How to Protect your Microsoft Exchange Servers From Security Vulnerability CVE-2020-0688

Summary
Microsoft has announced a remote code execution vulnerability in Exchange, CVE-2020-0688. This could allow an unauthenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM. This is a remote code execution vulnerability that exists in Microsoft Exchange software when the software fails to properly handle objects in memory, aka ‘Microsoft Exchange Memory Corruption Vulnerability’.
This is a short blog post for Kemp customers to assist in mitigation of this vulnerability whilst following Microsoft guidelines and best practises to mitigate this vulnerability.
How your load balancer can assist in mitigating vulnerabilities?
Kemp recommends that users patch their Microsoft Exchange implementation to mitigate this vulnerability as their primary response. However, any Kemp load balancer (virtual, cloud, bare metal or dedicated hardware) can provide immediate assistance to mitigate this vulnerability depending on your current deployment model.
Kemp provides two options for remediation actions to mitigate against CVE-2020-688. These are outlined below as:
- Content Rule
- Web Application Firewall (WAF) Rule
Content Rule Recommended Actions
The approach outlined in this flow is to use a content rule to block all external traffic to the Exchange Control Panel (ECP) sub Virtual Service.This approach is based on usage of the Kemp provided Microsoft Exchange template.
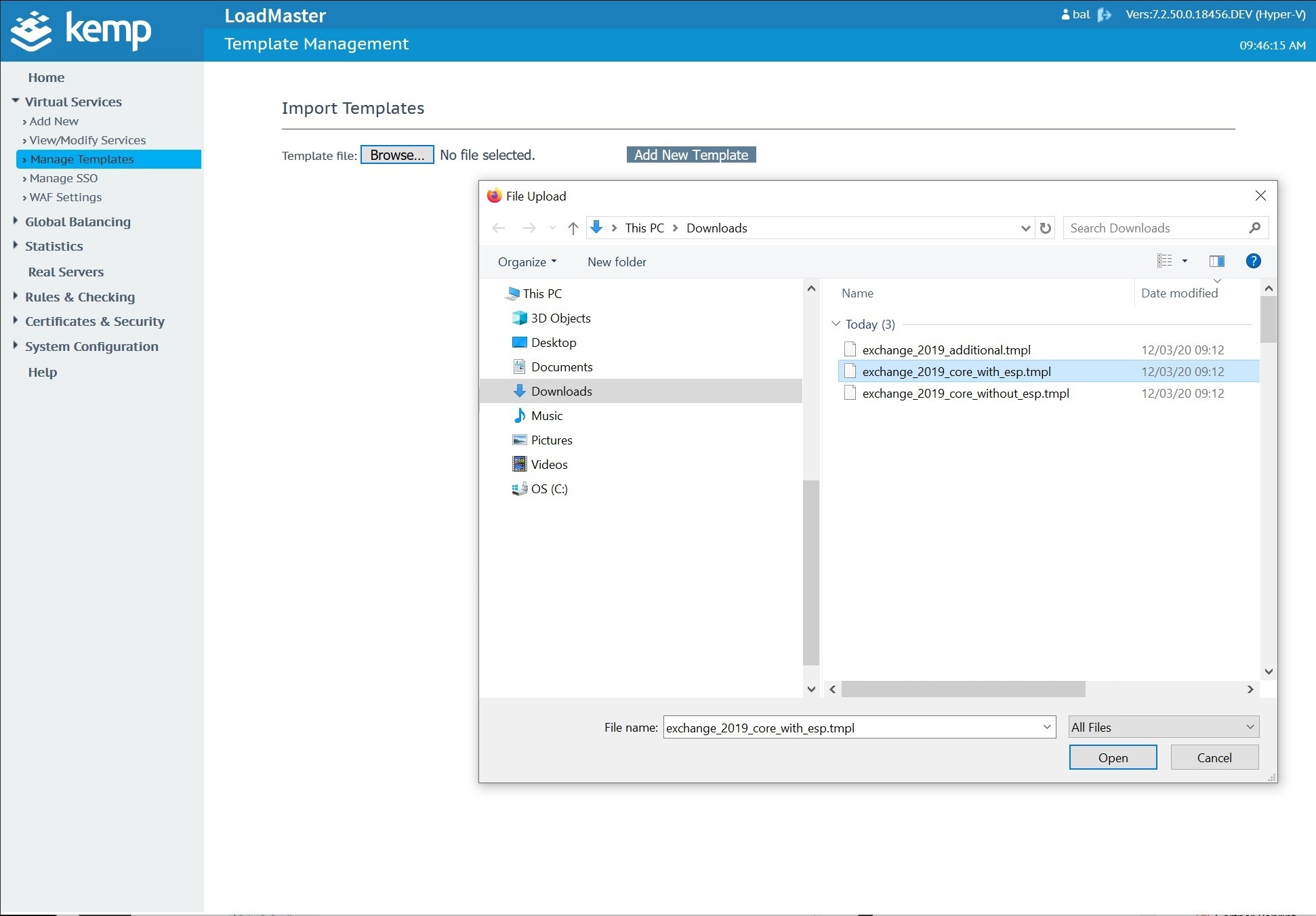
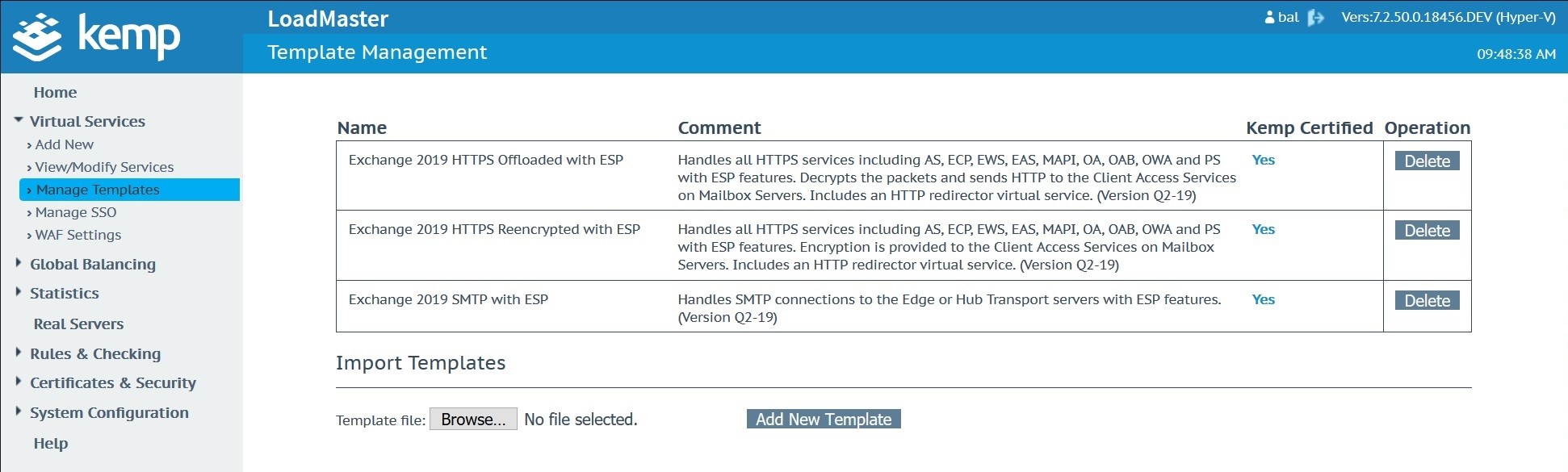
Import the template into your Kemp in the Manage Templates menu located under Virtual Services

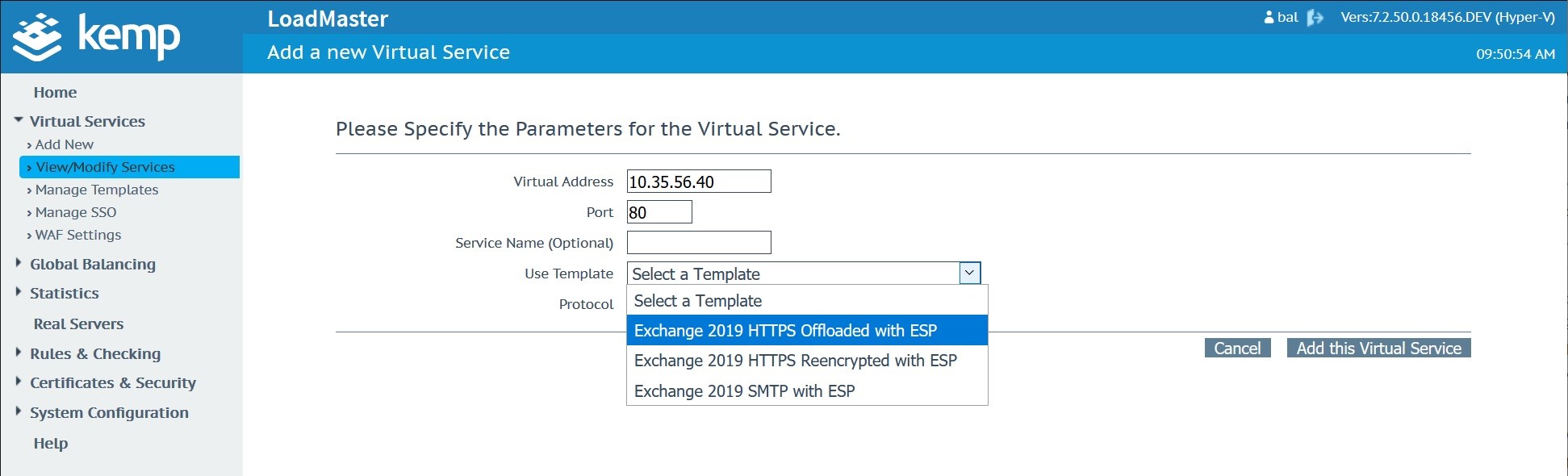
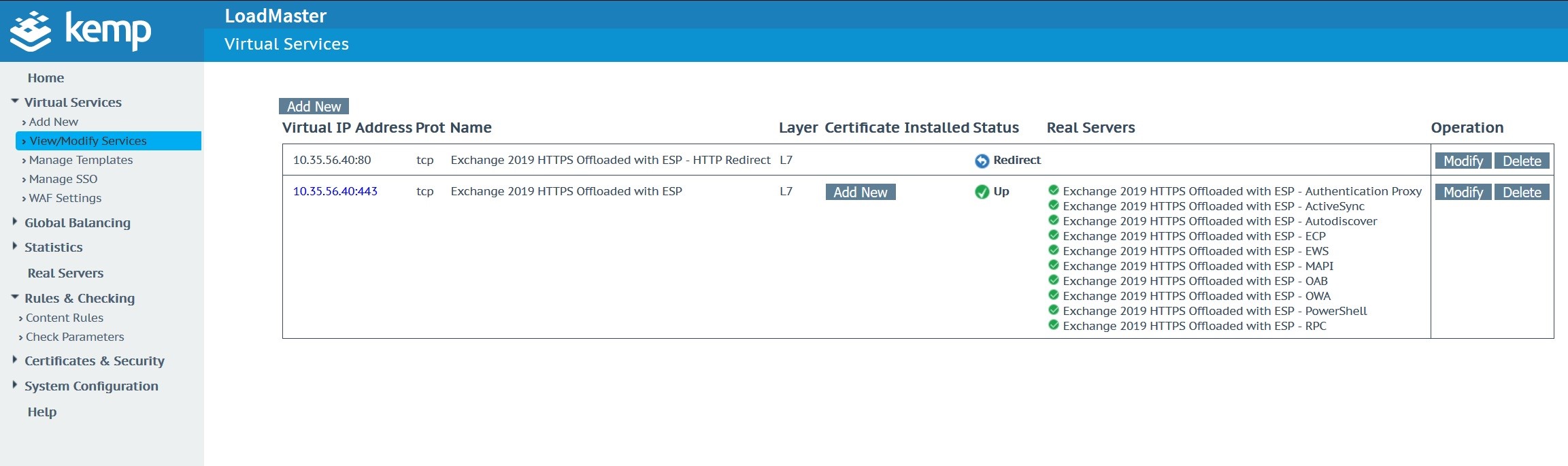
Create and publish your virtual service using Exchange 2019 template configurations
Create a new “CVE20200688” rule in the Content Rules menu which you’ll find under “Rules & Checking”. This will need to be a “Content Matching” rule type using the “Regular Expression” match type against the “src-ip” header field. Use the “Match String” shown in the table below which is basically looking for any attempts to connect to the service from the 192.168.0.1 to 192.168.255.254 IP address range. This would need to be updated to support the internal address range for your specific network.

