Featured Stories
Latest Stories
OWASP Top Ten Series: Cross Site Scripting
Cross Site Scripting (XSS) attacks are a type of injection attack. XSS is probably the most common type of malicious attack after code injection. They are certainly the most common …
October 13, 2015
OWASP Top Ten Series: Security Misconfiguration
Security Misconfiguration Modern web applications are built from many different parts. There are front end components such as a web browser, a desktop application with embedded web viewer, or increasingly …
August 11, 2015

OWASP Top Ten Series: Broken Authentication & Session Management
Broken Authentication and Session Management Securely authenticating users, managing their sessions when connected, and ensuring proper logout when the sessions end are essential activities when delivering web applications. As are …
July 17, 2015
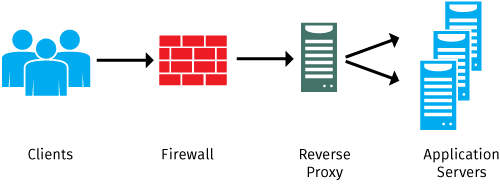
Reverse Proxy for Skype for Business
Microsoft Skype for Business is a robust and easy to use collaboration platform. It provides employees with tools that allow them to collaborate from anywhere, at any time, on any …
June 10, 2015

Experience the KEMP Advantage – Riverbed SteelApp Replacement Program
KEMP Technologies’ award-winning LoadMaster range of Load Balancers & Application Delivery Controllers, enhance the resilience and performance of any network in which they are deployed. We believe more organizations should …
June 4, 2015

Announcing the New FREE LoadMaster™ Application Load Balancer
A free version of our popular VLM application load balancer is now available for unlimited use, making it easy for IT developers and open source technology users to benefit from …
March 3, 2015

La seguridad en un balanceador de cargar, HA ( alta disponibilidad ) y Reverse Proxy
Un Proxy inverso es un elemento de vital importancia dentro de las infraestructuras de aplicaciones para proporcionar una capa adicional de seguridad para las instancias del servidor mediante la recuperación…
January 13, 2015

WAF – Web Application Firewall 101
Traditional network firewalls placed in front web servers offer protection by limiting webserver access to the HTTP and HTTPS protocol ports – normally port 80 and 443. This approach prevents …
November 25, 2014

Dude, Where’s My Reverse Proxy?!
In the past the “Reverse Proxy” shown in the diagram below would have said “TMG”, Microsoft’s Threat Management Gateway product. With that option no longer available a lot of people …
August 19, 2014


