Herding Cats: How to Mitigate GhostCat Vulnerability (CVE-2020-1938)

Sometimes that’s how it feels when it comes to security vulnerabilities, herding the organizational cats to understand the latest security vulnerability and respond in a timely and appropriate manner. Typically, these security vulnerabilities are targeted to exploiting the end user applications either to exploit customer credentials or to take control of the application or infrastructure as a backdoor for a broader attack surface.
All network elements have a responsibility to provide an extra layer of security to mitigate any attack. As an example, the Kemp load balancer can be the primary ingress point into a customer’s network for all requests after the firewall. The Kemp load balancer natively blocks ports by default, provides IPS/IDS protection, SSL (with offload and re-encrypt), content rules and filtering, dual-factor authentication, single sign-on, domain filtering and security group validation and a Web Application Firewall (WAF).
An exploit titled GhostCat and tracked as CVE-2020-1938 / CNVD-2020-10487 has been identified when using the Apache JServ Protocol (AJP) when trusting incoming connections to Apache Tomcat. The AJP protocol is enabled by default, listening on TCP port 8089 and bonded to IP address 0.0.0.0. Where the Apache server may be poorly configured, an attacker could upload malicious code to gain remote code execution (RCE). GhostCat was discovered by the Chinese cybersecurity firm Chaitin Tech.
How your load balancer can assist in mitigating vulnerabilities?
Kemp recommends that users patch their Apache implementation to mitigate this vulnerability as their primary response. However, any Kemp load balancer (virtual, cloud, bare metal or dedicated hardware) can provide immediate assistance to mitigate this vulnerability depending on your current deployment model.
New Deployments
Specific to Apache deployments, we recommend the usage of our certified Apache application deployment Template. Using this for publishing Apache virtual services ensures that best practice configurations are applied and non-secure cipher types are disallowed for encryption. Our load balancers ship with a default state of all ports (bar