How to do MFA with Google CAPTCHA using Kemp LoadMaster

This blog post is intended to provide technical guidance on how to deploy Multi-Factor Authentication (MFA) with Google Authenticator (CAPTCHA) using Kemp LoadMaster load balancer to a Microsoft Exchange backend application server(s). This will leverage the Kemp Edge Security Pack (ESP) standard functionality.
The blog post focuses on integration with Google Authenticator (CAPTCHA) using the HMAC-based Onetime Password algorithm using LinOTP via RADIUS.
More information on Google Authenticator is available here. More information on Google CAPTCHA v2 account is available here. More information on LinOTP is available here.
High Level Overview
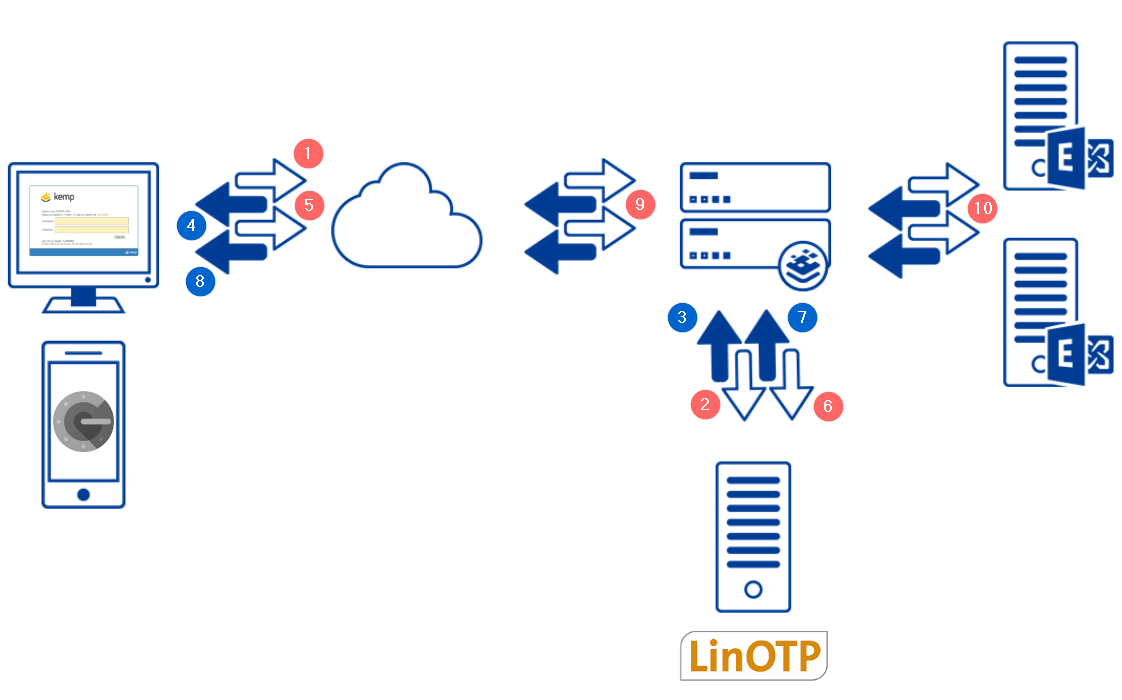
In the architecture above you can see a diagram of the components involved in this flow. These are described as follows:
- Client connects to their Exchange server. This is terminated on the Kemp LoadMaster load balancer. The Kemp LoadMaster Edge Security Pack (ESP) is configured to redirect the client to the Kemp authentication form.
- The Kemp LoadMaster proxies the clients credentials to LinOTP via RADIUS.
- LinOTP responds to the Kemp LoadMaster with an Access Challenge.
- The Kemp LoadMaster presents the client with a second login page.
- The client opens their Google Authenticator App and enters their Second Factor Token.
- The client enters their Second Factor Token to the Kemp LoadMaster second login page.
- The Kemp LoadMaster sends the Second Factor Token to the LinOTP server.
