
Flowmon
Visualize Network Traffic, Identify Issues & Prevent Cyber Incidents
Reduce risk and improve your resilience across your on-prem, hybrid and cloud with intelligent network visibility and security monitoring.
Protect your business from
modern threats

Detection
Uncover ransomware attacks, unknown threats and early incident of compromise before they can impact your business.

Threat Hunting
Analyze malicious activity and investigate the root cause with a state-of-the-art solution based on AI & ML.

Response
Leverage response in autonomous way to enhance containment and eradication of cyber threats.

Forensic Analysis
Collect, store and retrieve all network security data to deep analysis for better cybersecurity resilience.
Control your network with full
visibility & decisive Intelligence
Complete Insight
Gain comprehensive visibility into your entire hybrid & cloud environment. Get a holistic overview of your network with detailed insights.
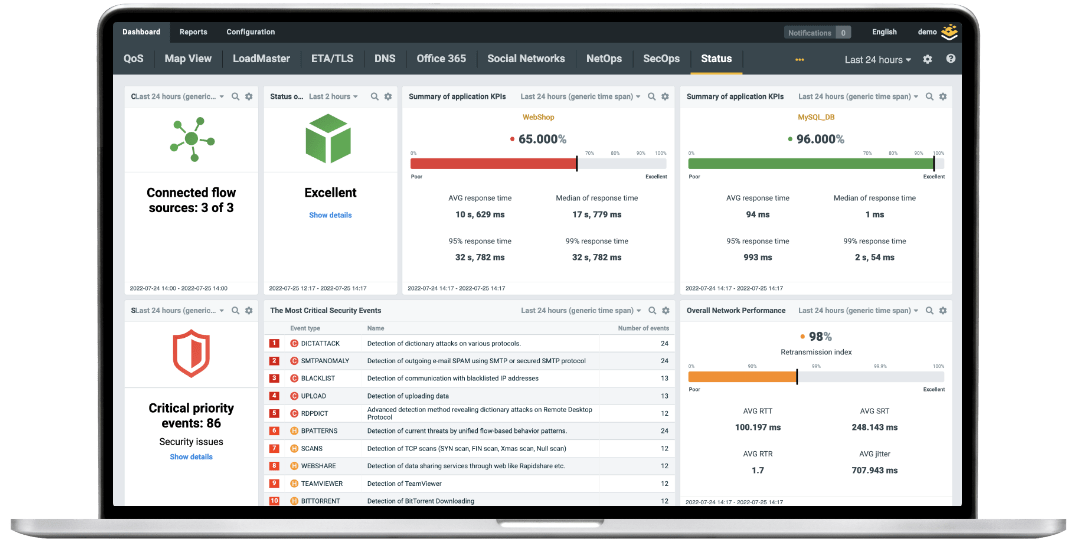
Performance Indicators
See performance degradation and distinguish between delays caused by the network itself and delays caused by applications and services.
Troubleshooting & Analysis
Quickly find the root cause of any network & security failures with deep data granularity and suggestions for remedial action.
Indispensable Anomaly Detection
Automated analysis of user and network behaviour for recognition of advanced threats and operational issues.
Flowmon Named Technology Leader in Network Detection and Response
Released in 2022, the SPARK MatrixTM report conducted by Quadrant Knowledge Solutions provides market insights, competitive evaluation, and vendor rankings to better understand the capabilities of different solutions in the network detection and response (NDR) market. In Customer Impact and Technology Excellence they awarded Flowmon's NDR the highest ranking of Technology Leader.
Get the report
Results first

“The installation of Flowmon is very simple and intuitive. Thanks to Flowmon, we are provided with network visibility that we previously lacked. As a consequence we can identify the causes of network issues easier than ever before. The solution also allows us to design the proper capacity of our network. We plan to enforce network monitoring solution deployment across all 11 group offices and 20 facilities.”
Operations Network Engineer at SEGA
Technology trusted by your peers
 Rated 4.9/5
Rated 4.9/5
Request free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial today