Today, we are going to provide technical guidance on how to migrate your Citrix Netscaler Exchange Virtual Server using NetScaler AAA Session Policy Virtual Server, to a Kemp Exchange Virtual Service using Kemp’s Edge Security Pack (ESP). This is a valuable technical guide if you currently use Citrix Netscaler products and are interested in learning about migrating an advanced service that includes AAA Session Policies. In this walk-through, we are using our Exchange OWA service with Forms Based Client Side and Forms Based Server Side.
Architecture/Design Requirements
- Microsoft Exchange backend with OWA configured for “Forms Based”
- Kemp LoadMaster with Enterprise or Enterprise Plus support package (or Trial license)
Terminology
Citrix Netscaler uses different terms for some functions and technologies. Below is a chart that maps the Netscaler terms with what is used within Kemp documentation.
| Citrix Netscaler | kemp LoadMaster |
| Virtual Servers | Virtual Services |
| SSL Profile | SSL Acceleration |
| Content Switch Policies | Content Rules |
| Monitors | Health Checks |
| AAA Virtual Server Policies | ESP |
| Service Group | Sub Virtual Service |
| Group Member | Real Servers |

Template
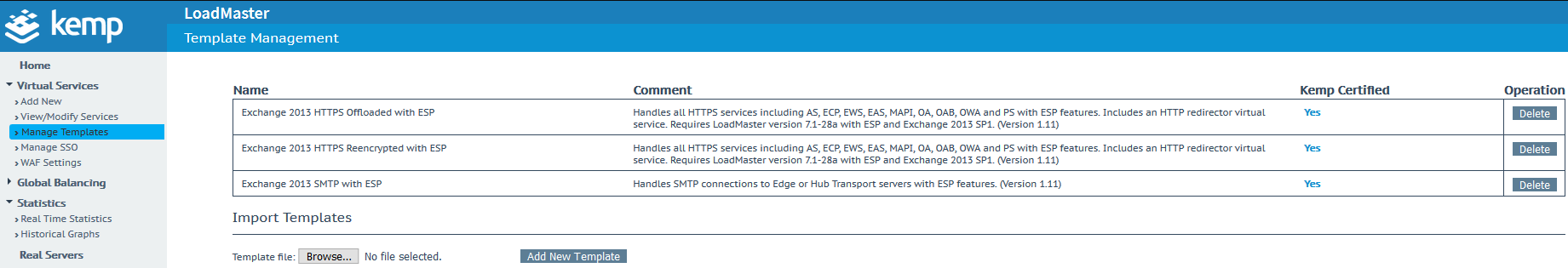
Kemp provides an Exchange configuration Template which comes preconfigured with all the required configuration parameters. This makes the Kemp configuration easy since only customer unique information needs to be provided (IP addresses, server names, etc.). To download our popular application Templates, please navigate here. Select the corresponding Template depending on your Exchange version. In this case, we have chosen Exchange 2016.
On the Kemp load balancer, to import the template, navigate to Virtual Services > Templates > Browse > Import on the left-hand menu.
Exporting your Netscaler SSL Certificates
On your Citrix Netscaler navigate to: Traffic Management > SSL, click on Manage Certificates / Keys / CSRs.