SSH, HTTPS) being closed. Installing the Apache template only makes available the required ports to support your Apache service(s) and stops traffic to the affected port, 8089, as identified in this vulnerability.
The approach is outlined in the following flow:
Download the Kemp Apache template hereImport the template into your Kemp in the “Manage Templates” menu located under “Virtual Services”.
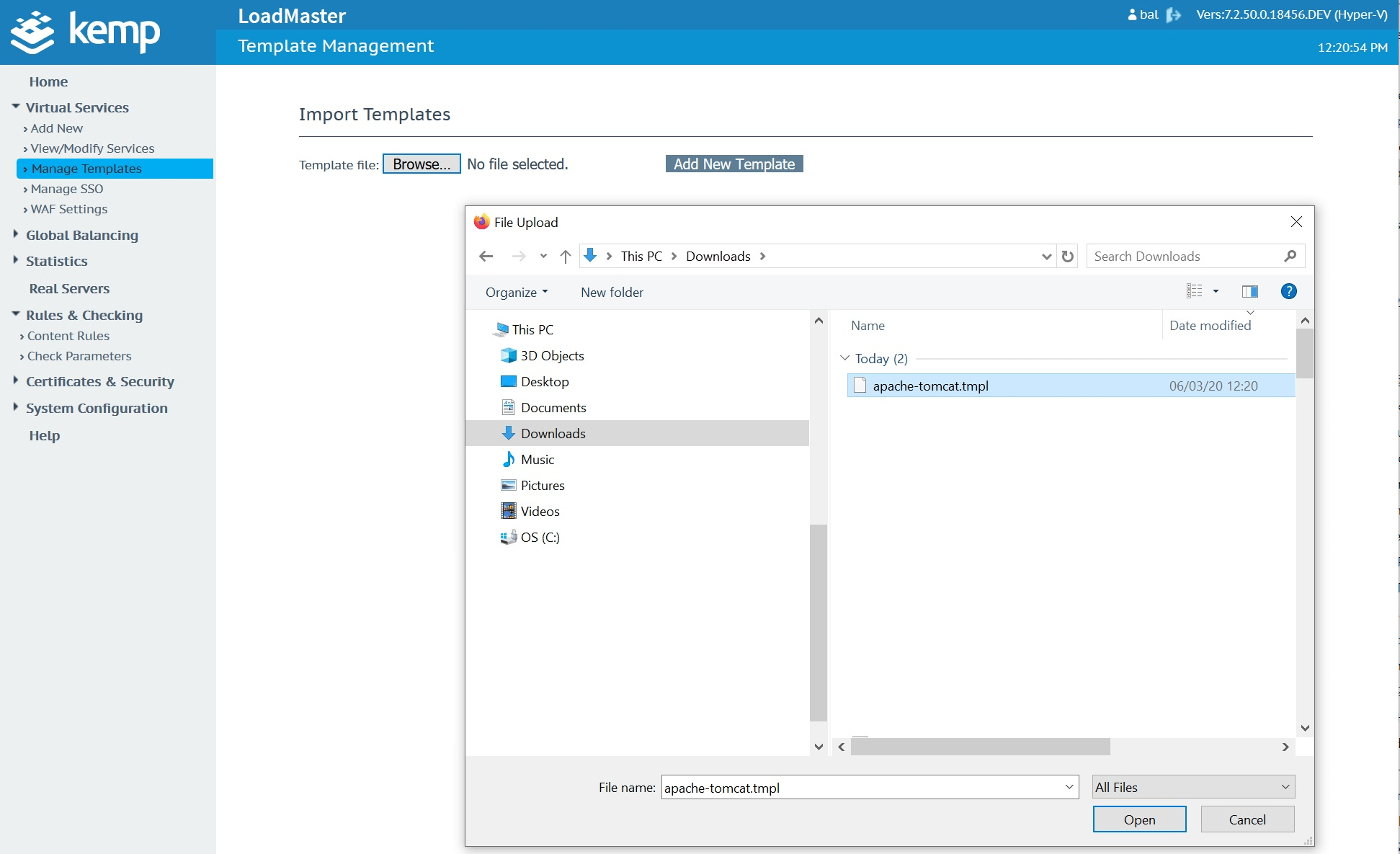
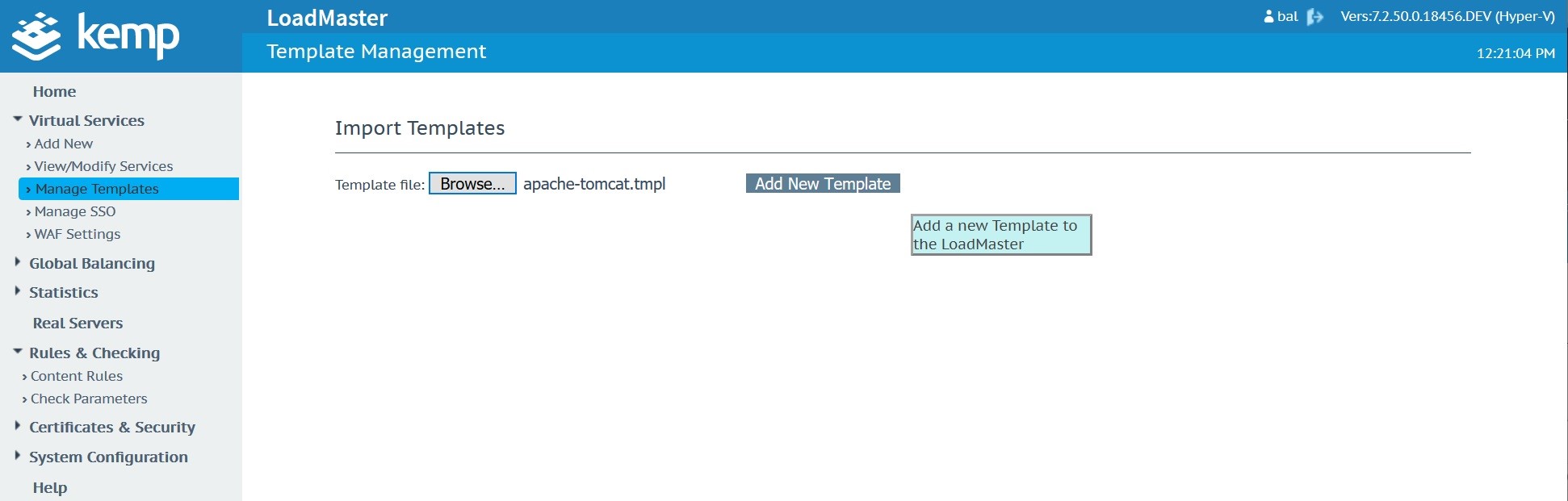
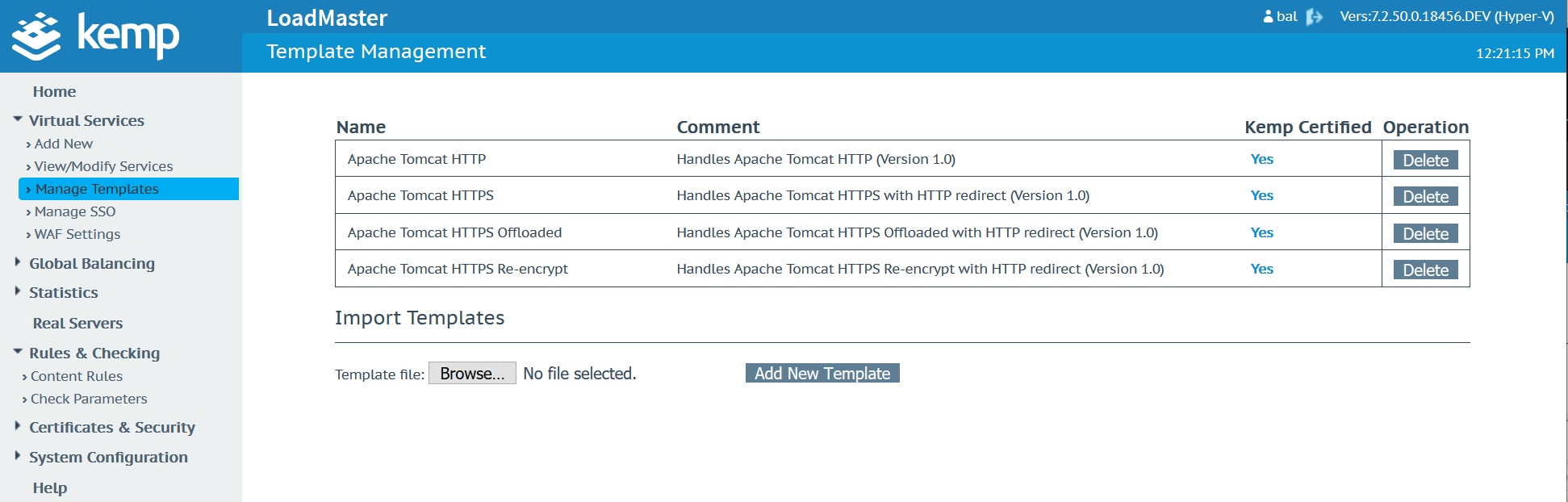
Create and publish your virtual service using Apache template configurations.
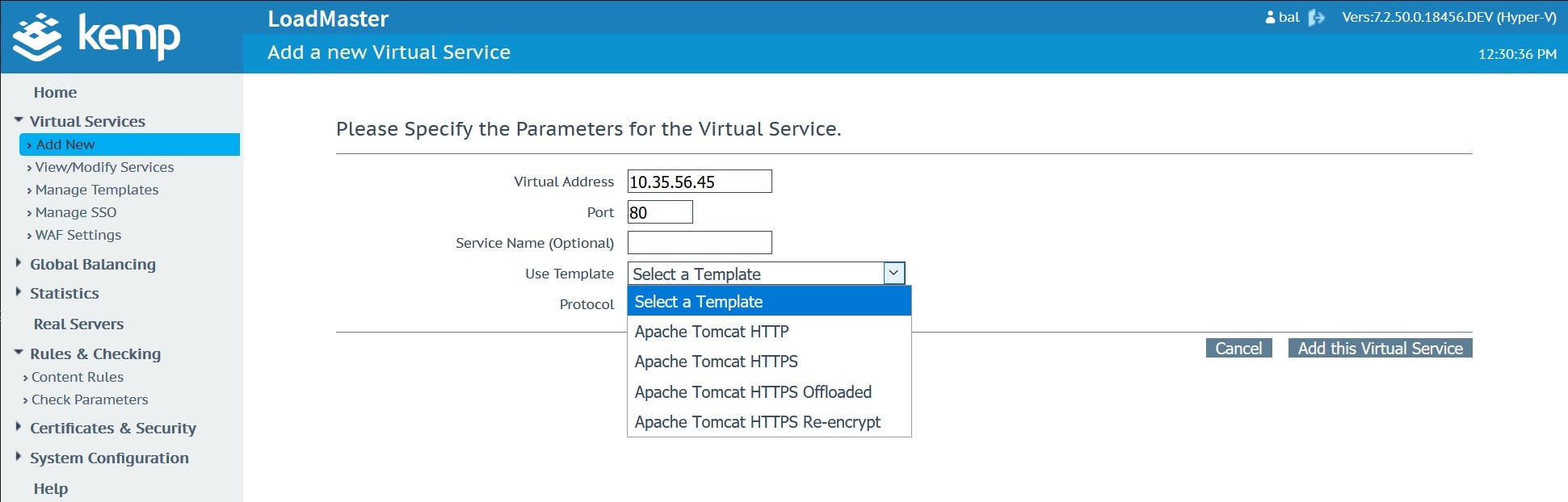
Existing Deployments
In this scenario, where there is a wildcard Virtual Service or port 8089 is open on a Virtual Service in front of an Apache deployment, we recommend the usage of a content rule to disable access to the affected port.
Content rules are essentially load balancer logic, often leveraging regular expressions, that interrogate the heuristics of traffic flows and make steering decisions, content injections or connection interruptions based on that information.
