Using Flow Data to Better Understand Your Networks and Application Experience

In a previous post, we outlined how flow data collection and flow monitoring work. Rather than repeat that information here, we’ll outline three scenarios where organizations can use flow data to diagnose IT issues that would be challenging for traditional infrastructure monitoring tools.
As an addendum, we’ll also discuss how flow monitoring can enhance an organization’s security posture by helping surface cybercriminal activity on the network if a cybersecurity attack has bypassed perimeter defenses.
The Whole Business Needs Visibility
In today’s hyperconnected business world, it is imperative that applications are always available and responsive. A problem of the latter kind is often a worse issue than an application being unavailable because offline applications are easy to spot. Your infrastructure monitoring tool’s display dashboard will probably turn red, and there will be email and SMS alerts to the IT team.
But performance issues are more insidious than offline applications, and they not only impact the productivity of users, they also degrade the trust in the IT team. When apps are slow, it’s very frustrating for end-users, but for IT it’s often hard to find any issues. It’s the dreaded “it works fine for me” problem.
If you are a CTO or other executive charged with IT delivery, you don’t want to have trouble identifying IT performance issues and fixing them as quickly as possible. Fielding calls from department heads or the CEO about why the IT systems are ‘broken’ will put a dampener on your day. Existing infrastructure monitoring tools are great for alerting IT teams when a piece of equipment, application, or service is down, but they are not very useful for pinpointing problems when users complain that “the system is slow!”