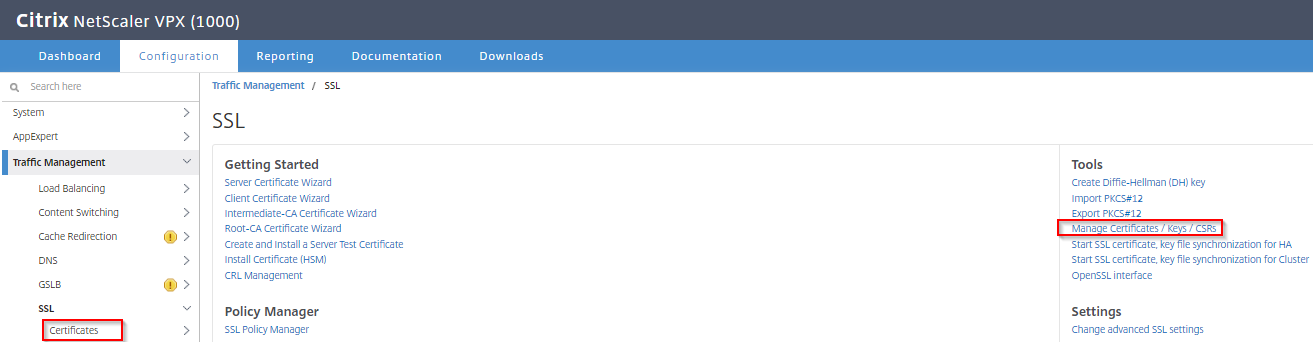
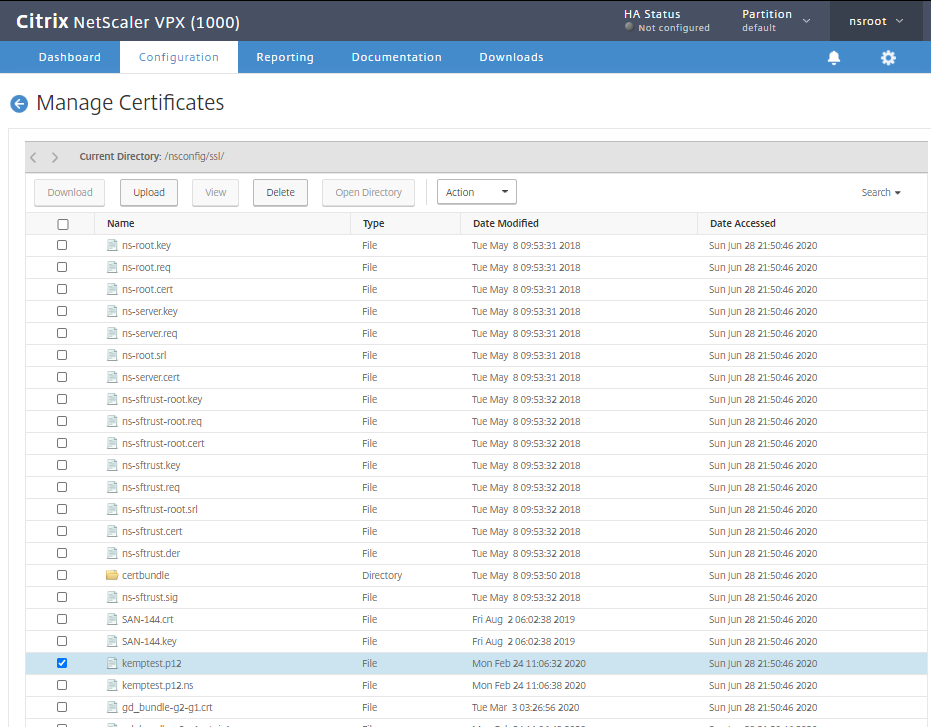
Select your SSL Certificate and Download. In most cases this will be a PFX.P12 certificate, but it could also be in other formats such as “.crt” with .pem or .key.
Importing your Netscaler SSL Certificate
On your LoadMaster Navigate to Certificates & Security > Import Certificate.
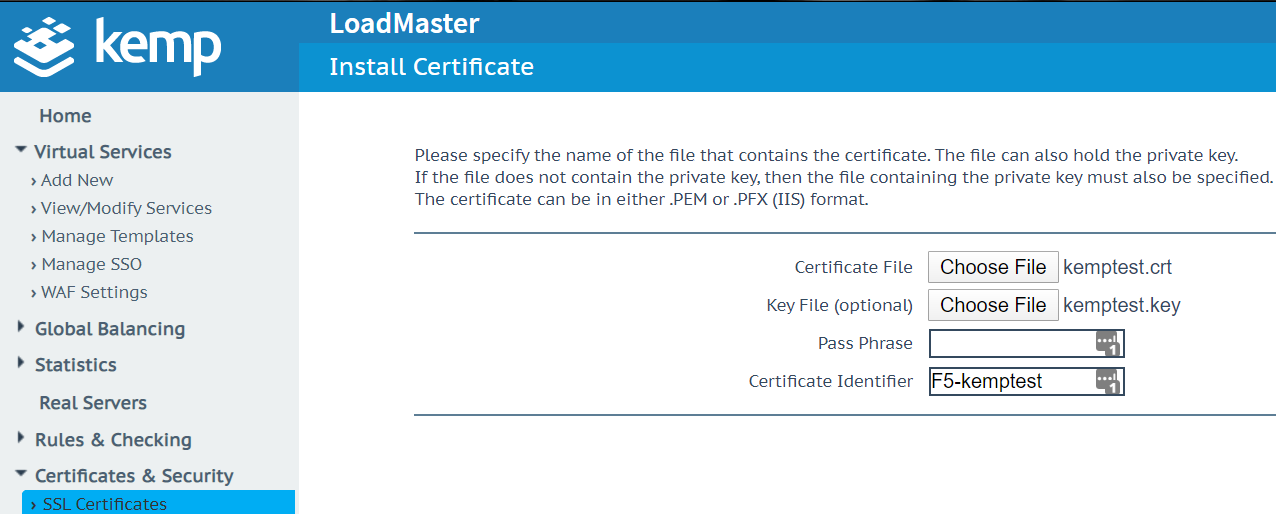
Select your PFX certificate and enter your Pass Phrase
If you have your Private Key and CA Cert as separate files, select your .crt/.pem file,and for your Private Key file select your .key/.pem file.