One key configuration consideration is that this approach assumes the use of sub-virtual services, referred to in Kemp’s UI as SubVS. Sub-virtual services enable complex application traffic routing and health checking combinations by putting the backend server targets into sub-groups. Logic and rules can then be applied to steer client requests or fail services based on a variety of logic options.
The approach for addressing the GhostCat vulnerability is outlined in the following flow:
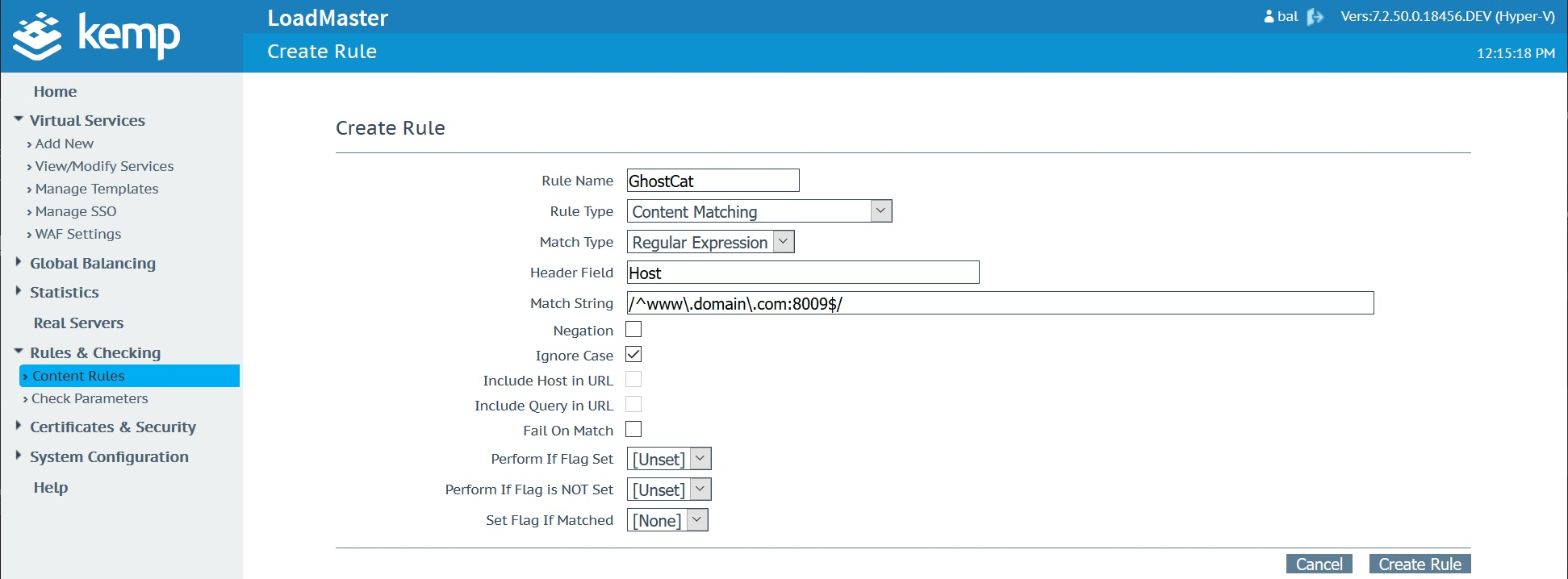
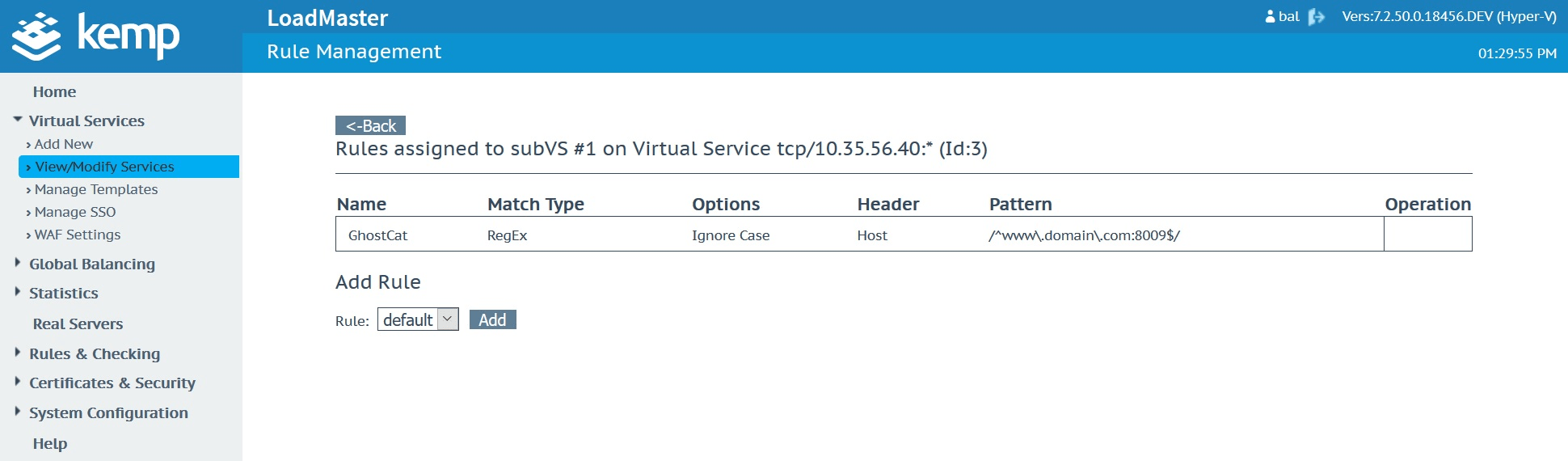
Create a new “GhostCat” rule in the Content Rules menu which you’ll find under “Rules & Checking”. This will need to be a “Content Matching” rule type using the “Regular Expression” match type against the “Host” header field. Use the “Match String” shown in the below screenshot which is basically looking for any attempts to connect to the service it gets applied to on port 8009.