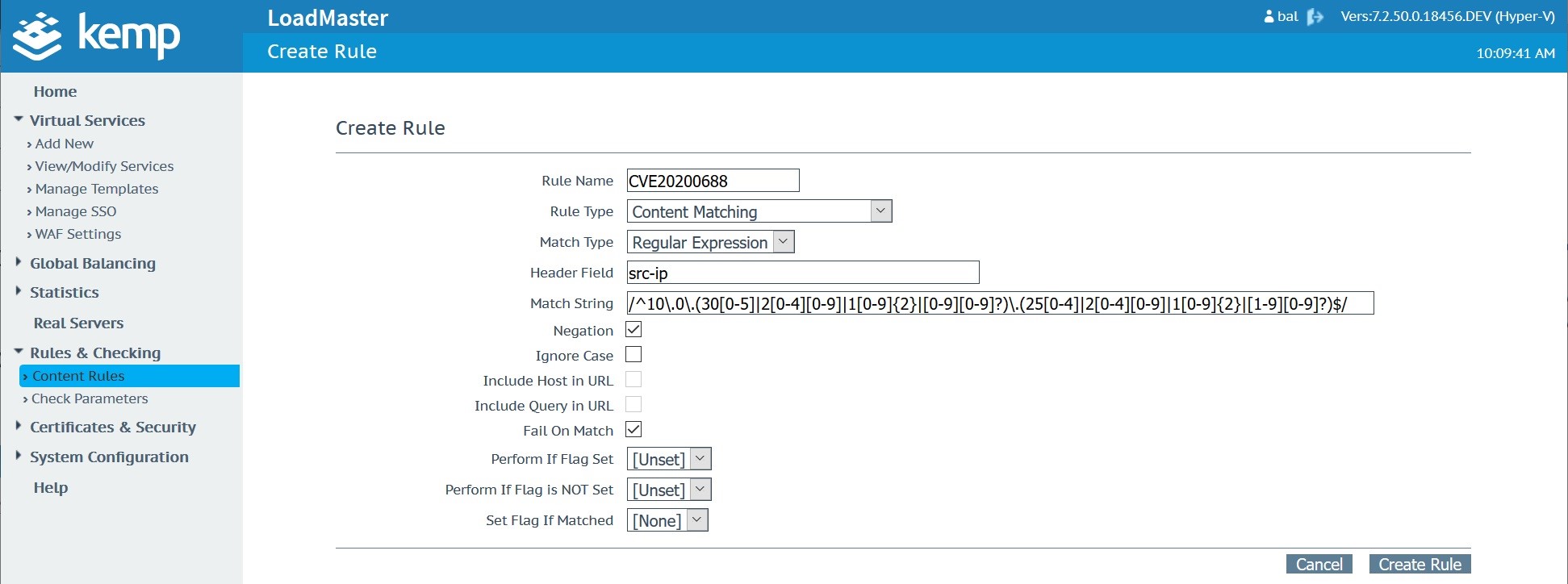
Once created, the rule should look like this when viewed in the “Content Rules” list
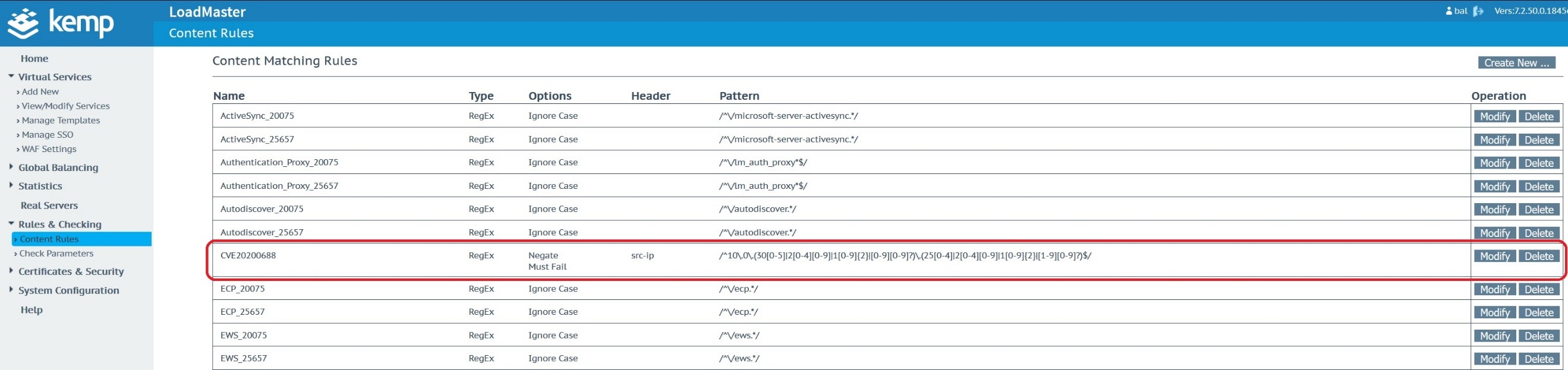
This content rule needs to be applied to the Microsoft Exchange Virtual Service and in specific the sub virtual service ‘Exchange 2019 HTTPS Offloaded with ESP – ECP’.