Content Switching Policies Versus Content Rules
Both Netcaler & LoadMaster can direct traffic to a specific Exchange Pool by looking at the HTTP URL. Netscaler achieves this using Content Switching Policies and a Content Switching Virtual Server, whereas Kemp achieves by using Content Rules which are assigned to a Sub VS.
Netscaler OWA Content Switch Policy
- Create and configure Content Switching Virtual Server
- Create Content Switching Actions
- Create Content Switching Policies
- Bind Content Switching Policies
Expression example
HTTP.REQ.URL.CONTAINS(“/owa”)
This function is much more easily achieved on kemp by creating a simple Content Switching rule.
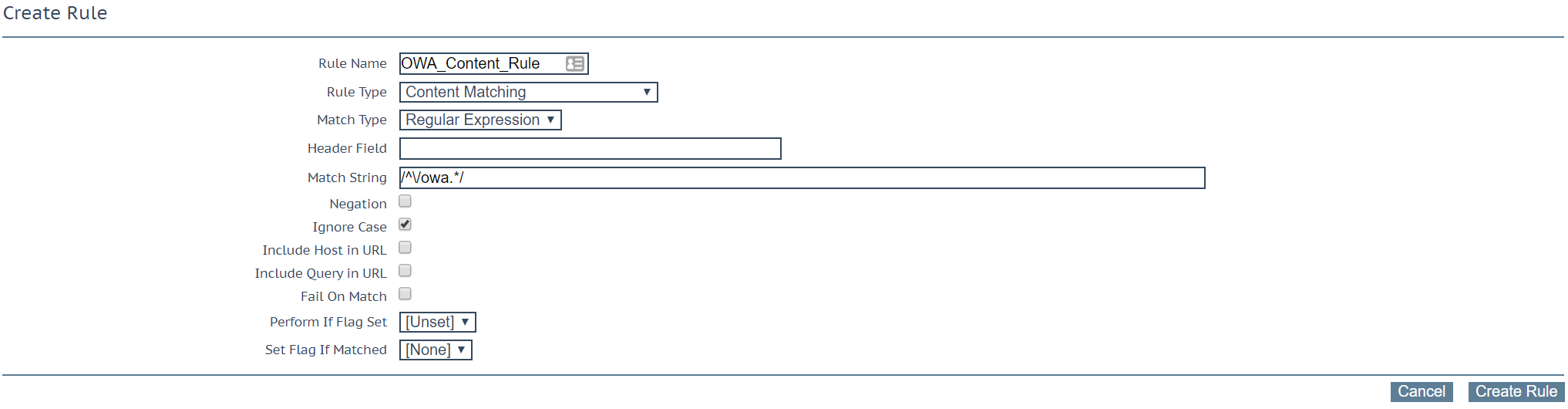
All Exchange Content Rules come as part of the template and are already associated to each Exchange Pool such as OWA & ECP. More information on Content Rules can be found here.