- In the successful case, the LinOTP server responds with an “Access Accept” response.
- The client is now redirected back to the original URL which contains an LMDATA Authentication Cooke.
- The Kemp LoadMaster forwards the request to the Exchange Server by POSTing the clients credentials.
Configuration RequirementsThis section outlines the configuration requirements to enable this functionality:
- LinOTP server (Alternatively any MFA authentication server like RSA can be used)
- Google Captcha account, available here
- Microsoft Exchange backend with OWA configured for “Forms Based”
- Kemp LoadMaster with Enterprise / Enterprise Plus subscription (or Trial license)
- Kemp firmware release v7.2.49 (or greater)
LinOTP Configuration This section outlines the LinOTP configuration that is required to support this:
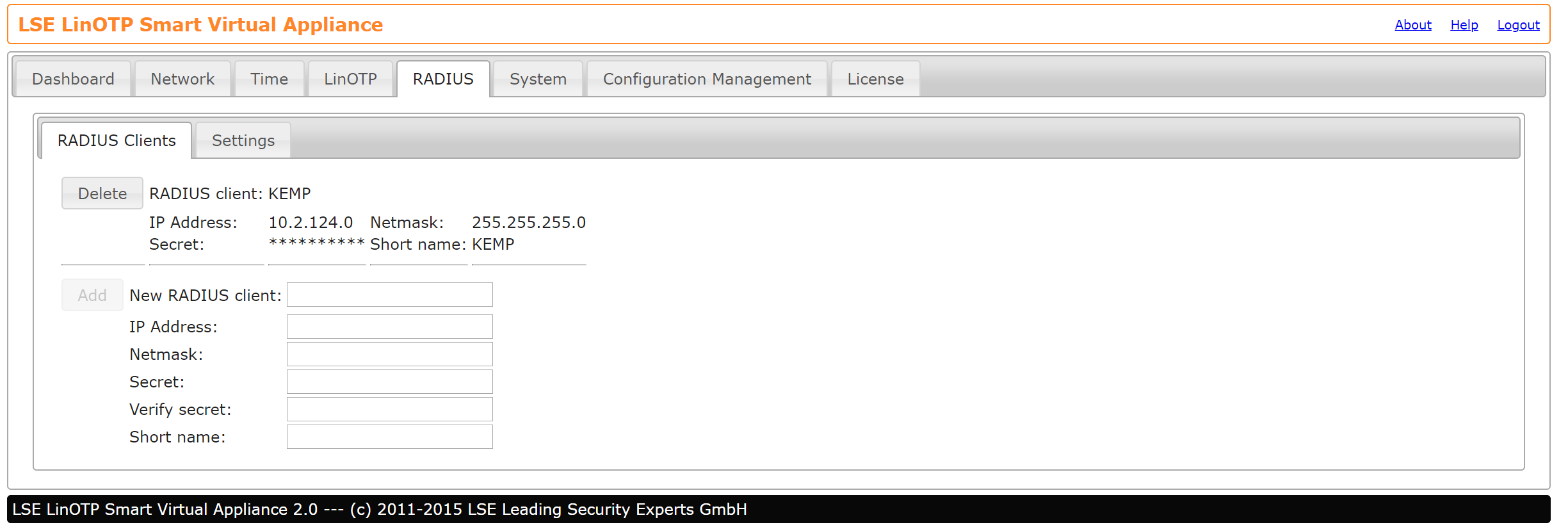
- To configure RADIUS clients, login to LinOTP under https://<<LinOTPServer>>:8443/config
- Configure the RADIUS client as shown below, with the LoadMaster credentials
- To enrol users, Login to LinOTP under https://<<LinOTPServer>>/manage
- Click on Enrol and select Token settings > Google Authenticator compliant. Fill in the appropriate sections including a pin that is statically configured for that user.