Select the HTTP Selection Rules for this sub Virtual Service.
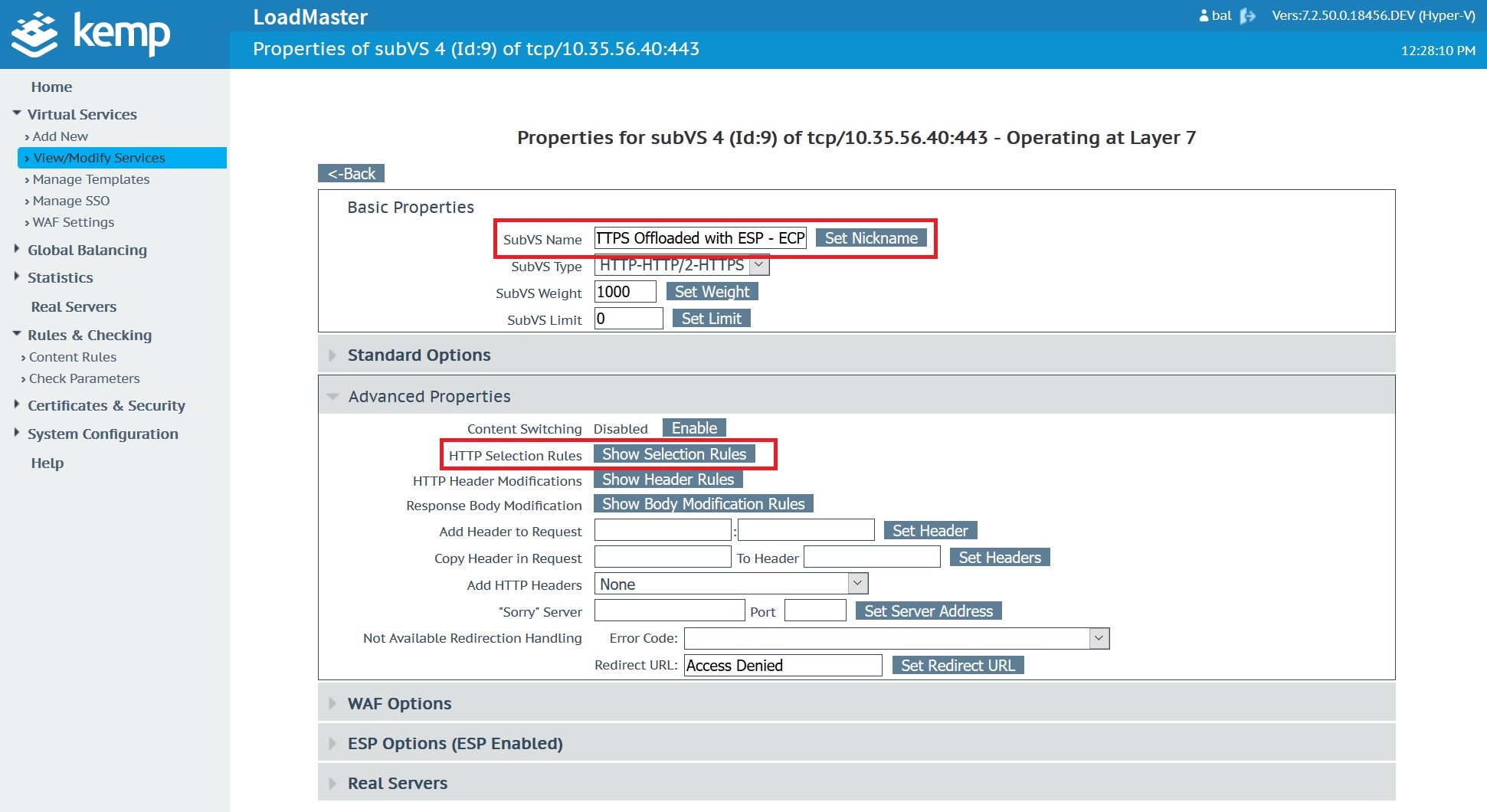
Select and apply the CVE20200688 content rule created earlier to apply it

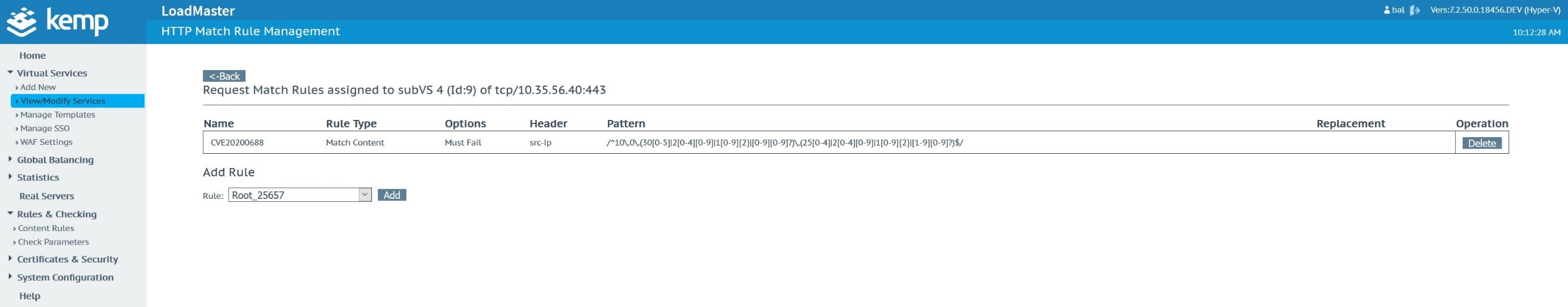
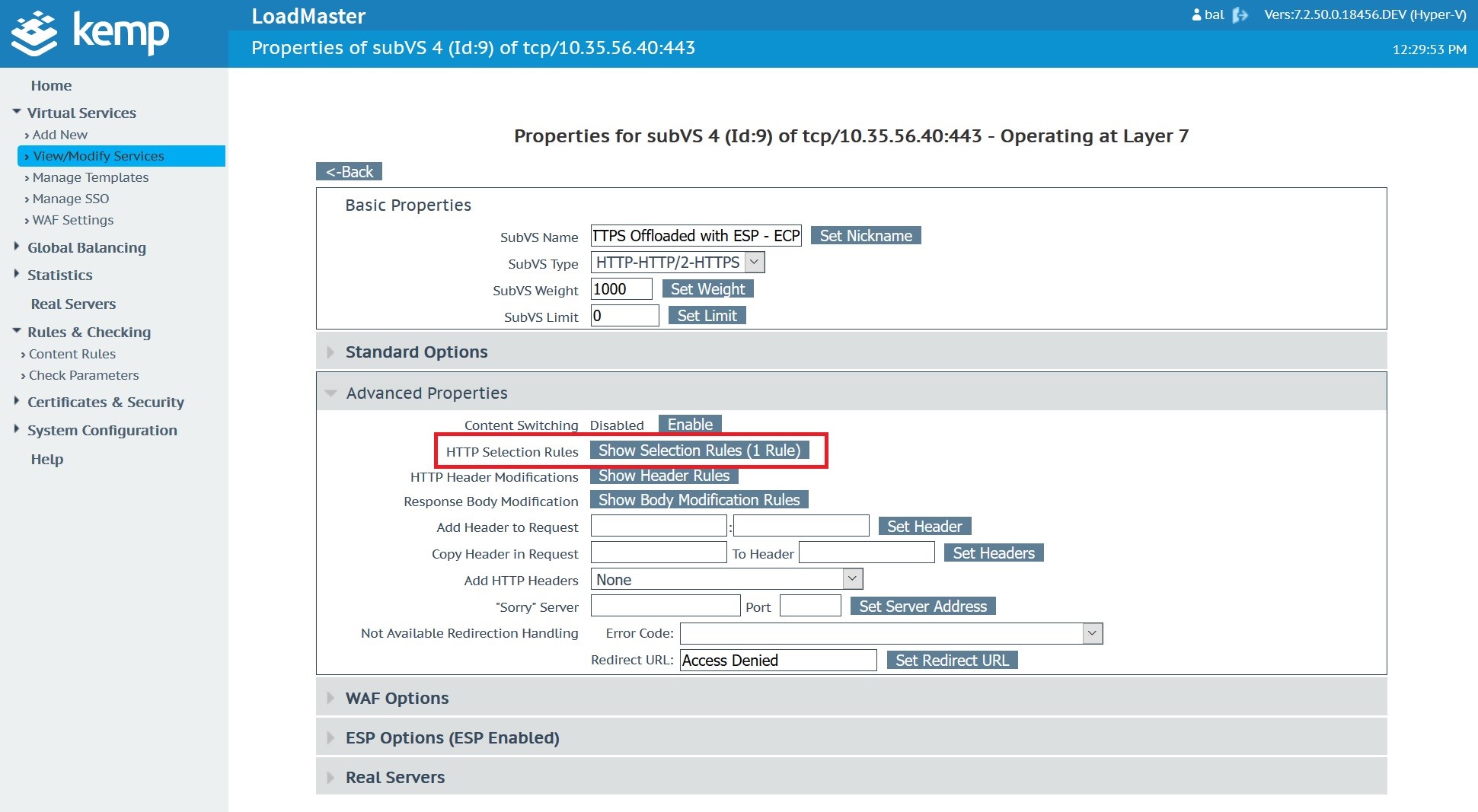
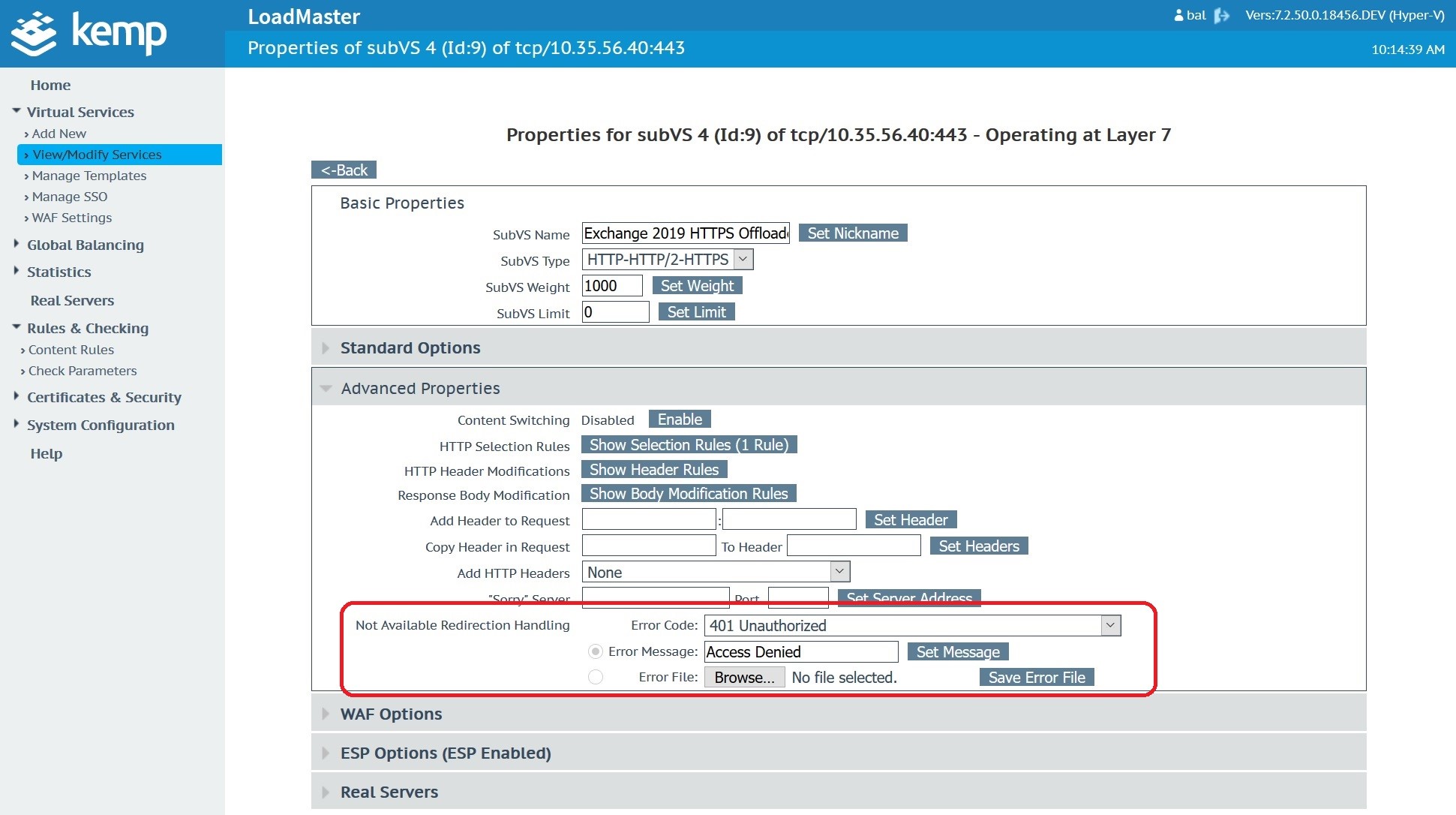
Finally, we add an action to deny access if the Content Rule is triggered.