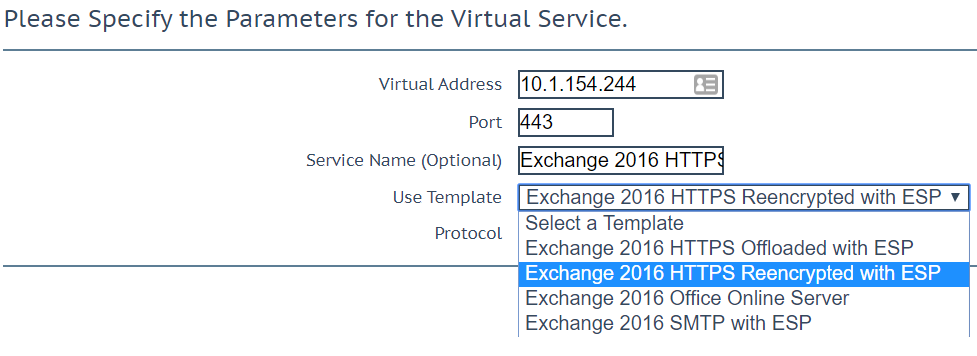
Virtual Service Configuration
Navigate to Virtual Services > Add New > Add IP > User Template > Select Exchange 2016 HTTPs Reencrypted with ESP.
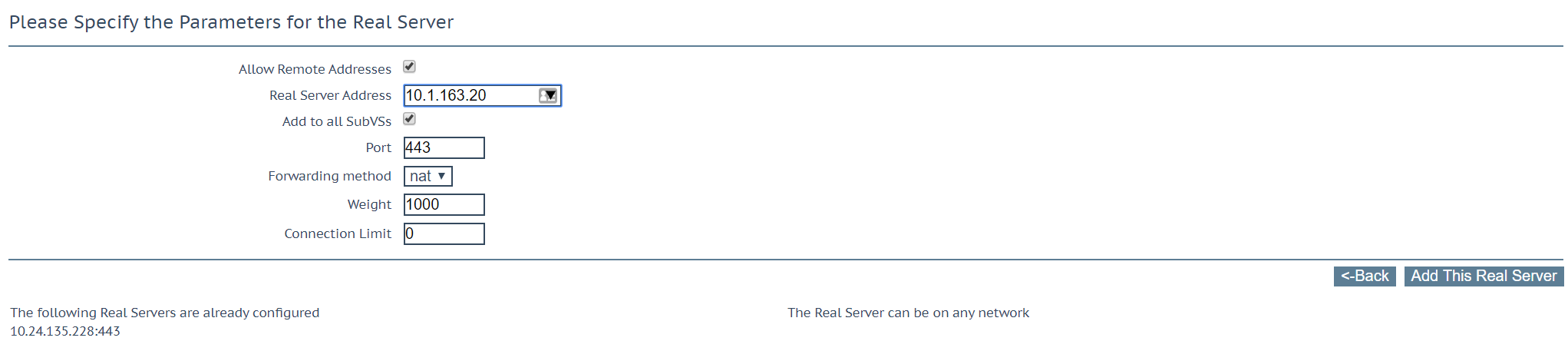
Adding Real Servers to Sub VS
Navigate to Virtual Services > Modify Sub VS > Real Servers > Add Real Server
Check “Add to all SubVS”. This will add your server to all Exchange Sub VS such as OWA & ECP.
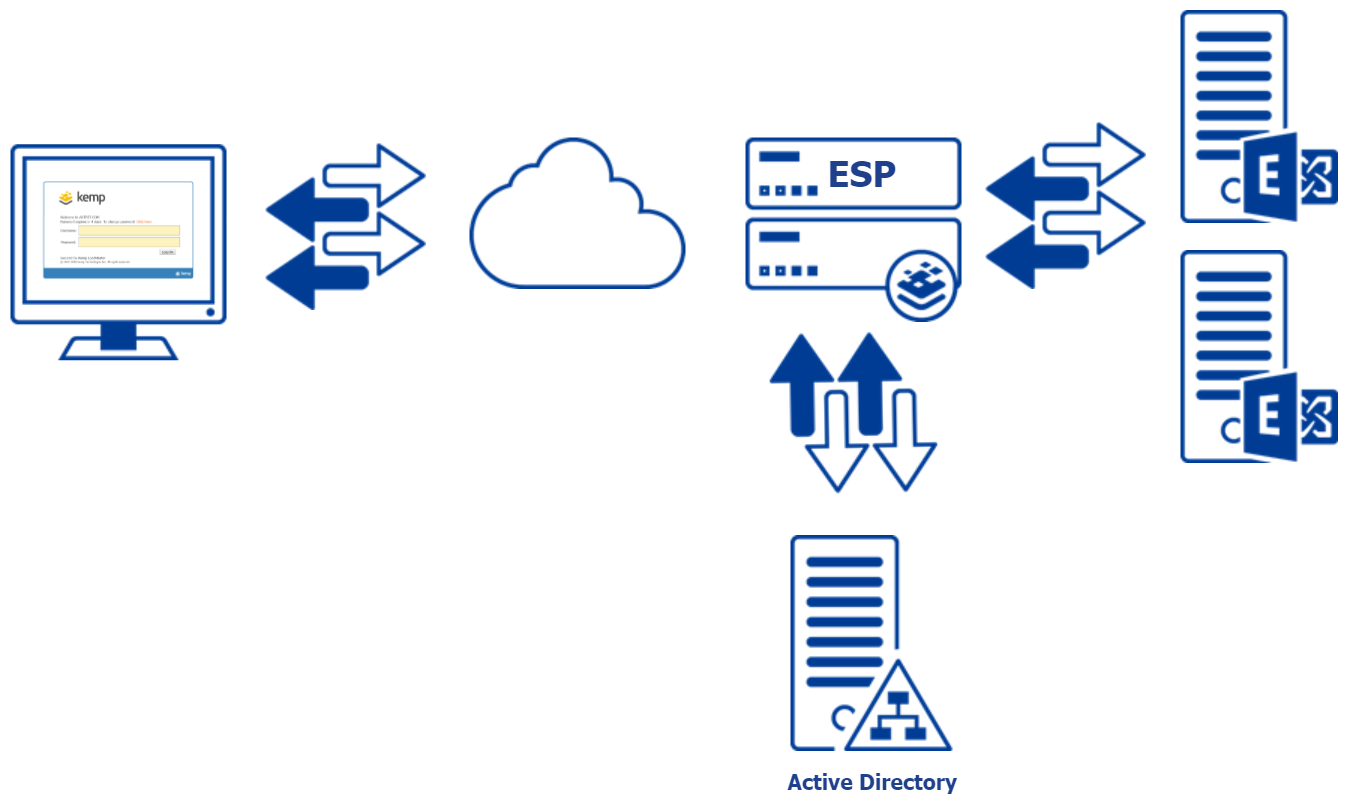
Netscaler Authentication Policy & kemp SSO Manager