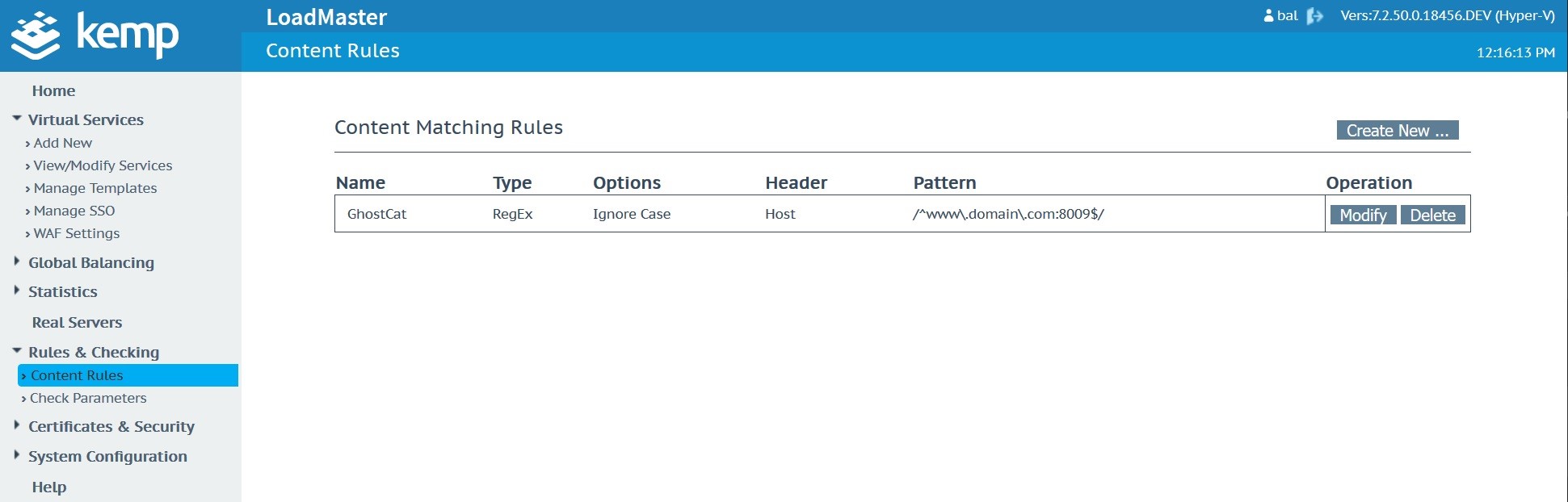
Once created, the rule should look like this when viewed in the “Content Rules” list.