Web Application Firewall RuleThe approach outlined in this flow is to use a WAF custom rule to block all traffic containing a query string parameter named __VIEWSTATE for Exchange Control Panel (ECP).
The rule was contributed by Christian Folini (@ChrFolini) from netnea.com in Switzerland.
The relevant rule that we need to apply in this scenario is: SecRule REQUEST_URI “@beginsWith /ecp/” “id:10000,\ phase:1,deny,log,msg:’Attack via Microsoft CVE-2019-0688 detected’,chain” SecRule &ARGS_GET:__VIEWSTATE “@gt 0”
This is added to a text file and uploaded to the Kemp Technologies WAF as shown:
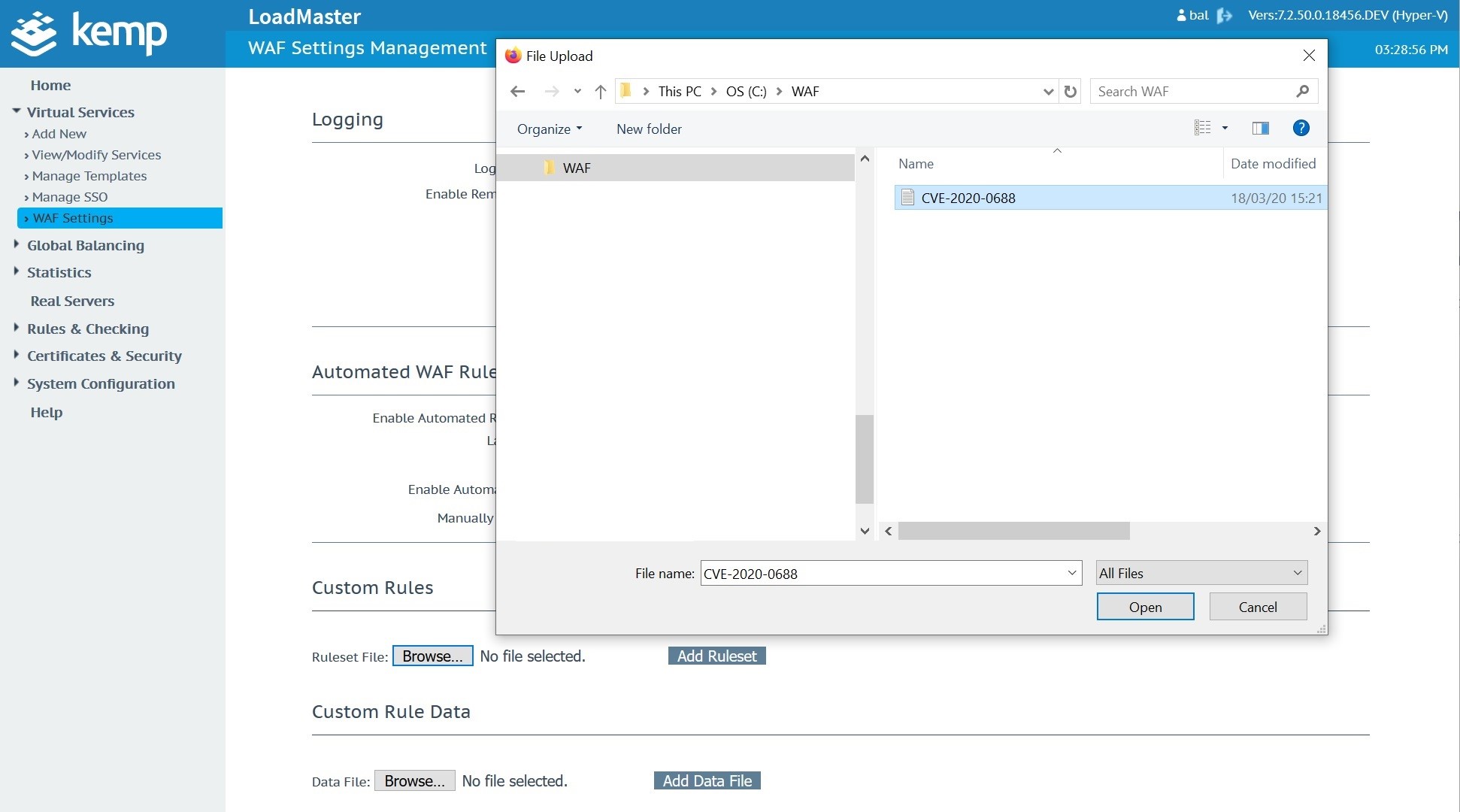
