5 Steps of Incident Detection and Response

As a security practitioner, every day you experience something new. Sometimes, the new things are not so good and you have to figure out how to respond quickly before the threat spreads across your systems and cause even more serious damage. Network perimeters are usually very well secured hence attackers found another way through.
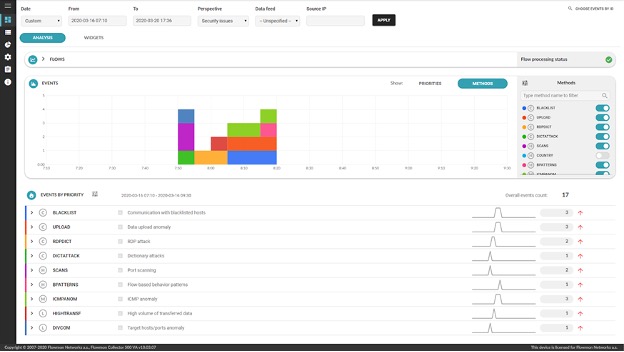
One of the most common and worrisome group of attacks are so called insider threats, malware especially. These are trying to compromise a system and make it to attack other systems within your network. This means that this attack traffic won’t be detectable on network perimeter. It is critical for your security organization to have a complete incident detection and response plan. Let’s take a look on 5 crucial steps of incident detection and response.
#1 Have Proper Tools and Processes in Place
There is always a risk that threats are being missed among floods of false positives and negatives or they are just slipping through visibility gaps. To build a truly comprehensive cybersecurity framework, Gartner analysts suggest adopting so the called SOC Visibility Triad approach. Consisting of SIEM, Endpoint Detection and Response (EDR) and Network Detection and Response (NDR, formerly called Network Traffic Analysis), this visibility triad allows one to eliminate weak points and lift up cybersecurity via cooperation.
While EDR is the only window into endpoints and SIEMs processes the wealth and depth of logs. NDR provides the holistic network perspective. NDR enables one to detect breaches at every stage of compromise since every adversary leaves footprints in network traffic and thus complements SIEM and EDR capabilities.
#2 Detect, Analyze and Determine the Scope of the Incident
Because the vast majority of malicious activities can be seen in the network traffic, malware included, we can use tools to do a forensic analysis of the traffic patterns and content. Port scanning, communication with C&C (Command and Control) botnet servers, high data transfers, anomalies and changes in host’s behavior are just some of the indicators that pinpoint on ongoing compromise.
Once the detection tool alerts you to suspicious activity on the network, you should identify the originator of the event and identify the device(s) responsible for the event. NDR tools are very effective since they can provide you with a lot of additional information including the relevant device by IP address, device domain name, device domain name recorded at the time of detection, the physical address of the device (MAC address) and user identity. In case of ransomware you could extract indicators of compromise such as URLs, hashes, IP addresses, etc.
Determining the scope of the incident is important because modern threats usually conduct lateral movement and spread quickly throughout the network. It is important to analyze the communication on the data network, identify all the communications, potentially affected systems, activity of the attacker and any other potentially compromised systems.
#3 Respond at Early Stage
The goal of every response process should be the containment of the malicious code to mitigate its impact on your network and data. Sometimes the entire response process can be automated, but sometimes heavy lifting is required to manually execute some of your actions. Your response starts with the discovery of an anomalous event, the indicator of compromise (IoC). But every time, your response should include some basic steps based on the IoC observation:
- blocking incoming emails on email server (based on a particular IoCs),
- removing malicious emails from user mailboxes,
- blocking malicious URLs from access on proxy,
- identifying workstations that have visited malicious URLs and thus might be infected,
- identifying workstations which downloaded payload with unwanted IoCs and which executed certain files by EDR system or similar tooling you have.,
- block ransomware traffic indicating calling home on IPS, firewall and on proxy
- prevent out-of-office workstations from connecting to the network until they are scanned for the infection.
As a security professional, it is important to cooperate with network operations team. If necessary, you should have procedures enabling shutting down a branch, business unit or even country from the network and stop the communication with other units in case of danger.
#4 Recover
Remove malicious code from the network and infected systems. It is critical to find the root cause of how the malicious code entered your network and plug the security hole. Patch the vulnerability, upgrade software version, and create a new SIEM rule based on observed IoCs to prevent future malicious attempts.
In the recovery phase, all affected devices and systems should be cleaned, restored and returned back to business. If you were hit by ransomware and cannot decrypt files, restore data from the latest clean backup.
#5 Assess
Complete a post-mortem “lessons learned” incident report [FY1] which will help you to improve the incident response plan and harden your defense. It is also important to continue with security monitoring since some attacks may be only a cover for another malicious activities. Review the incident and possible vulnerabilities that it exposed in your infrastructure and as well as your procedures. Good security is an ongoing process. You can also schedule a training to educate employees if there was a human/social vulnerability exposed.
Comprehensive Incident Detection and Response
All IT organizations have security incidents. The top security teams have a comprehensive incident and detection response plan. It is important to move quickly and deliberately when an incident has been discovered. Build your plan around these 5 steps to take your security response plan to the next level. Visit the Flowmon Security Operations Solutions page to learn more about managing your security detection and response tools.