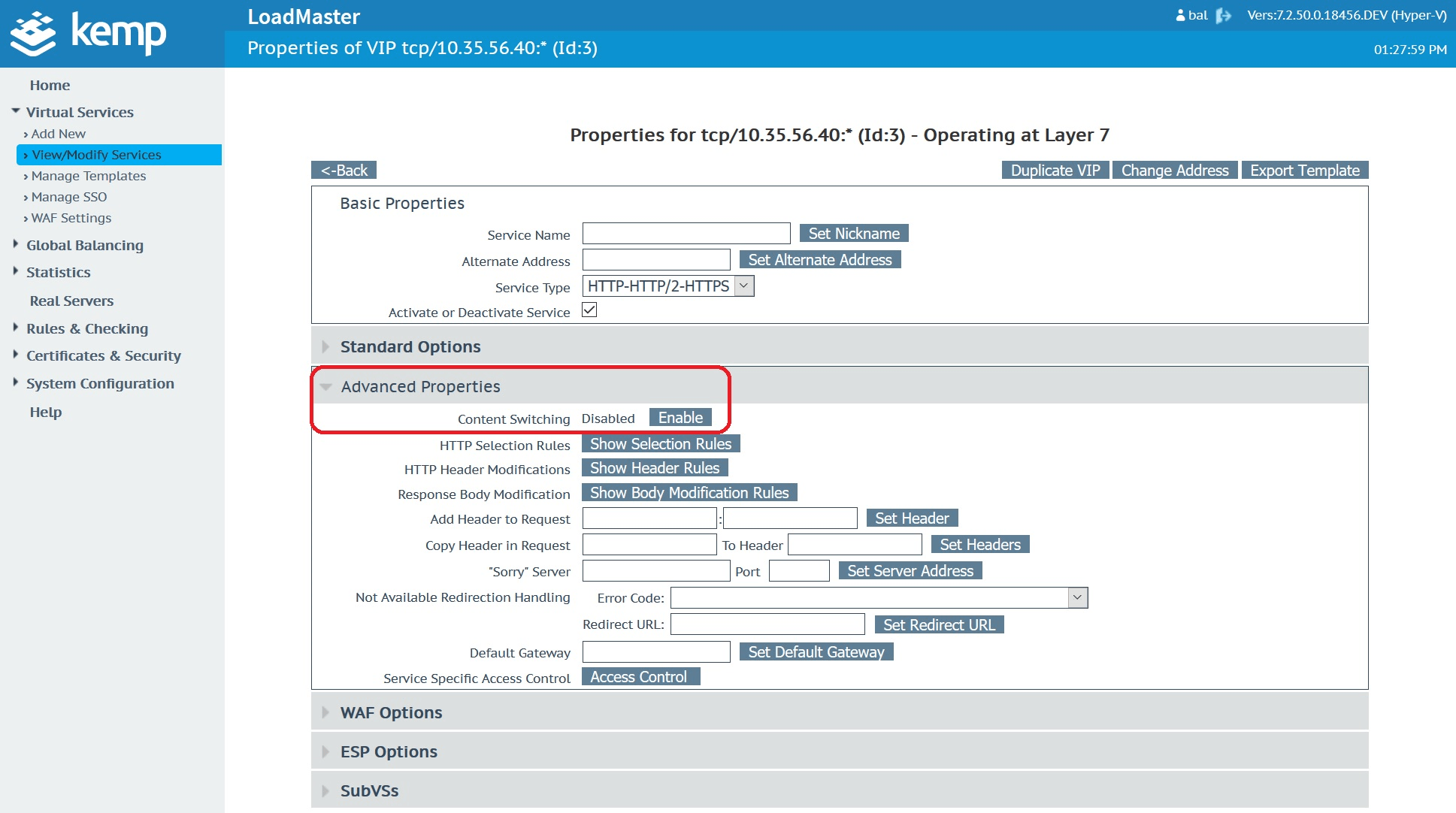
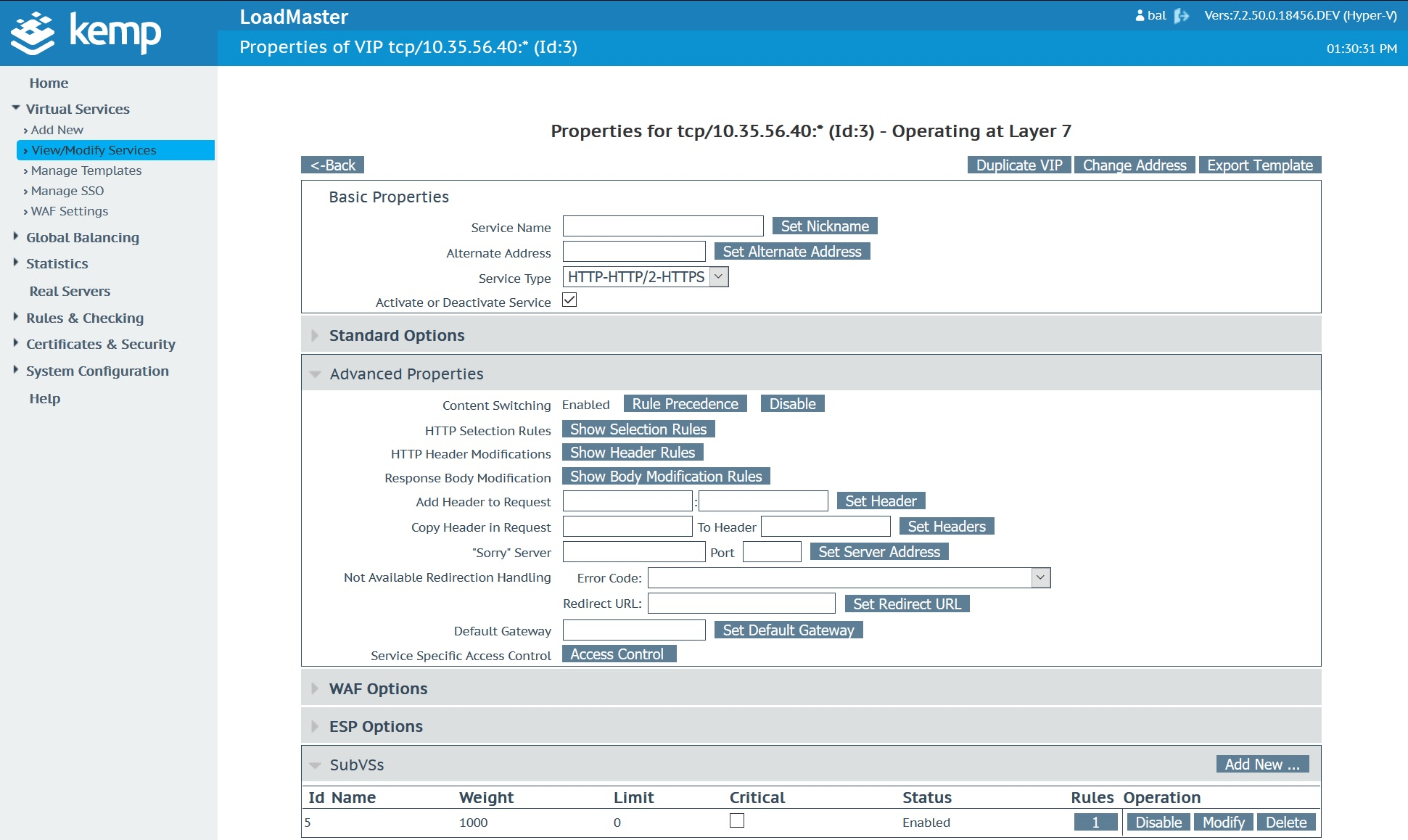
On the virtual service in question, be sure to have content switching enabled. By default, this