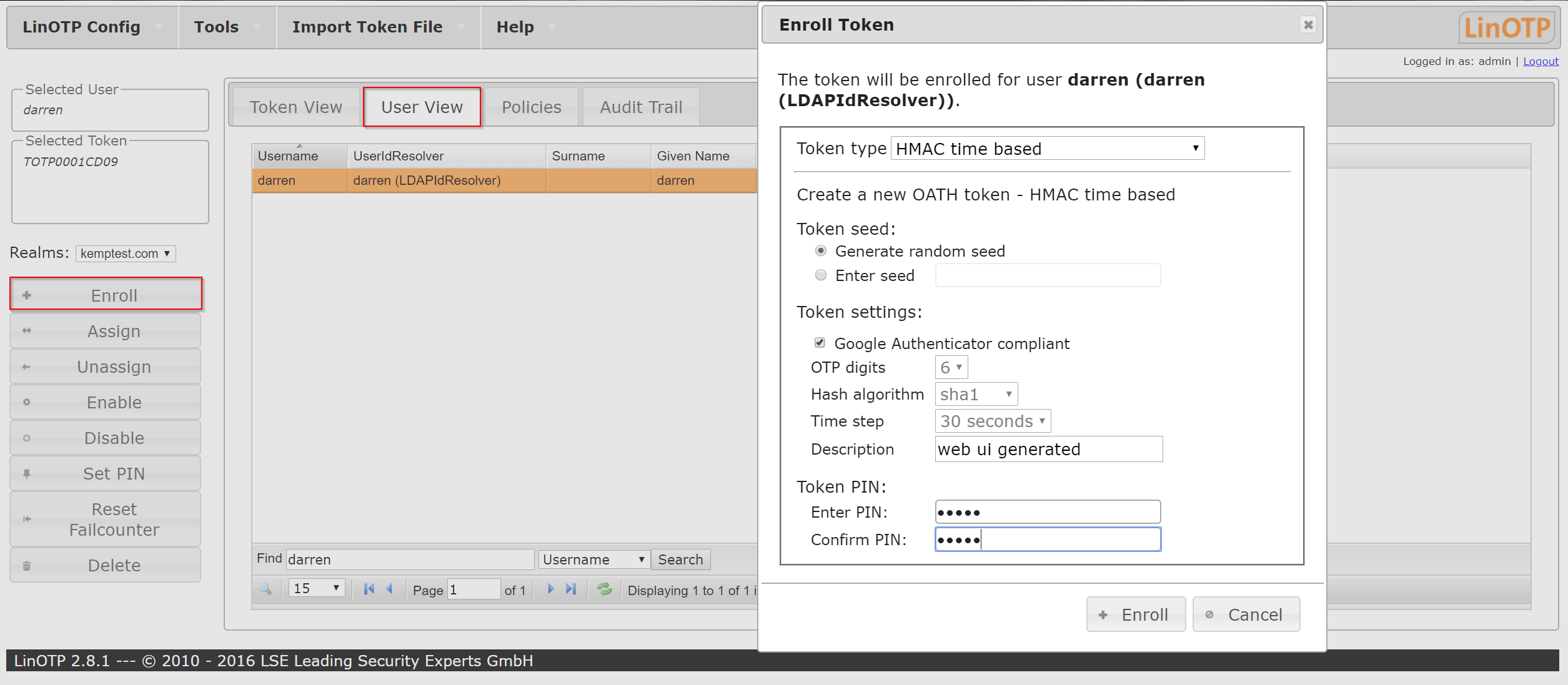
5. Using the Google Authenticator app to scan the 2D barcode that is presented.
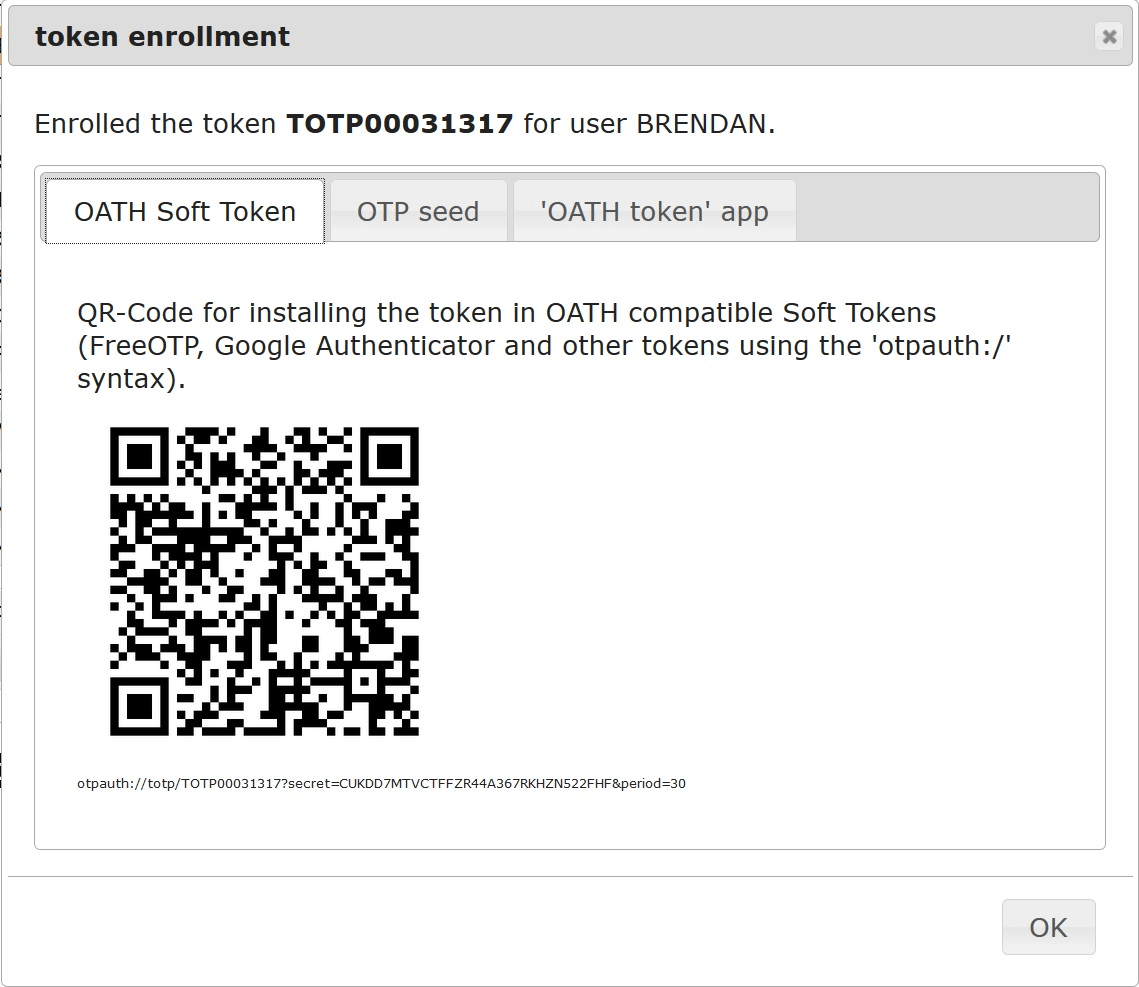
- This will create a token, for example TOTP0010CD19, which can be viewed in the ‘Token View’ tab of LinOTP and is also presented on the Google Authenticator Application also.
