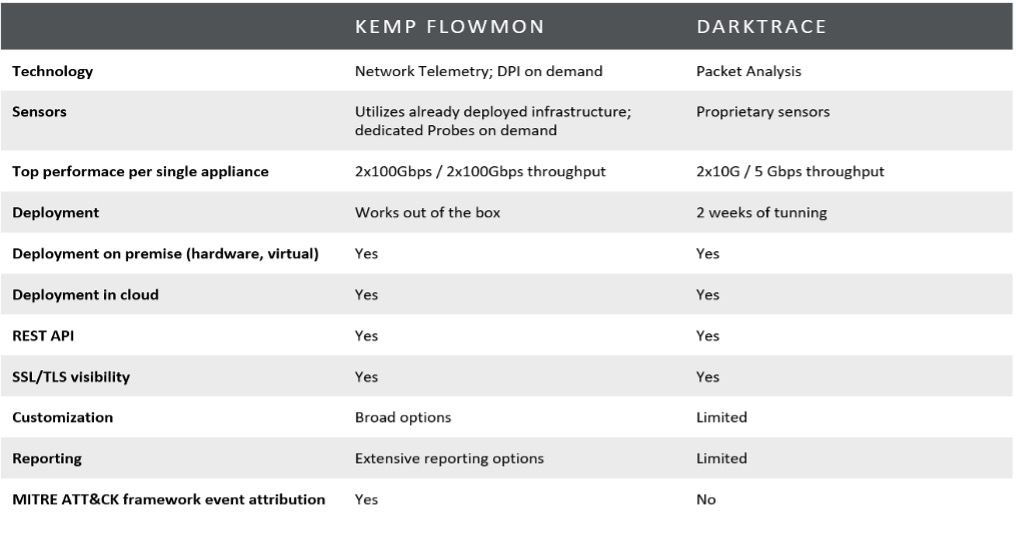
Kemp Flowmon vs Darktrace
Flowmon Flow Data versus Darktrace Packet Capture
The primary differentiator is how the solutions collect the data. Flowmon performs network monitoring based on the collection of flow data. This is a highly efficient technique that reduces the storage required and CPU processing power needed to capture and analyze network monitoring data. Using flow data is efficient since most of the packet content information is irrelevant to network and security operations. When needed, full packet capture is available to help determine the root cause of the issue at hand.
Darktrace uses full packet capture and this has significant storage implications that impact the amount of historical data that can be retained. It also limits where Darktrace can gain visibility in the network without the extensive deployment of probes.
Flow data gathering provides real-time network monitoring and analysis without the considerable storage requirements of full packet capture. Most modern network devices support flow export. Rather than collecting all packets, a flow collector tracks the source and destination IP address and port for each network interaction from flow sources. The duration of the communication and the number of bytes transferred is also recorded and stored. The actual user data in packets are not stored. This can be a good thing when businesses are concerned with privacy and policies like GDPR and HIPAA.
Flow data monitoring
Flow data recording is like how the telephone company tracks your phone calls. Logs are kept of calls that are made with a timestamp and how long the calls lasted. But the contents of the calls are not stored. Flow data monitoring records the connections between endpoints on the network, how long the links were maintained, the amount of data that flowed between them, and the data type. The actual content of the data streams is not retained long term.
Recording flow data instead of full packet data reduces the amount of data stored for network monitoring. Typical reductions range within 250 to 500:1 over full packet analysis. This means that only 0.2% of the storage is required, and the network monitoring data can be retained for extended periods to allow for analysis further into the future. For example, capturing a throughput of 250 Mbps on average equals a data size of 1.8 GB per minute, which adds up to 108 GB per hour and 2.6 TB a day. On modern 10Gbps networks, it’s possible to get to data capture and storage amounts in the range of 100TB! A significant undertaking even if the data is stored for short periods. And short storage periods with rapid deletion means that historical information is not available for deep analysis of events that come to light after the data is gone.
Experience shows that it is possible to analyze and troubleshoot up to 95% of all network incidents that need investigation by collecting enriched flow data. This is possible by using a combination of the NetFlow and IPFIX protocols for collecting flow data. For the other 5% of cases, packet analysis can be enabled (and even triggered automatically in Flowmon) when required to capture the data packets.
The Flowmon Advantage
Darktrace is a pure cybersecurity NDR solution. They have a machine-learning based Enterprise Immune System (EIS) solution for detection, and an optional Antigena tool for automated responses. Flowmon is both an NDR tool and an NPMD tool. The NDR functionality is delivered via the Flowmon Anomaly Detection System (ADS) tool, and NPMD is delivered via Flowmon Monitoring Center. This means that Flowmon provides both cybersecurity monitoring of the network, and performance monitoring and diagnostics to detect and highlight network issues that have nothing to do with cybersecurity attacks. Because of this, Flowmon delivers both security detection and protection as well as service monitoring and alerting.
This combination ensures that the user experience for people using services and applications over the network is optimal at all times. It is this functionality that provides synergy with how LoadMaster delivers an enhanced application experience for web applications. Providing the best application experience requires that both application servers and the network do not have any issues that degrade performance. LoadMaster delivers the optimal application performance, and Flowmon ensures that the network is optimal. When combined, these ensure that all applications are available and ready to respond to user requests.
Flowmon + LoadMaster = Kemp AX
Both Darktrace and Flowmon provide automated responses to network anomalies. Each integrates with third-party SIEM and firewall products to allow for automated blocking of data streams and ports as required.
Flowmon also expands LoadMaster’s web application firewall security to the whole digital environment. Covering not only the application delivery chain but also both north-south and east-west network traffic. This allows the detection and response to events like lateral data movement, data collection, command & control commands, or data exfiltration. This effectively turns the network into another layer of protection against cyber threats and ensures applications are delivered in a secure environment across the whole infrastructure landscape.
In the same way that LoadMaster delivers the best price-performance in the application experience sector, the Flowmon value proposition provides significant savings compared to Darktrace. Typical pricing for comparable deployments can be 2.5x more expensive with Darktrace.
Flowmon is more functional, integrates with LoadMaster to deliver the best application experience, and is more cost-effective upfront and over time.
Conclusion
Kemp LoadMaster and Flowmon combine to deliver a solution that provides enhanced cybersecurity and a better application delivery experience. Whether you are building on an existing Kemp LoadMaster deployment, a Flowmon Anomaly Detection System & Flowmon Monitoring Center deployment, or starting from scratch, deploying these tools together will enhance and simplify your network and application delivery operations.