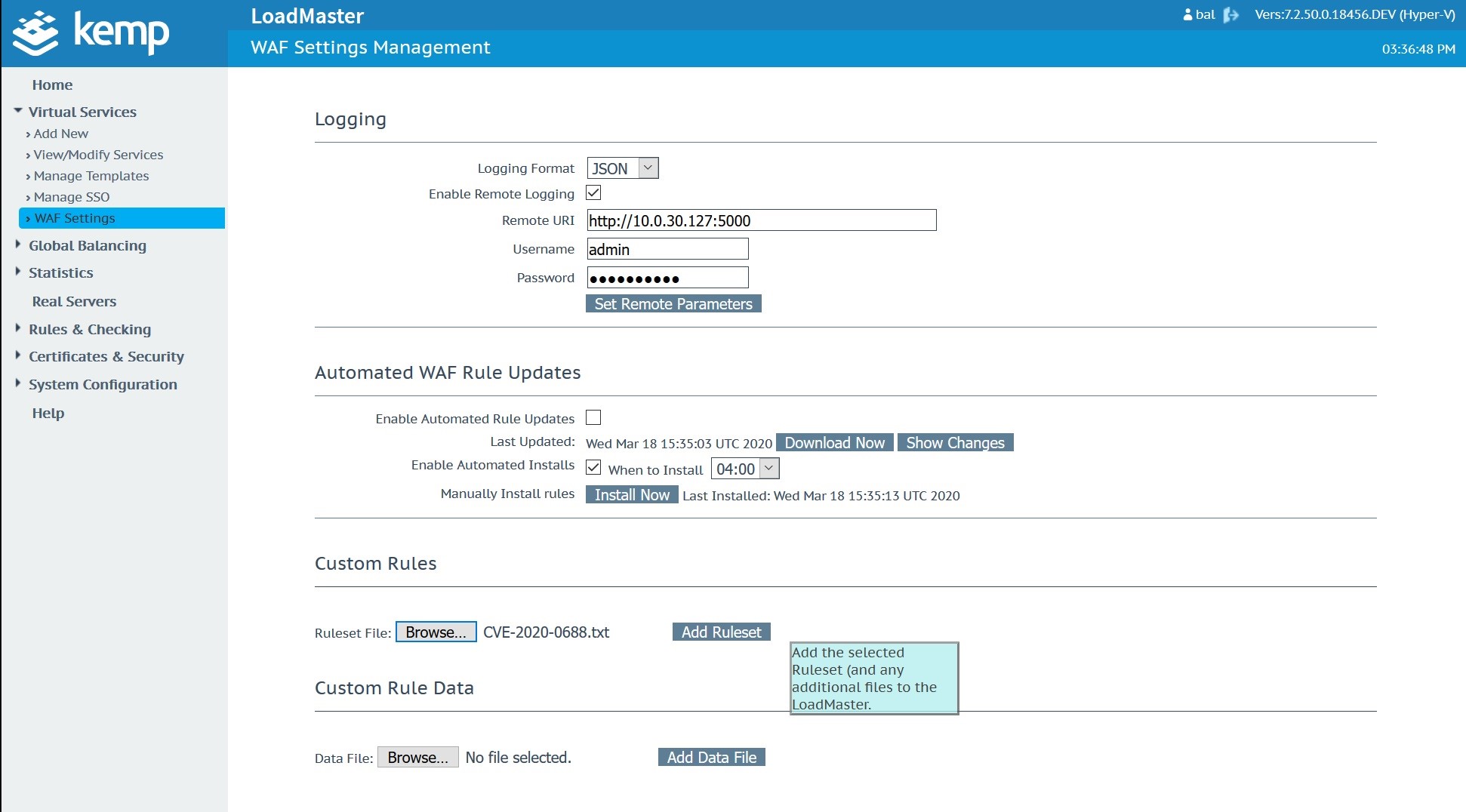
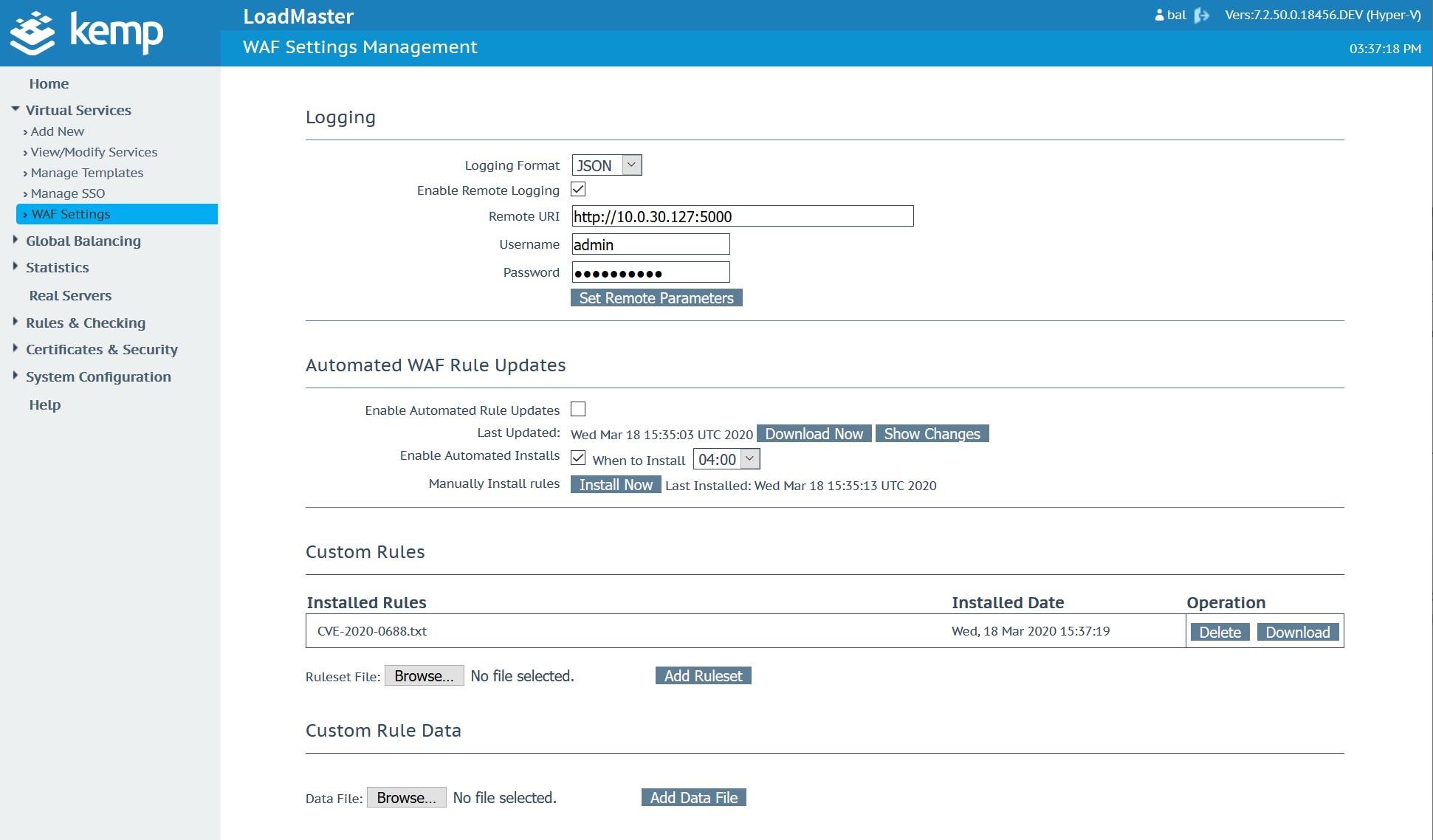
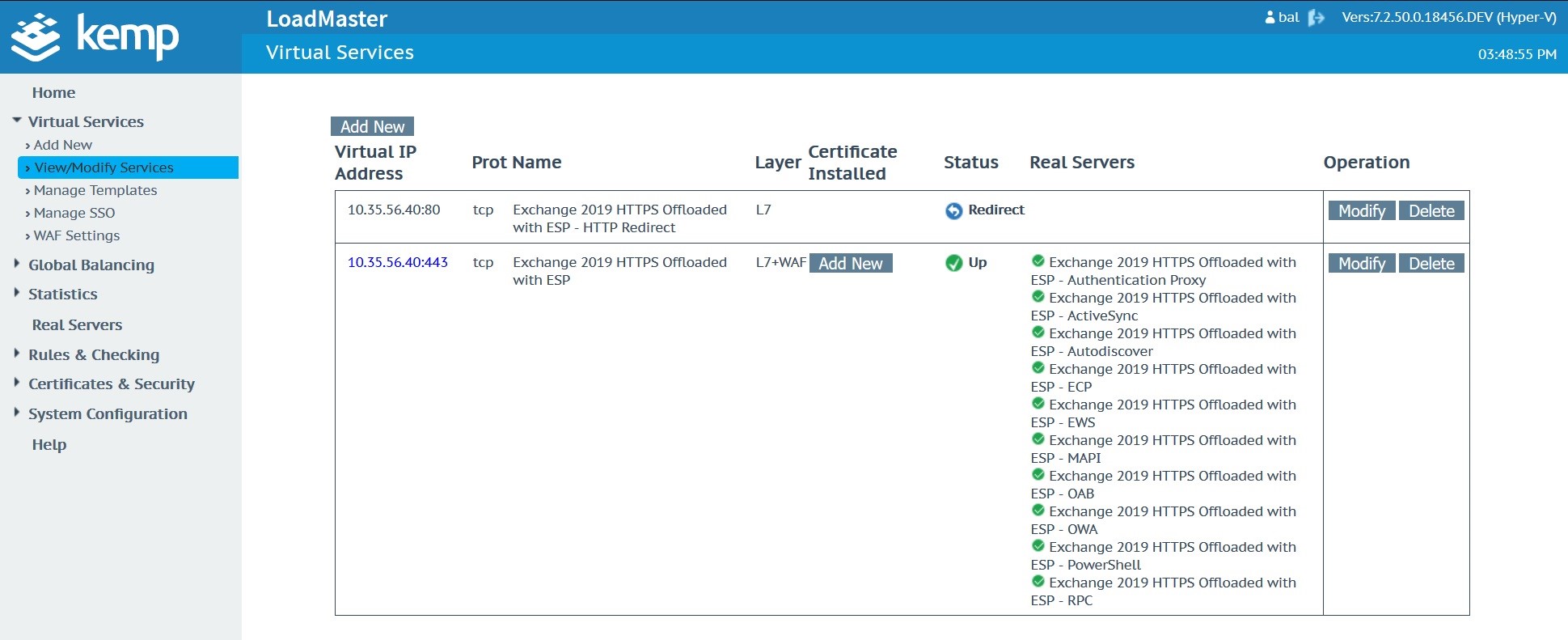
Once the custom WAF rule is uploaded and available, navigate to the Microsoft Exchange Virtual Service. In this case, the Microsoft Exchange Virtual Service was created with a Kemp Technologies Exchange 2019 template.