option is disabled on most service types.
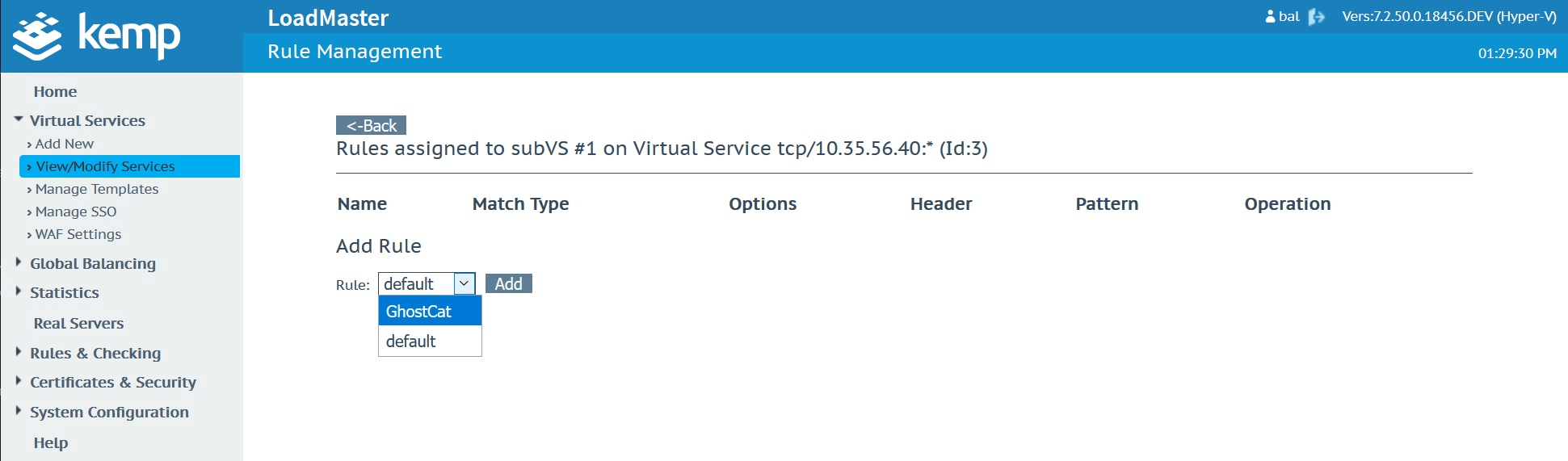
Once content switching is enabled, you’ll now see the option to apply it to your sub virtual service.