Fortunately, there is a solution to plug this monitoring gap in the form of network traffic monitoring and analysis with flow data that can give you real network visibility.
Flow Monitoring Supercharges Troubleshooting
Capturing flow data and using flow monitoring techniques to analyze it is a powerful addition to the IT operations toolbox. The information provided via these techniques allows the quick pinpointing of any issues impacting the application experience.
Let’s briefly look at three common troubleshooting scenarios ranging from simple to complex and see how flow data availability can quickly pinpoint and resolve issues.
Scenario 1
The Helpdesk gets reports that the Internet is slow at an office location. Infrastructure monitoring tools show a significant spike in network traffic on a network interface, but nothing more.
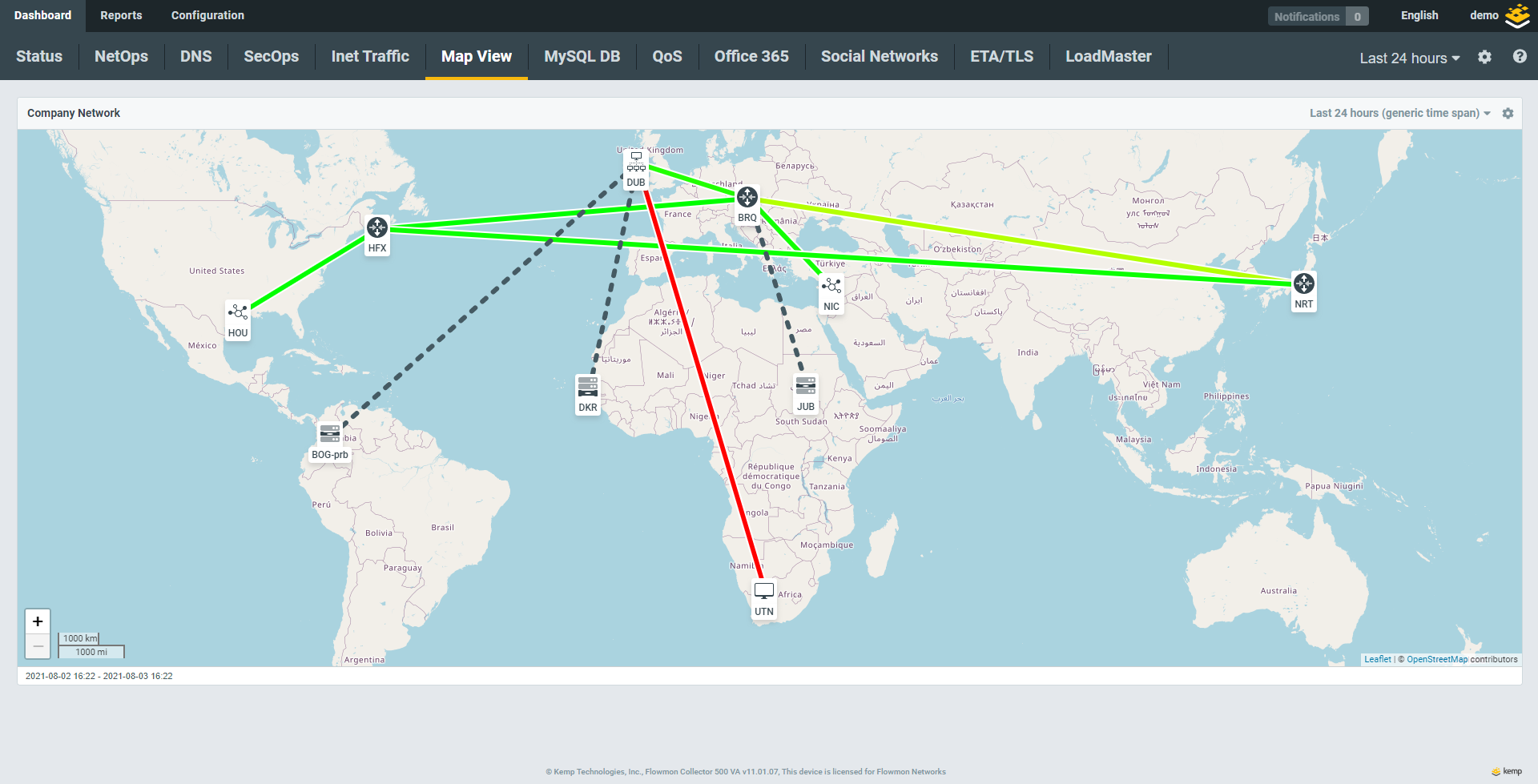
However, even basic flow data monitoring will immediately show you what device is responsible for the traffic spike and allows you to identify the communication protocol; in this case it was a PC downloading large media files from the Internet via BitTorrent..
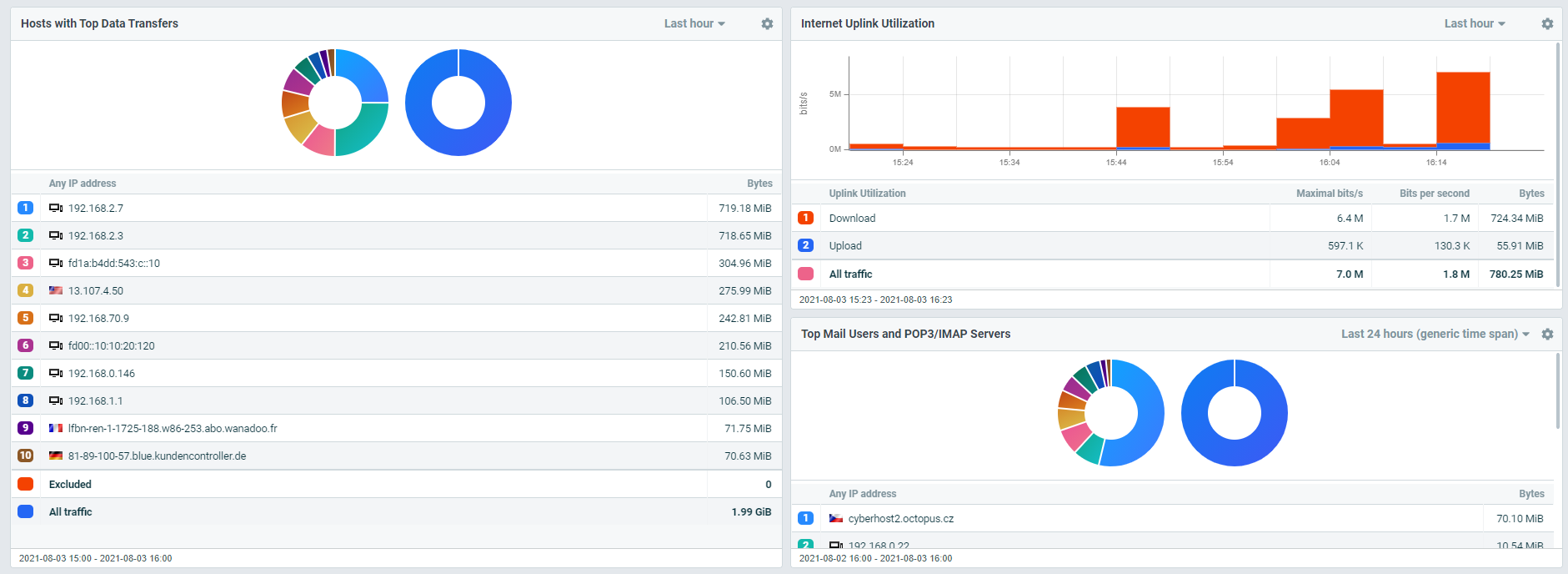
Scenario 2
Expected data transfers between a new branch site and a central storage system in a data center are not working. Although both systems appear up and fully functional according to the standard monitoring tools, querying the flow data for both systems show zero traffic passing between them.
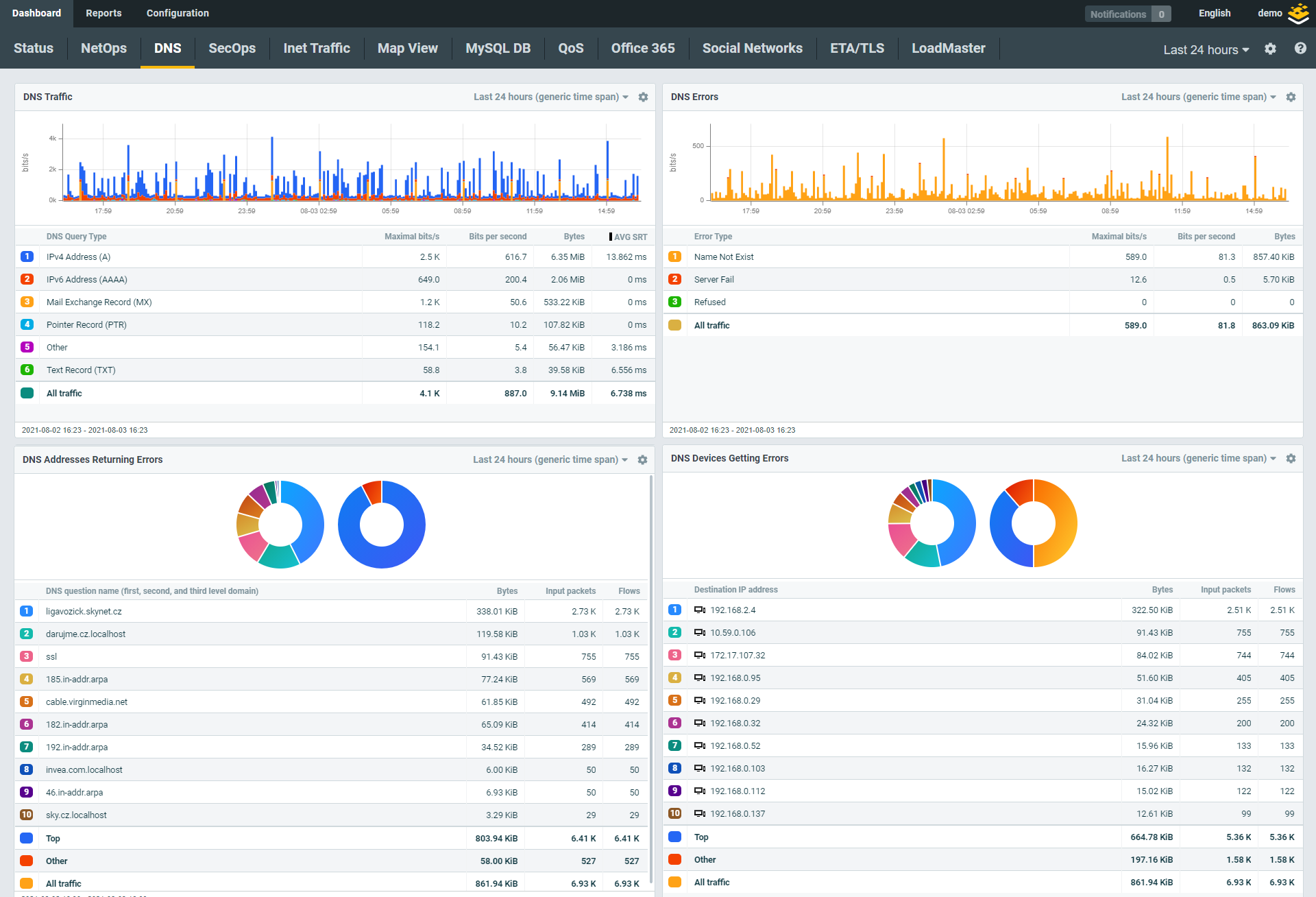
To get to the bottom of this problem, you need more detailed data, such as L7-enriched IPFIX flows from a Kemp Flowmon Probe.
By drilling down into the communication, you’ll see that someone had configured the remote server with incorrect DNS settings, and it couldn’t resolve the IP address of the storage server in the data center. Flow data monitoring will capture DNS errors and allow you to diagnose and fix these types of issues quickly.
