The Kemp Technologies LoadMaster includes a Web Application Firewall (WAF). With this functionality, LoadMaster becomes a critical part of a Security Information and Event Management (SIEM) system that helps protect networks against the OWASP Top 10 and other threats (for example Cross-Site Scripting, Cross-Site Request Forgery, SQL Injection etc).
One aspect of a SIEM system is the deployment of tools to analyze network device logs in real-time. In this way, suspicious activity and known threats that leave well-known signatures in logs can be spotted, and system administrators alerted quickly. Automated responses can often be triggered to counter attacks in real-time.
Real-time log analysis is a way to help achieve this, and Kemp LoadMaster logs are ideally suited for this purpose. Due to its logical position on the network, LoadMaster inspects all the Layer 4 and Layer 7 traffic flowing to and from websites and application servers. All this activity is recorded in the LoadMaster logs. These can be passed to dedicated threat monitoring tools for analysis, and any suspicious activity can be identified. Best practice says that the logs should be sent off from the network device that collects them and analyzed remotely. LoadMaster can send its logs to various industry standard tools, from relatively simple Syslog collectors to more sophisticated analysis tools such as SIEM systems.
Real-time analysis of the logs from LoadMaster, as part of a complete system of network security, can help identify attacks quickly. This allows preventative measures to be triggered and reduces the risk of a compromised system and data breaches.
This blog details the format of the JavaScript Object Notation (JSON) logs that the LoadMaster Web Application Firewall (WAF) produces and demonstrates how those logs can be exported in real-time from the LoadMaster and provided to log data endpoints including:
From Figure 1, the WAF JSON format logs are selected on the LoadMaster and the appropriate settings are configured. As you will see in the videos, a proxy like LogStash, can assist as the intermediator between the LoadMaster and log data endpoints.
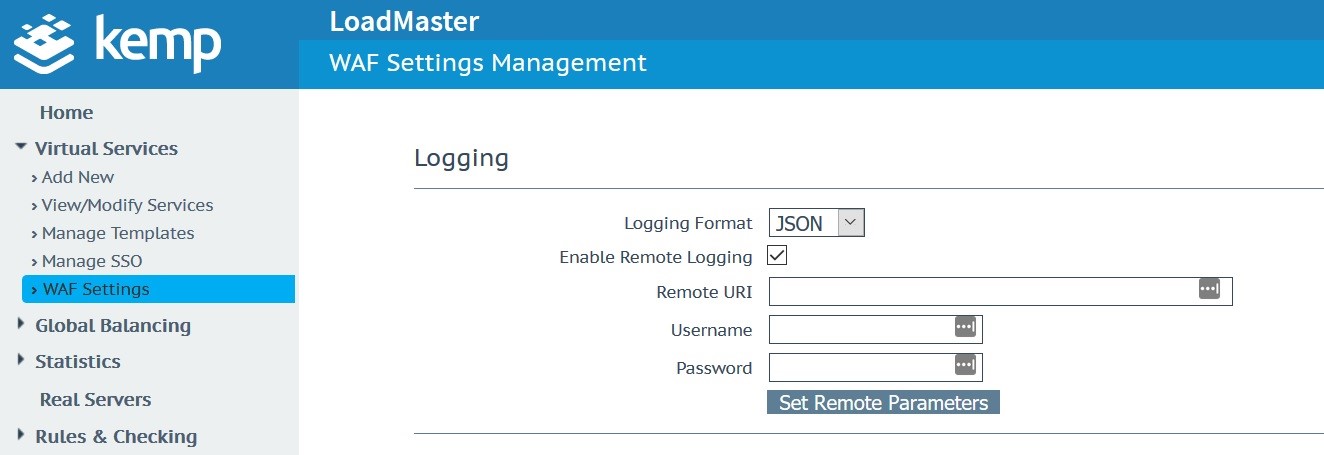
The Kemp Technologies LoadMaster provides logs in the ModSecurity Native and JSON formats. These formats are full described:
This blog solely deals with the ModSecurity JSON format logs (native format logs would be handled similarly).
The JSON format logs are sent to the log data endpoint over HTTP as shown in Figure 2. This is a standard trace taken from the LoadMaster and viewed in Wireshark.
