Many organizations have legacy applications in use that are delivering essential business functionality. But many of these applications cannot use modern security features available to those built on current technology stacks or in the cloud.
But this doesn’t mean that they can’t be secured. Using a layer-based cybersecurity model and existing infrastructure such as the Kemp LoadMaster load balancer provides methods that can secure legacy applications and raise the overall cybersecurity posture of an enterprise organization. Legacy app security is a critical part in preserving application functionality for apps that perform essential operations within your organization while actively securing the ecosystem.
I share in a recorded webinar on how to use the Kemp LoadMaster load balancer beyond its core load balancing functionality to secure legacy applications. I touch on multiple ways LoadMaster can participate in an overall layered defense strategy. But the focus of my talk is on three core components: Web Application Firewall (WAF), Pre-Authentication via the LoadMaster to secure log on, and Zero-Trust via the LoadMaster for legacy app application security.
You can watch the video below or via our BrightTALK page.
Read on for a high-level summary of the points I outline in the video. I do recommend you take the time to watch the 25-minute webinar — it is time well spent.
The Current Cybersecurity Landscape
The threats organizations face from cybercriminals and cyberattacks are forecast to grow. With the growth building on an already high level of attacks, Gartner estimates “30% of critical infrastructure organizations will experience a security breach that will result in the halting of an operations or mission-critical cyber-physical system” by 2025.
Many other organizations running line of business systems outside of the critical infrastructure sector will fare no better. Many of the systems in use are legacy applications that are providing essential services but are running on older technology stacks that no longer receive security updates.
All organizations should have a plan to replace legacy systems, but this will take time and considerable expense. For many, they will be projects that stretch for years, but cybersecurity protection needs to apply to legacy applications in the interim. Yes, I’m talking about the need for legacy app security.
The modern approach to cybersecurity uses a layered technique that protects systems and data at multiple points, such as the network perimeter, on network infrastructure, via servers and other host systems, in applications, and for the data (both at rest and in transit over networks). There is no single tool that can provide cybersecurity across all layers. Instead, a range of solutions that work harmoniously is required.
The LoadMaster load balancer can provide enhanced security for legacy applications at multiple layers. I summarize three solutions for legacy app security in the webinar.
Web Application Firewall
Kemp’s Web Application Firewall (WAF) helps to protect your custom and off-the-shelf applications from common vulnerabilities, such as SQL injection and cross-site scripting (XSS). It lets you create per-application security profiles to enforce source location-level filtering, adopt pre-integrated rulesets for common attack vectors (including the OWASP ModSecurity Core Rule Set), and provides custom security rules support. Using a combination of rule types, you can protect all your applications within Kemp LoadMaster.
The protection covers known web attacks and prevents specific traffic patterns from reaching your applications without changing your application or infrastructure. Kemp WAF can also help meet PCI-DSS and data loss prevention (DLP) compliance requirements. It also provides granular per-application event logging, in-UI statistic visualization, and false-positive analysis with rich telemetry to third party SIEMs providing comprehensive visibility of running applications.
 The diagram above shows where WAF on LoadMaster logically sits within a typical application deployment infrastructure. Organizations will likely have legacy applications deployed in virtual machines in the data center location shown in the diagram. LoadMaster and WAF sit between the applications and clients using them, mediate access requests, inspect traffic, and provide security via predefined rule sets and customs rules.
The diagram above shows where WAF on LoadMaster logically sits within a typical application deployment infrastructure. Organizations will likely have legacy applications deployed in virtual machines in the data center location shown in the diagram. LoadMaster and WAF sit between the applications and clients using them, mediate access requests, inspect traffic, and provide security via predefined rule sets and customs rules.
Pre-Authentication
An area where legacy applications are weak is in user authentication. LoadMaster can bridge any gaps in built-in authentication by providing pre-authentication services that control access higher up on the access path. The LoadMaster authentication functionality allows access to legacy applications using modern authentication methods without modifying the applications themselves — a capability not possible for many legacy applications. Using LoadMaster, you can make use of the following authentication techniques with legacy (and modern!) applications:
- LDAP
- Radius
- RSA-SecurID
- SAML
- Certificate Authentication
- OIDC/OAuth
- Kerberos
- Multi-Factor Authentication
In addition to these, the LoadMaster authentication functionality integrates with Microsoft 365 authentication and Azure AD. Microsoft has validated this integration, and organizations who are starting to use AD Federation and Azure AD can now use accounts that are in AD via LoadMaster to authenticate users to legacy applications alongside modern ones.
Zero Trust
Finally, I share how LoadMaster can help deliver a zero-trust approach to cybersecurity. In zero-trust, every connection to the network is treated as potentially hostile no matter where it originates. All connection types require the same level of security, and movement from one system to another needs separate authentication to gain access.
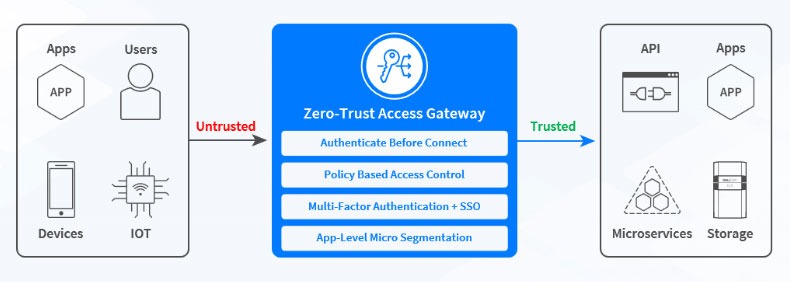 Zero-trust access uses a Who, What, and Where classification that grants access based on predefined policies. LoadMaster operates as a zero-trust access gateway, which provides granular security to deliver zero-trust principles such as least privileged access and restricting lateral movement throughout the network. Doing so allows access to legacy applications to be restricted based on the need to access within your organization. All traffic to the application flows through the LoadMaster, and invalid access requests get dropped.
Zero-trust access uses a Who, What, and Where classification that grants access based on predefined policies. LoadMaster operates as a zero-trust access gateway, which provides granular security to deliver zero-trust principles such as least privileged access and restricting lateral movement throughout the network. Doing so allows access to legacy applications to be restricted based on the need to access within your organization. All traffic to the application flows through the LoadMaster, and invalid access requests get dropped.
Conclusion
This summary provides a high-level overview of my webinar. Take the time to watch it, and if you have any questions, reach out to your Progress Kemp contact, or use our contact page to get in touch.

