What is the OWASP Top 10?
The Open Web Application Security Project (OWASP) organization has been running since 2003. It publishes a top 10 list approximately every four years highlighting the most severe vulnerabilities and threats seen in real-world web application deployments. The 2021 release of the OWASP Top 10 is now available, and it replaces the previous 2017 version.
We’ve published many OWASP articles on the Kemp blog, including a comprehensive OWASP Top 10 series covering the 2013 release, updates for 2017, a five post series on the OWASP ModSecurity Core Rule Set (CRS), and how to use CRS with Kemp LoadMaster Web Application Firewall (WAF), and many more.
Kemp Sponsors the OWASP ModSecurity Core Rule Set
The OWASP ModSecurity Core Rule Set is an open-source project that delivers a valuable service to the web application community by maintaining a core defensive set of rules that anyone can deploy on top of the ModSecurity Engine. The LoadMaster WAF builds on ModSecurity, and Kemp is delighted to put our support behind the OWASP ModSecurity Core Rule Set project by being a Gold Sponsor.
CRS protects against the main vulnerabilities highlighted in the OWASP Top 10 and other threats outside that list. By maintaining the rules and making them available free of charge, CRS most certainly does provide the 1st Line of Defense that their tagline proclaims.
What’s Changed in the 2021 OWASP Top 10?
The 2021 edition of the Top 10 list has changed quite a lot from the previous one. The infographic below shows the changes (source: OWASP Top 10 2021 Introduction).
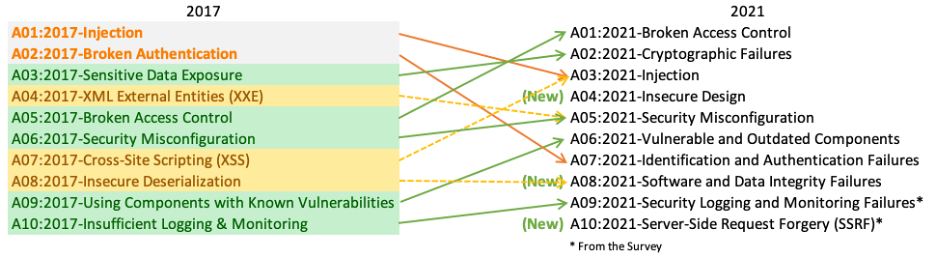
The new release includes three new categories of vulnerability. Four existing categories from the 2017 list have had naming or scoping changes, and consolidation has combined some into existing entries. The OWASP team has also changed some names to reflect the risk better. For example, the new A02:2021-Cryptographic Failures entry is a renamed version of the A03:2017-Sensitive Data Exposure entry. This change highlights that data exposure is overwhelmingly due to a cryptographic failure on data at rest or in transit over a network.
Full summaries and technical dives into each of the 2021 Top 10 entries are available on the OWASP Top 10 – 2021 website. Rather than repeat that excellent information here, we’ll direct you to the OWASP site to read about the new list. However, we will say a few words about the data collection and methodology that went into compiling the 2021 Top 10 list.
The Methodology Behind the OWASP Top 10 – 2021
The OWASP team built the 2021 version of the Top 10 on top of more web application data submissions than ever. Over 500,000 web applications were submitted and scanned for vulnerabilities during the revision period for the Top 10. The team selected eight of the latest top 10 entries based on this data analysis.
OWASP selected the other two entries (numbers 9 & 10) after analyzing the returns of an OWASP Top 10 security community survey. Analysis of existing applications is somewhat looking into the past and addressing well-known threats. The survey data has more up-to-date information from security professionals and developers about emerging threats that have not yet made it into testing tools.
Check Out Kemp LoadMaster WAF & CRS
The OWASP Top 10-2021 list is a good starting point for all organizations that want to bolster their web application security. Using the CRS to protect against the vulnerabilities on the list provides cyber defenders with a ready-made set of rules to deploy
Kemp LoadMaster with WAF is the ideal way to deploy the CRS protections, which is why we are delighted to be a Gold Sponsor for CRS.
Visit the Kemp Web Application Firewall page to find out more and to download your 30-Day Free Trial.