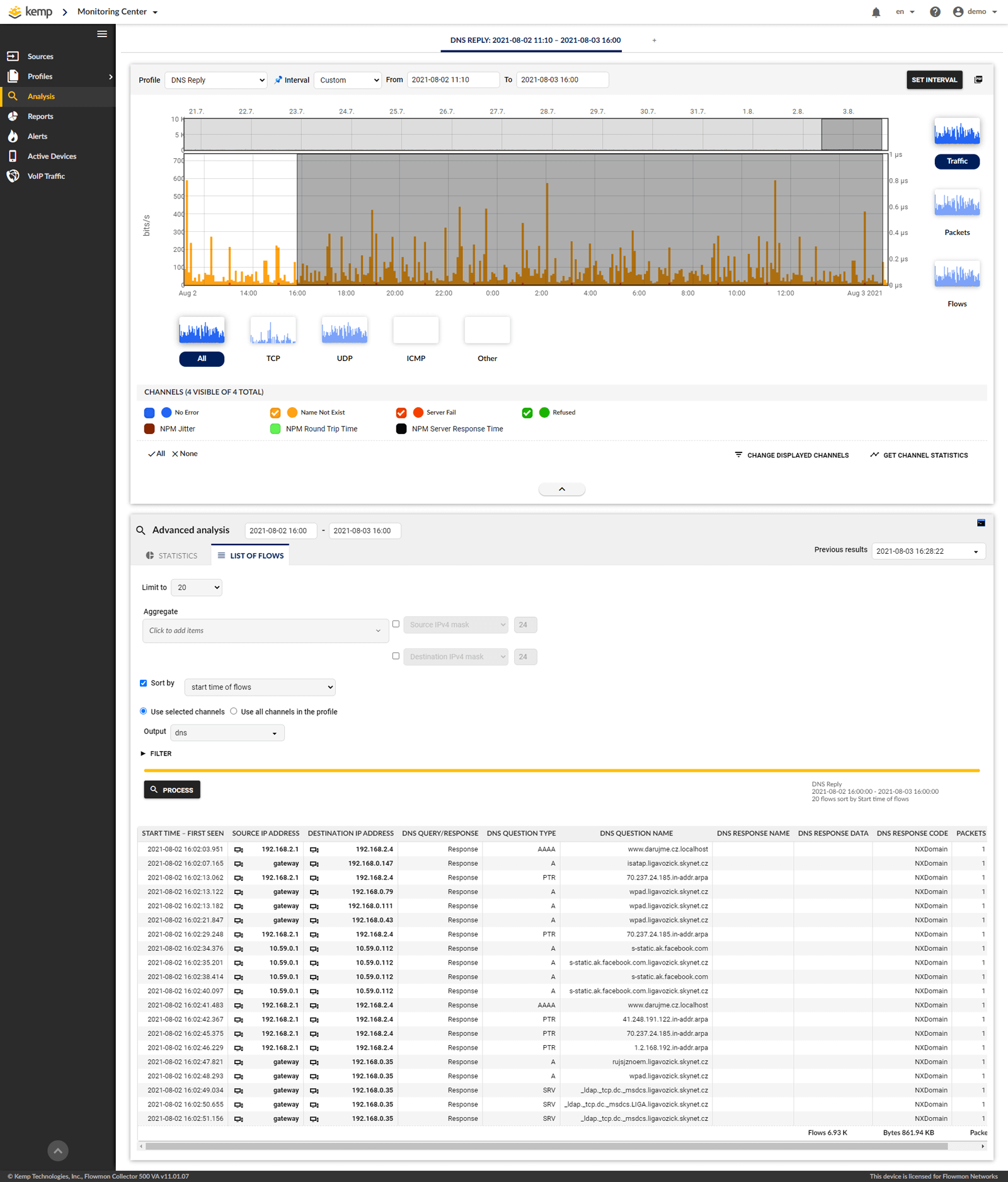
Scenario 3
A third-party application vendor performs an upgrade of a web application and its backend database schema. Shortly after the updated system goes back into production users report that it feels slower than before. The vendor does some checks but says that there is nothing wrong with the application and it must be a network problem.
But the network team can refer to network-based NPM metrics generated by a Kemp Flowmon Probe and thus are able to prove the fault is indeed with the vendor by comparing metrics from before and after the upgrade.
