In the past the “Reverse Proxy” shown in the diagram below would have said “TMG”, Microsoft’s Threat Management Gateway product. With that option no longer available a lot of people are scratching their heads and wondering what to do. This blog post aims to answer all your reverse proxy and TMG replacement questions.
The diagram below shows the architecture of Lync 2013’s Mobility Service and should be a fairly familiar topology for anyone that’s deployed a publicly accessible Microsoft workload in the past.
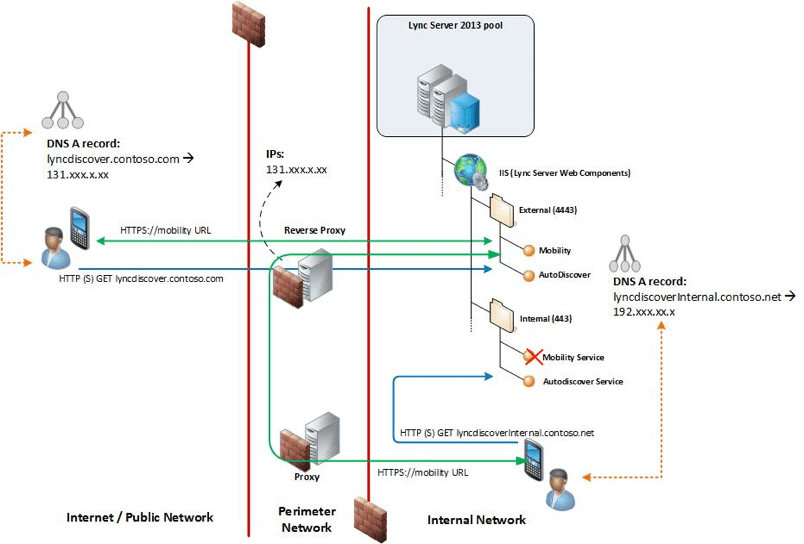
Source: http://technet.microsoft.com/en-us/library/hh690030.aspx The diagram above shows the architecture of Lync 2013’s Mobility Service and should be a fairly familiar topology for anyone that’s deployed a publicly accessible Microsoft workload in the past. In the past the “Reverse Proxy” shown in the diagram below would have said “TMG”, Microsoft’s Threat Management Gateway product. With that option no longer available a lot of people are scratching their heads and wondering what to do. This blog post aims to answer all your reverse proxy and TMG replacement questions.
Source: http://technet.microsoft.com/en-us/library/hh690030.aspx
What is a Reverse Proxy?
The term reverse proxy is a little bit like the term “cloud”. If you ask three people what it is you’ll get four and a half answers! Is it a firewall? A router? A load balancer? If it’s not clear to you, don’t worry, you’re not alone.
The challenge of understanding what reverse proxy actually is often comes from thinking of it as a specific device or product when in fact it is a network function much like switching or routing. With this way of thinking in mind it becomes easier to understand why many different products and devices can perform the role of reverse proxy.
Let’s begin with a simpler question though –what is a proxy? You may not have noticed but the Lync diagram shown earlier contains both so what’s the difference? In computer network terminology a proxy is any system that mediates connections between two systems (usually a client and a server). Often, one entity is in a trusted zone and the other in a less trusted or untrusted zone. The client sends its request to the proxy and the proxy forwards it to the server, the server sends the response to the proxy and the proxy returns it to the client. Nice and simple.
So where does the “reverse” in reverse proxy come from? This is where things start to get a little bit fuzzy.
A forward proxy is a proxy configured to handle requests for a group of clients under the local Administrators control to an unknown or arbitrary group of resources that are outside of their control. Usually the word “forward” is dropped and it is referred to simply as a proxy, this is the case in Microsoft’s topology. A good example is a web proxy appliance which accepts web traffic requests from client machines in the local network and proxies them to servers on the internet. The purpose of a forward proxy is to manage the client systems
A reverse proxy is a proxy configured to handle requests from a group of remote or arbitrary clients to a group of known resources under the control of the local Administrator. An example of this is a load balancer (a.k.a. application delivery controller) that provides application high availability and optimization to workloads such as Microsoft Lync, Exchange and SharePoint. The purpose of a reverse proxy is to manage the server systems.
Everything after that is just details specific to the situation and the product but not part of the definition of a reverse proxy. Having the role of reverse proxy is important for delivering a lot of other network services but it isn’t what defines a reverse proxy. For example in Lync there is a requirement for Port Address Translation, external clients connect on port 443 and the reverse proxy needs to make a connection to the Lync servers on port 4443. Security devices like web application firewalls act as reverse proxies in order to inspect application traffic for attacks and load balancers implement reverse proxying in order to optimise and control traffic as well.
Working at KEMP Technologies I often get asked the question “How do I turn on reverse proxying?” but the truth is it’s already on! As soon as you setup a Layer-7 virtual service on a KEMP Loadmaster application load balancer it’s already acting as a reverse proxy.
So how do I replace TMG?
The answer to this question depends on what you were using TMG for in the first place. TMG had a lot of security features and functionality but at KEMP we’ve found that many people were only using it for a few things with Microsoft UC and collaboration applications.. Two important functions that it provided for these workloads were:
1. Port Address Translation
2. Pre-Authentication of Connections
The first, Port Address Translation, is easy to provide using a wide range of network appliances and just involves listening on one port for clients whileforwarding these requests to servers on a different port.
If you need Pre-Authentication to validate user credentials against Active Directory before forwarding the request to you Application server then your choices are much more limited. There’s a new server role for Server 2012 R2 called Web Application Proxy which can provide both of these functions but also requires you to deploy AD FS. Additionally it requires an external mechanism to achieve high availability. Another option is the KEMP LoadMaster.
Our Product Management and Development team worked closely with the Microsoft community in enhancing our existing reverse proxy functionality to include additional services such as pre-authentication, SSO, dual-factor authentication, domain filtering, etc. Kerberos Constrained Delegation has recently been added to the list of supported authentication methods. These features are part of what’s known as the Edge Security Pack (ESP) and is a solution that helps Microsoft administrators to easily replace the functionality they were using in TMG.
A very common scenario was pre-authentication for Exchange Outlook Web App and port address translation for external Lync clients. The Edge Security Pack satisfies the needs of these scenarios and also features customizable Forms Based Authentication and support for RADIUS and 2 Factor Authentication using RSA tokens.
So if you’re looking at a topology that includes a “reverse proxy” stop and think about what services this device is required to deliver. This is how you’ll know what the right solution is for you. Many different solutions exist for reverse proxying but this is such a generic term that it may as well be “network device”. And if you’re wondering, “Dude, where’s my reverse proxy?!” chances are you already have at least one running somewhere in your network.
If not check us out at www.kemptechnologies.com and we’d be happy to help.