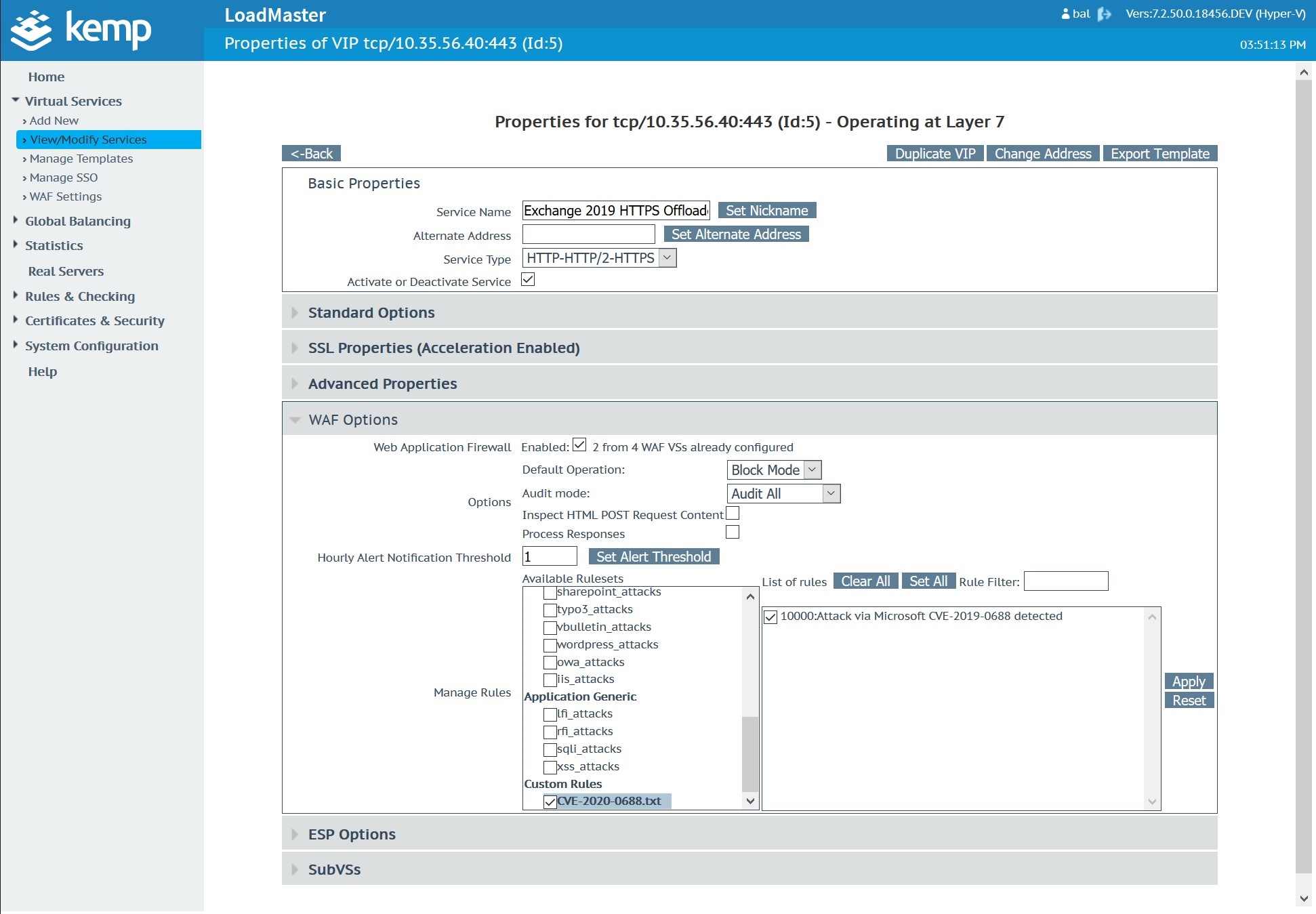
Expand the WAF Options, scroll to the bottom of the Custom Rules section and select the uploaded document.
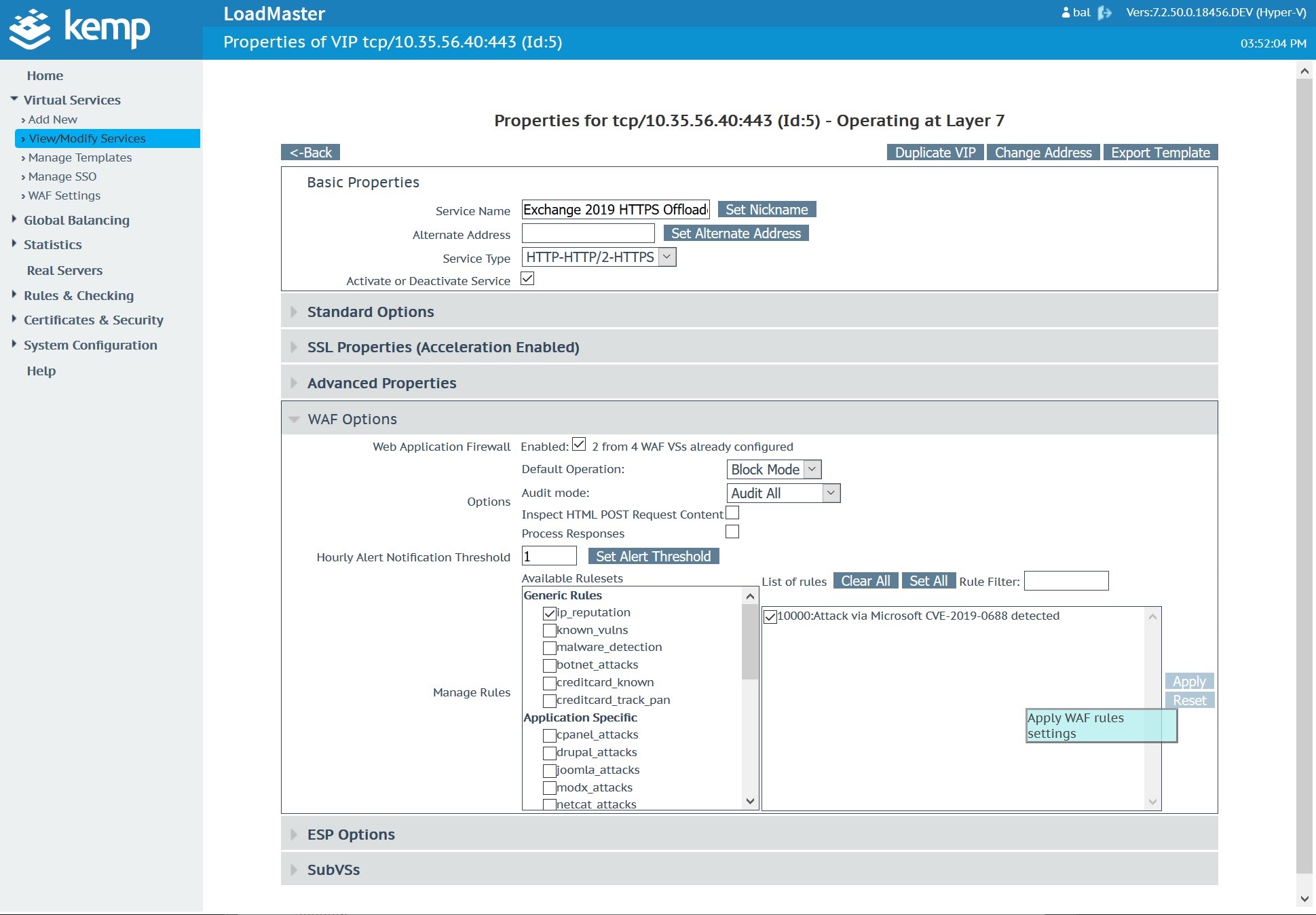
Click Apply to apply this rule to the Microsoft Exchange Virtual Service.
Additional information
For additional information about the discovered vulnerability: CVE-2020-0688 Microsoft Advisory Volexity Threat Research TrustedSec Blog
Based on our experience, Kemp provides an extremely flexible load balancing solution with the widest platform support in the industry, specifically for virtual and software deployments. A key part of our holistic application delivery strategy includes the mitigation of application-specific vulnerabilities. We continue to provide timely key security features and services that allows customers to enable secure access to web-based applications.
We’re committed to resolving security vulnerabilities carefully and quickly. If you think you have found a security flaw in a Kemp product, please inform us at securityalert@kemp.ax

David O'Connor
David O’Connor is a Product Manager in Kemp working in Limerick, Ireland. He holds a bachelor’s degree in Computer Engineering from University of Limerick. David has a telecoms background with previous roles in development, customer support and presales with a focus on product-market fit and creating tech products that customers love.
more from the author