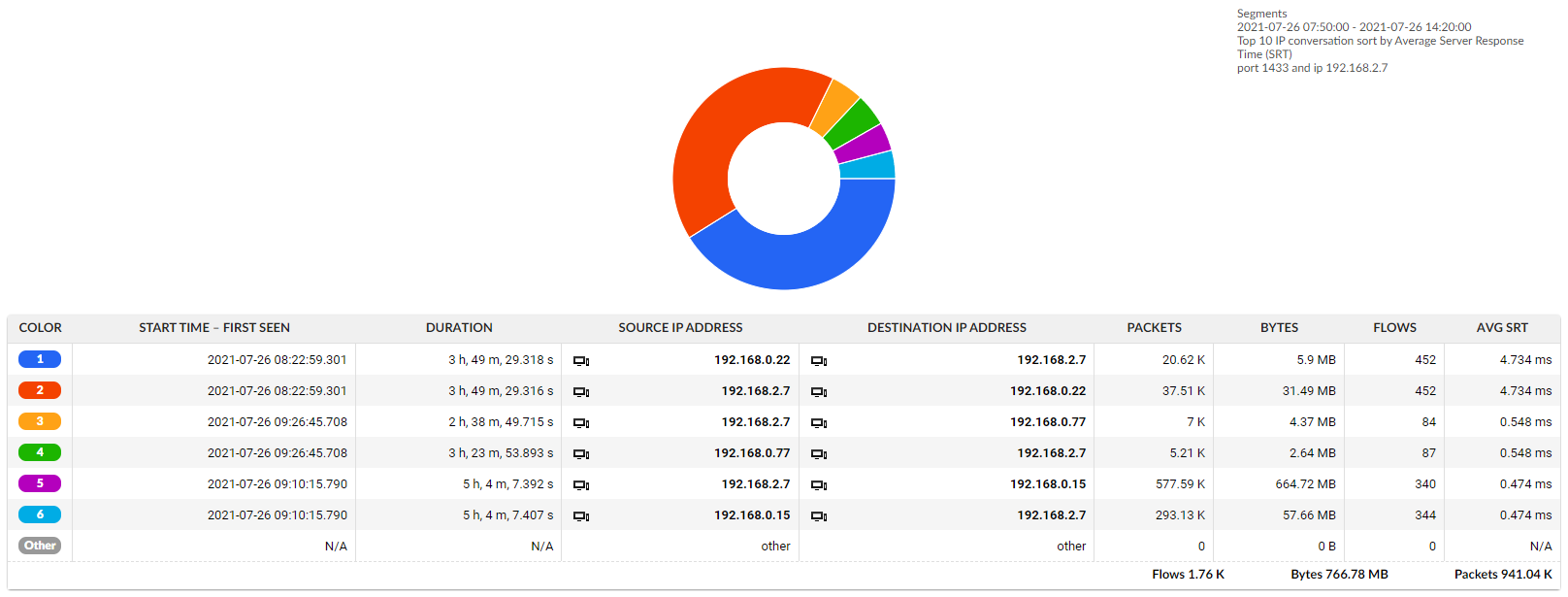
The vendor can now see that SQL queries are returned more slowly on the database server, so the slowdown is not due to the network.
These scenarios are simplified, but there is a webinar on YouTube if you want to go into the technical details of each and how flow data capture and monitoring work.
Cybersecurity Enhancement with Flow Data Monitoring
Flow data analysis can also help detect suspicious activity if there is a cybersecurity breach. Even with the best defenses in place, it’s only a matter of time before some attacker finds an entry point.
Dwell time before discovery after cybercriminals have breached defenses is often measured in months. Flow data monitoring and analysis can reduce this dwell time dramatically.
The behavior analysis engine built into Kemp Flowmon bridges the gap between perimeter defenses and endpoints on the network. It can alert about unexpected network activity such as sudden data transfers from the network to Internet locations, a common symptom of an impending ransomware attack. Often cybercriminals copy data to sell on the dark web or to use to blackmail an organization after encrypting their data.
Conclusion
Collecting and analyzing flow data will significantly improve the overall picture that organizations have of their networks and the application experience that users are getting. It will also reduce the troubleshooting and resolution time when issues occur.
Kemp LoadMaster and Flowmon combine to deliver a solution that provides enhanced cybersecurity and a better application experience. Whether you are building on an existing Kemp LoadMaster deployment, a Flowmon Collector with the Anomaly Detection System deployed, or starting from scratch, deploying these tools together will enhance and simplify your network and application delivery operations.

Pavel Minarik
View all posts from Pavel Minarik on the Progress blog. Connect with us about all things application development and deployment, data integration and digital business.
more from the author