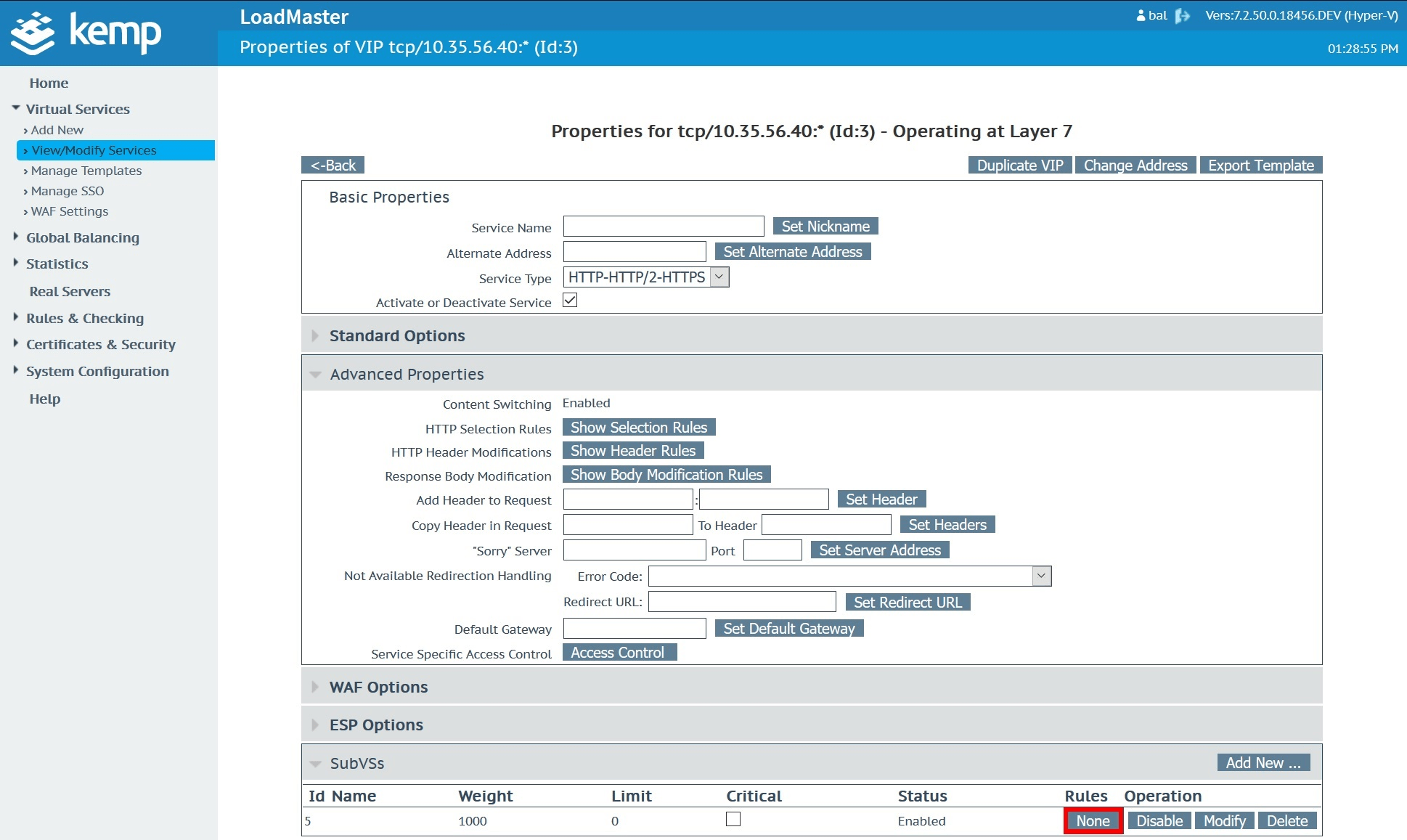
Select and add the GhostCat content rule created earlier to apply it.
Additional information
For additional information about the discovered vulnerability:
Based on my personal experience, Kemp provides the best load balancers with the widest platform support in the industry, specifically for virtual and software deployments. A key part of our holistic application delivery strategy includes the mitigation of application-specific vulnerabilities. We continue to expand on our application-centric offerings by providing key security features and services that allows customers to enable secure access to web-based applications.
We’re committed to resolving security vulnerabilities carefully and quickly. If you think you have found a security flaw in a Kemp product, please inform us at securityalert@kemp.ax Credits for GhostCat image: www.chaitin.cn

David O'Connor
David O’Connor is a Product Manager in Kemp working in Limerick, Ireland. He holds a bachelor’s degree in Computer Engineering from University of Limerick. David has a telecoms background with previous roles in development, customer support and presales with a focus on product-market fit and creating tech products that customers love.
more from the author