Within the Netscaler environment, you will define a Session Policy which will bind to an AAA Authentication VServer which will eventually Bind to your Exchange Virtual Server. Kemp LoadMaster uses similar more easily configurable logic where you will create a Single Sign On (SSO) Profile and associate it with your Virtual Service or Sub VS.
ESP High Level Overview
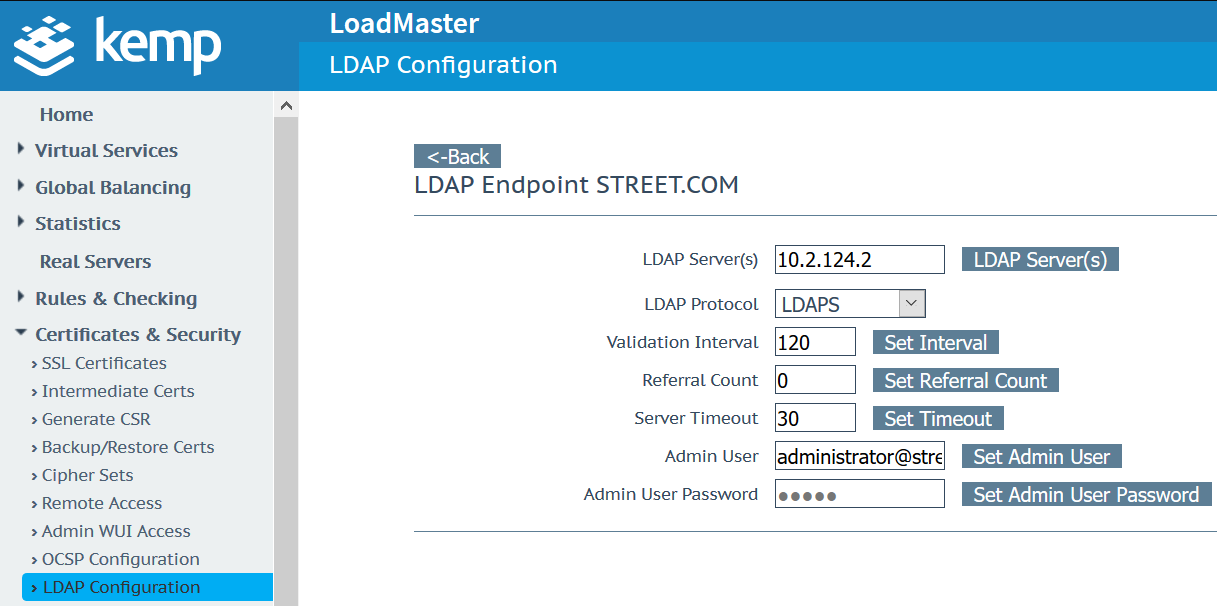
Create LDAP Endpoint
Certificates & Security > LDAP Configuration > Add new LDAP Endpoint
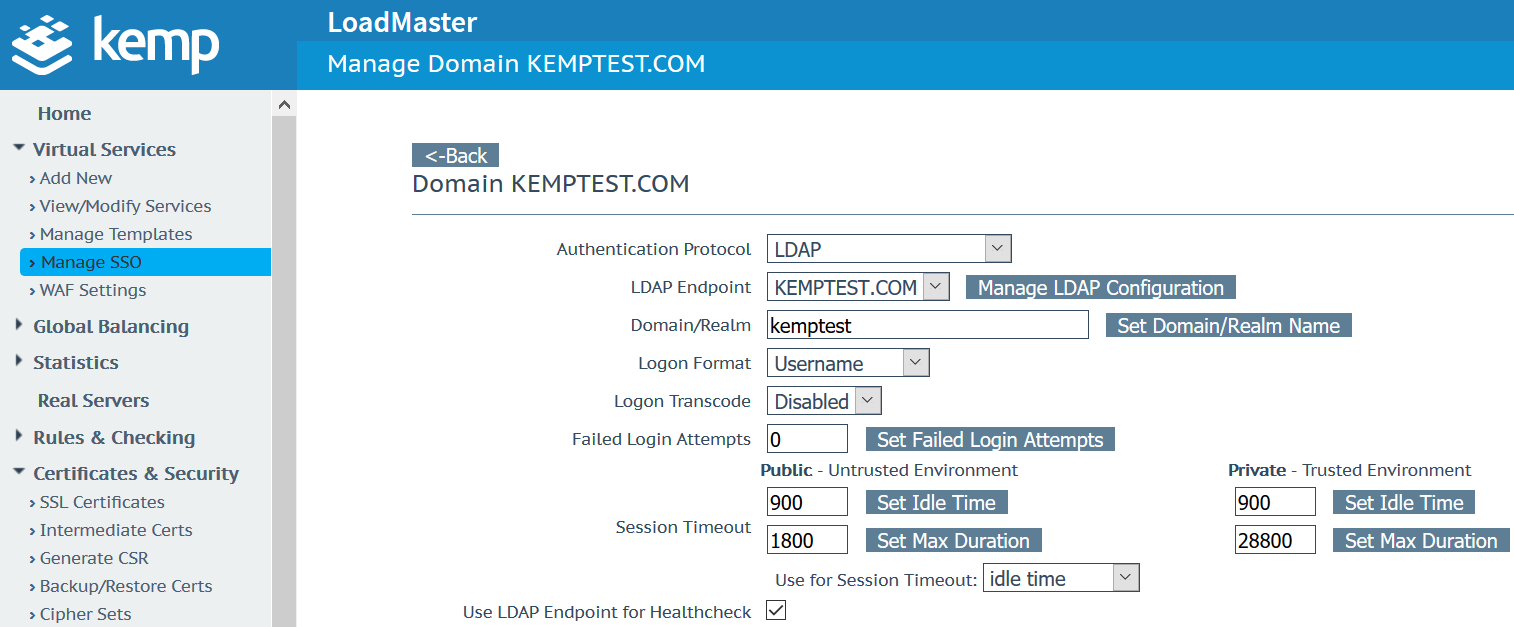
Create SSO Profile
Navigate to Virtual Services > Manage SSO > Add new Client Side Configuration
