Enabling TLS 1.2 on Exchange Server 2013 & 2016 – Part 1

Transport Layer Security (TLS) is a cryptographic protocol that is used to secure communication over a network. The latest specification is TLS 1.2 as defined by the Internet Engineering Task Force (IETF) who control the protocol. TLS is the successor to the Secure Sockets Layer (SSL) cryptographic protocol and provides stronger security.
TLS has mostly replaced SSL. If you are still running SSL as your cryptographic protocol, you should plan to move to TLS as soon as possible. If you are already on TLS but are not running TLS 1.2, then you should also plan to upgrade as quickly as possible. There are known vulnerabilities in TLS 1.0 and TLS 1.1 that the latest version addresses while also improving security generally. Many popular services are now enforcing TLS 1.2 for all access and integration services to provide the maximum cryptographic protection. Microsoft Office 365 will enforce TLS 1.2 from October 2018, and any hybrid Exchange organizations with mailboxes spread across on-premise and Office 365 will stop communicating id the on-premise Exchange servers are not using TLS1.2.
Note that it is possible to enable the use of TLS 1.2 on Exchange Server while still having TLS 1.0 and TLS 1.1 enabled and used for communications to other servers during a transition period. Once all servers and services are configured to use TLS 1.2, then the support for the previous versions of TLS can be disabled.
Enabling TLS 1.2 on Exchange Server 2013 & 2016
To enable the use of TLS 1.2 on Exchange Server 2013 & 2016 requires configuration changes to both the host Windows Server platform and the Exchange Server application. The following tables show the TLS versions support and status for Microsoft’s operating systems:
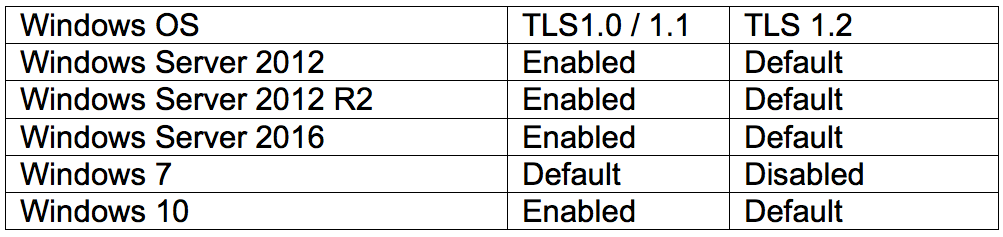
Microsoft Exchange support and status for TLS versions is shown in the next table:
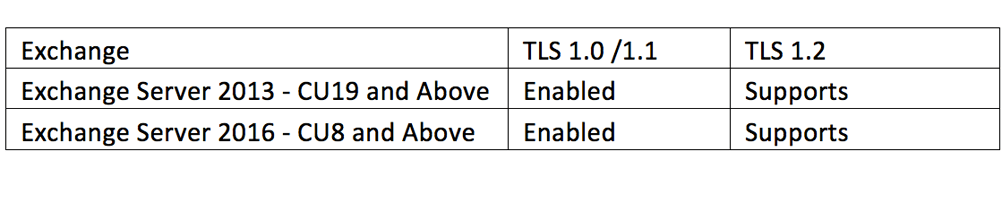 Before anything else make sure to deploy all the latest Windows Server and Exchange Server security patches. Once this is done the following three sets of registry changes need to be made if not already in place.
Before anything else make sure to deploy all the latest Windows Server and Exchange Server security patches. Once this is done the following three sets of registry changes need to be made if not already in place.
Schannel
This is a Windows Server component used to provide identity security checking and authentication to enable secure, private communications through encryption. It relies on the cryptographic protocol in place. To ensure that Schannel uses TLS make sure these registry keys are set:
1. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2 2. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client “DisabledByDefault”=dword:00000000 “Enabled”=dword:00000001 3. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server “DisabledByDefault”=dword:00000000 “Enabled”=dword:00000001
WinHTTP
WinHTTP provides a high-level server interface to the HTTP/1.1 Internet Protocol that applications and services running on Windows Server can use when establishing secure encrypted HTTPS sessions. Exchange uses it extensively. To ensure that WinHTTP is using TLS 1.2 make sure the following Registry keys are set:
1. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp “DefaultSecureProtocols”:dword:00000a80
2. HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp “DefaultSecureProtocols”:dword:00000a80
.NET Framework
The .NET Framework is a core set of code libraries and runtimes that are used by many Windows Server-based services and Applications, including Exchange Server. It’s essential to ensure that the .NET Framework is using TLS 1.2 to encrypt and secure the many API points it provides and uses to communicate. To do this makes sure the following registry keys are set:
1. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 “SystemDefaultTlsVersions”=dword:00000001
2. HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319 “SystemDefaultTlsVersions”=dword:00000001
Client Machines
In addition to configuring all Exchange and other servers to use TLS 1.2, its vital that clients are also configurated to use the latest version so that clients communicate with Exchange Servers in the most secure and encrypted manner.
Next Steps
When all Servers and Clients are using TLS 1.2, it will be possible to disable the support for TLS 1.0 and TLS 1.1. This will take planning to ensure access to some services isn’t broken when the previous versions of TLS are disabled. Part 2 of this article outlines how to disable the previous version of TLS to just leave TLS 1.2 in place, when you are ready to take that step. Read part 2 of this post here

Kurt Jung
Kurt Jung is a Senior Technical Marketing Engineer at Kemp Technologies. He works hands on with many technologies around application delivery and how to position these in today’s market. Kurt also works closely with key alliance partners to further strengthen the synergy. Prior to Kemp, Kurt has spent most of his career working as a consultant helping customers deploy on-premises, cloud and hybrid cloud solutions to support their business.
more from the author