Kemp LoadMaster Configuration
This section outlines the Kemp LoadMaster configuration that is required to support this:
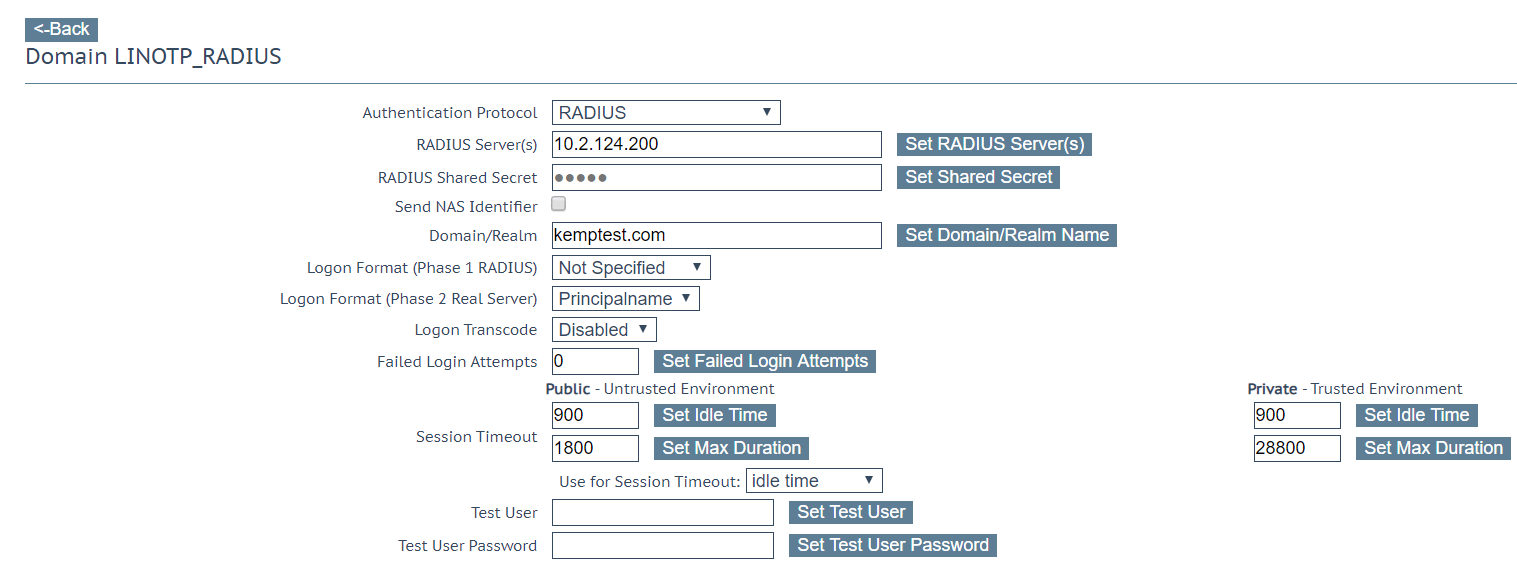
- To configure the LinOTP endpoint, go to Virtual Services > Manage SSO > New SSO
- Enter the details of the LinOTP RADIUS server
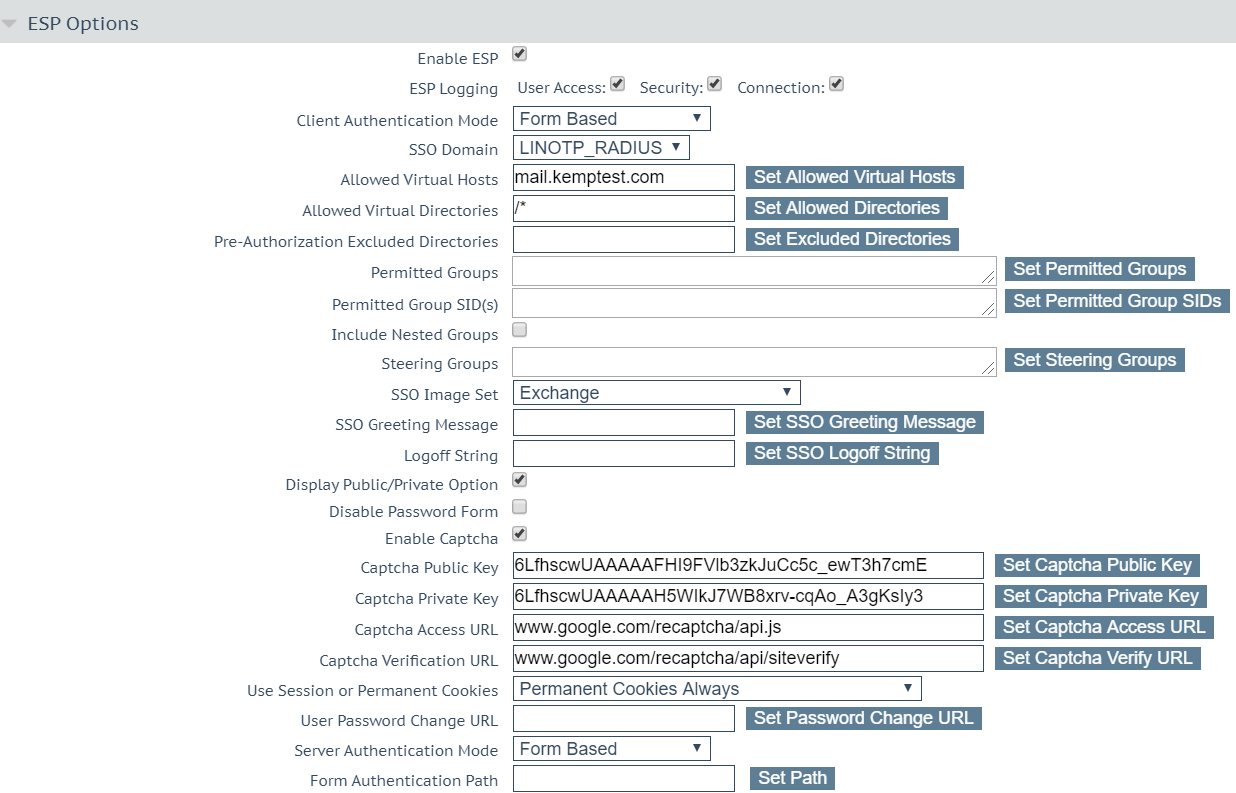
- To configure the Virtual Service, go to Virtual Service > ESP Options
- Enter the details of the CAPTCHA and the SSO Image Set configured to ‘Exchange’
Authentication with Google AuthenticatorThis section outlines the screens that user will be presented with as part of the workflow.
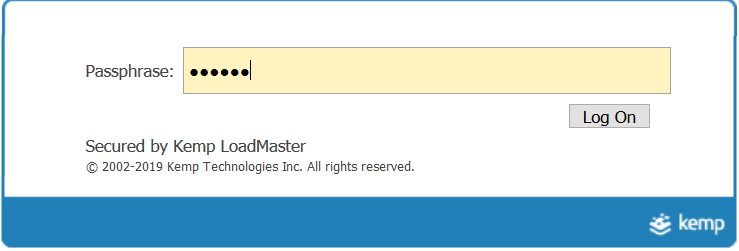
The Kemp LoadMaster will present the initial login page including the Google Authenticator CAPTCHA. The CAPTCHA presented will depend on how it has been configured in your Google account.
The Username / Password is that which has been configured on the LinOTP server.

Once the Username, Password and CAPTCHA are verified, the Kemp LoadMaster will request a pin. This pin is the 6-digit one-time password from your Google Authenticator Application.
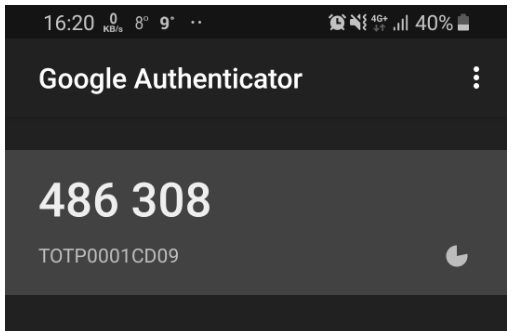
The pin will be verified by LinOTP and once successful will allow access to the Microsoft Exchange farm on the backend.

David O'Connor
David O’Connor is a Product Manager in Kemp working in Limerick, Ireland. He holds a bachelor’s degree in Computer Engineering from University of Limerick. David has a telecoms background with previous roles in development, customer support and presales with a focus on product-market fit and creating tech products that customers love.
more from the author