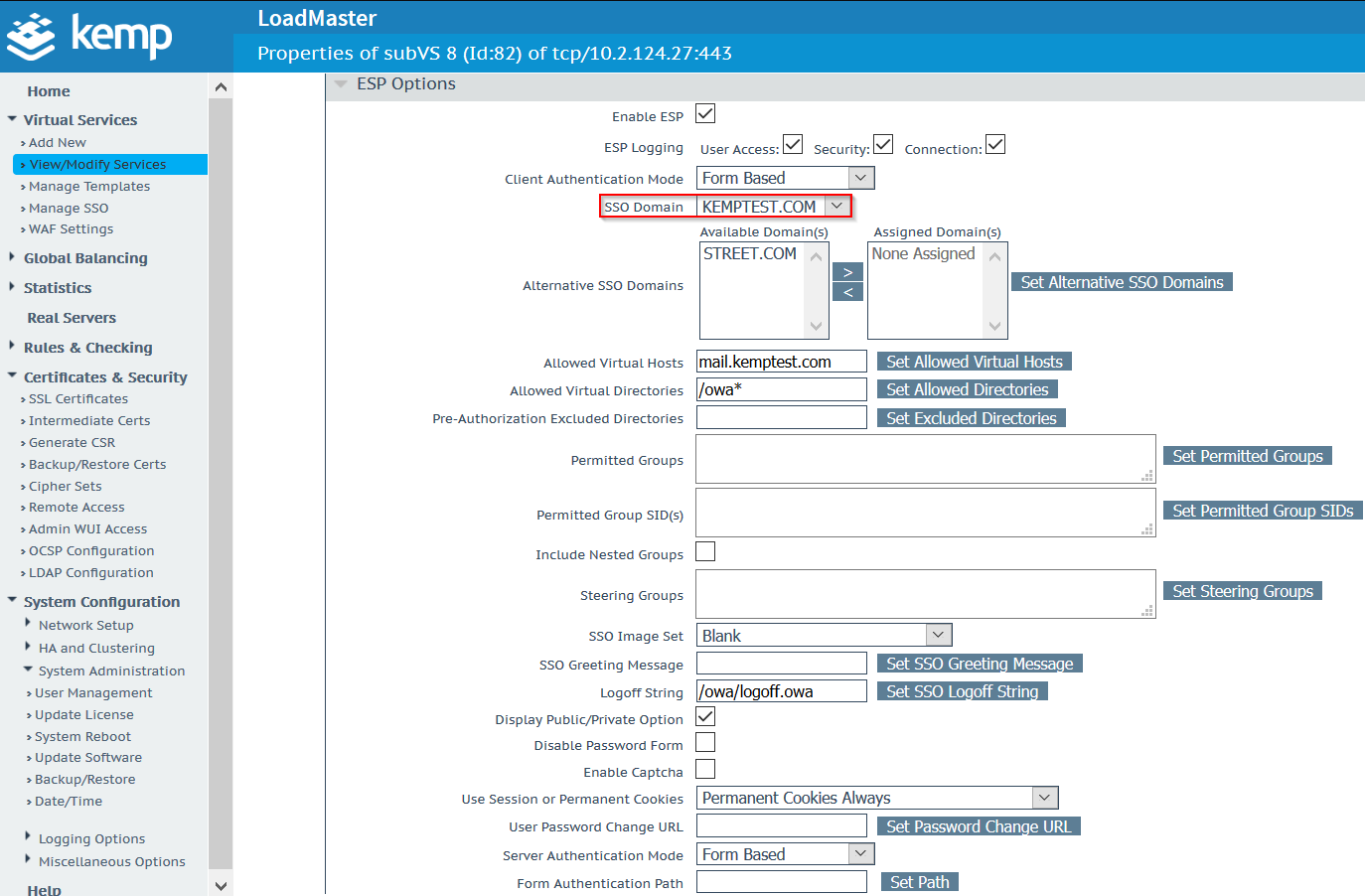
Associate SSO Profile to Sub VS
Navigate to Virtual Services > Modify > LM_auth Sub VSand OWA Sub VS and assign your previously created SSO Profile “kemptest.com”.
You will also be required to configure your Virtual Host to your FQDN. e.g, “mail.kemptest.com”.
Finishing and Testing the Migration
Once complete, you should be able to connect to the newly created Virtual Service using your Exchange client and access the service on the Kemp load balancer in the same way you did with your Citrix Netscaler load balancer. All of the Netscaler functionality has been migrated to the Kemp solution delivering an optimal application experience (AX).
Advanced Configuration
If you would like to implement an multi-factor authentication (MFA) solution please see this blog. For additional information on specific ESP Exchange Options, please see this Knowledge Base article.
Citrix Virtual Apps & Desktops
If you are also using Netscalers Gateway feature to proxy your external Virtual Apps & Desktop connections, please see our configuration guide in how to achieve this.