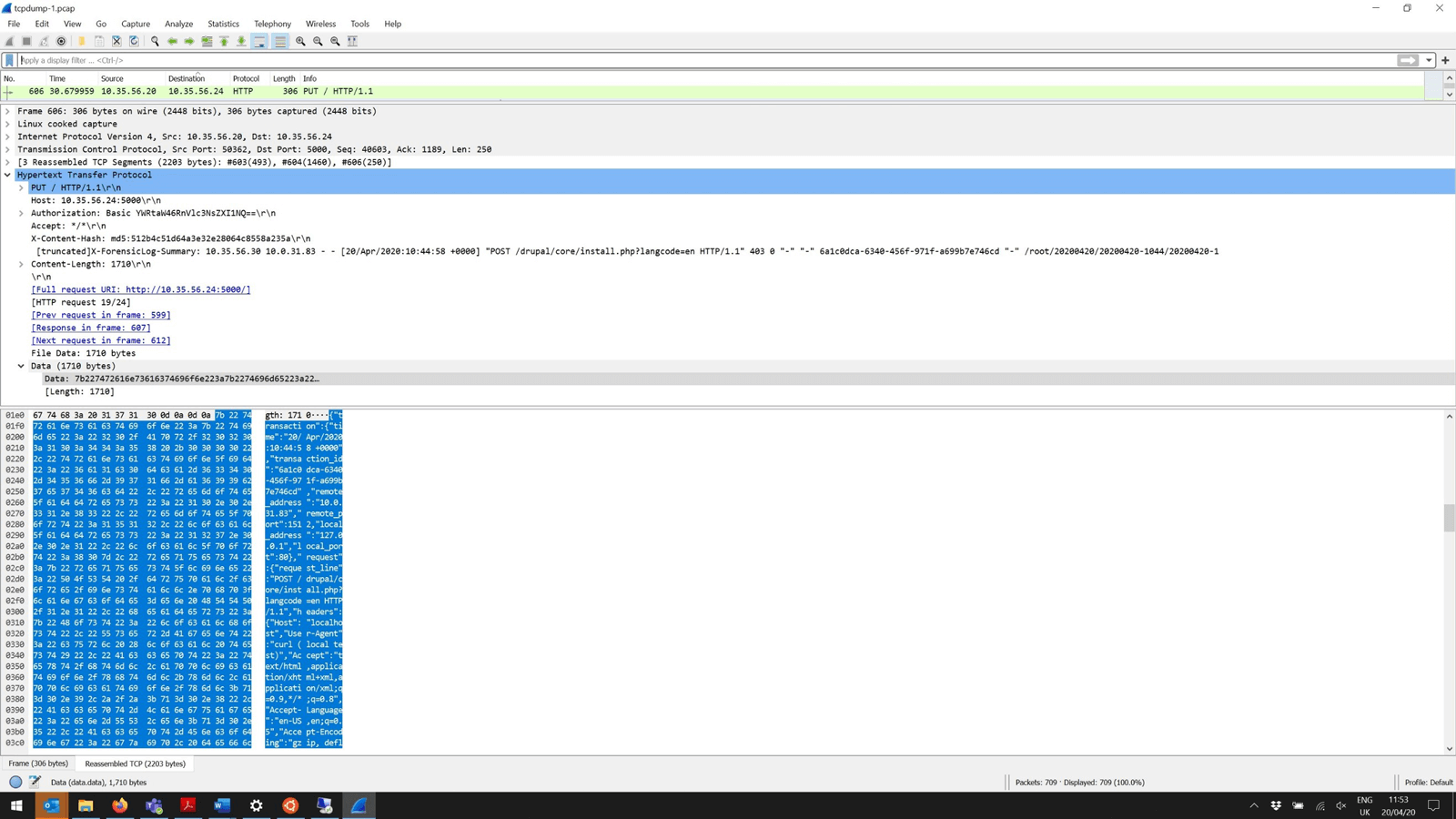
JSON Format Logs
The parts of the native audit log format are mapped to a JSON Schema with the following blocks:
- Transaction
- Request
- Uploads (optional)
- Response
- Matched rules
- Audit data
The individual blocks correspond with individual audit log parts in the native format, as described here.
Transaction (transaction)
The transaction part corresponds with the native audit log part A.
Request (request)
The request part corresponds with the native audit log part B together with part C.
Uploads (uploads)
The uploads part corresponds with part J in the native audit log format. It’s optional and only available if the transaction includes file uploads.
Response (response)
The response part corresponds with the native audit log part F together with part E.
Matched Rules (matched_rules)
The matched rules part corresponds with part K in the native audit log format.
Audit data (audit_data)
The audit data part corresponds with the native audit log part H.
The full format of the JSON audit log format is available in Chapter 20 of the ModSecurity Handbook, 2nd Ed., available here.
The full videos are available:
- ElasticSearch / Kibana (Please see short video here)
- Azure Sentinel (Please see short video here)
Based on my personal experience, Kemp provides the best load balancers with the widest platform support in the industry, specifically for virtual / software and hardware deployments. A key part of our holistic application delivery strategy includes the mitigation of application-specific vulnerabilities. We continue to expand on our application-centric offerings by providing key security features and services that allows customers to enable secure access to web-based applications.
Contact us today to discuss all your application delivery and security needs.
References
https://github.com/SpiderLabs/ModSecurity/wiki/ModSecurity-2-Data-Formats https://www.feistyduck.com/books/modsecurity-handbook/ https://www.wireshark.org/

